Last Updated on 11 Aug 2025
Fraud and Cybersecurity Concerns in the Supply Chain Industry
Share in

Key Notes
•
Supply chain fraud losses are projected to exceed $6 billion globally in 2025.•
Over 40% of supply chain attacks originate from third-party vendors.•
1 in 3 organizations report insider fraud in supply chain operations.
Introduction to the Supply Chain Industry
The supply chain industry forms the backbone of global trade, encompassing everything from procurement and manufacturing to distribution and reverse logistics. With increasing digitization, cloud integrations, and AI-driven systems, modern supply chains are no longer just physical networks, they're complex digital ecosystems. These connected systems have created new efficiencies but have also exposed critical vulnerabilities. The shift to real-time tracking, digital documentation, and global vendor networks has opened the door to sophisticated cyber threats and fraud schemes. As threat actors increasingly target supply chains, proactive cybersecurity has become a necessity, not a luxury.
Market Size and Growth of the Global Supply Chain Industry
According to Grand View Research, the global supply chain management (SCM) market size was valued at USD 27.2 billion in 2022 and is expected to grow at a CAGR of 10.9% from 2023 to 2030. Over 80% of enterprises report at least partial digitization of their supply chain operations. Emerging technologies like IoT sensors, blockchain for logistics transparency, and AI-driven demand forecasting are accelerating growth. The sector spans across more than 200 countries with thousands of implementation partners, including 3PLs, 4PLs, SaaS providers, and freight-forwarding platforms. This widespread expansion has increased the attack surface significantly, making cybersecurity in the supply chain more critical than ever.
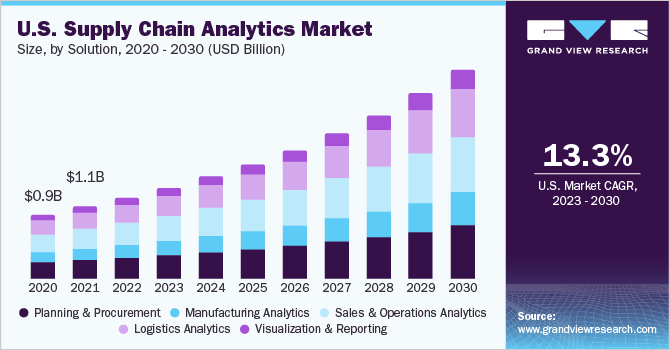
Source: Grand View Research
The Hidden Cost: Size of Fraud in the Supply Chain Industry
Fraud and cyberattacks in the supply chain ecosystem cost businesses billions annually. According to PwC, over 49% of organizations have experienced some form of supply chain fraud, waste, or abuse. Post-2020, cyberattacks targeting logistics companies and digital procurement systems have grown by 60% World Economic Forum. Losses stem not only from direct theft but also from downtime, legal penalties, and reputational harm. A Deloitte report revealed that 26% of companies found supplier fraud as one of their most damaging fraud events. From mule account creation in vendor databases to phishing targeting logistics portals, fraud's hidden costs are vast.
Real-World Cases of Fraud in the Supply Chain
Real-world supply chain fraud incidents demonstrate the sophisticated nature of modern threats:
- Maersk NotPetya Attack (2017): A global shipping giant, Maersk, was hit by the NotPetya malware attack, which shut down its entire IT infrastructure, resulting in an estimated $300 million in losses. The malware entered through a compromised Ukrainian accounting software used by a third-party vendor.
- Target Data Breach (2013): Hackers gained access to Target's internal network through a compromised HVAC vendor. Although not a logistics company, this case highlights the importance of third-party vendor security in supply chain networks.
- COVID-19 PPE Procurement Fraud: During the pandemic, governments and healthcare supply chains experienced fraud involving fake suppliers and counterfeit PPE. Europol reported dozens of arrests in global scams that siphoned millions.
- Tesla Insider Trade Secret Leak (2020): A Tesla employee was allegedly offered $1 million to install ransomware on the company's supply chain management systems. The insider instead reported the attempt, preventing major disruption.
- Amazon Counterfeit Crackdowns: Amazon has faced numerous fraud incidents involving fake supply chain partners selling counterfeit products. The company launched its Counterfeit Crimes Unit to address this.
Consequences of Not Being Protected Against Fraud and Data Breaches
Failing to secure supply chain operations against cyber threats and fraud can result in devastating, far-reaching consequences. Modern supply chains are deeply interconnected, and a single weak link, such as an unvetted vendor, exposed login credentials, or compromised shipping system, can unravel the entire operation. Below are key impacts supply chain organizations face if they lack adequate cybersecurity and fraud detection measures:
- Operational Disruption: Cyberattacks targeting logistics infrastructure, such as transport management systems or warehouse control platforms, can bring critical operations to a halt. Downtime leads to missed delivery timelines, supply shortages, production delays, and a ripple effect across business partners.
- Financial Losses: According to IBM, the average cost of a data breach in 2023 was $4.45 million IBM Security Reports. For global logistics and supply firms, these numbers are significantly higher due to the scale of transactions. Fraudulent invoices, cargo rerouting, procurement scams, and warranty abuse drain capital from the system.
- Reputational Damage: Repeated incidents of supply chain fraud, such as delivery fraud or counterfeiting, severely damage brand trust. Customers and partners often disengage after a public breach, especially if negligence or lack of transparency is revealed.
- Regulatory Fines and Legal Liability: Non-compliance with industry regulations like GDPR, ISO 28000, or CTPAT can result in heavy penalties. Organizations may also face class-action lawsuits from impacted customers or partners whose data was compromised.
- Increased Insurance Premiums and Risk Ratings: After an incident, insurers may reclassify the organization as high risk, leading to elevated premiums. Risk scoring firms may also downgrade your vendor profile, impacting future contracts.
Regulatory and Compliance Challenges in the Supply Chain
Supply chain operations now require adherence to various compliance frameworks:
- GDPR: Impacts how data is shared across vendor networks.
- ISO 28000: Focuses on supply chain security management systems.
- C-TPAT and AEO: Require risk assessments for international shipping.
- Third-Party Risk Management: Most breaches originate from external vendors.

Fraud Types in the Supply Chain: Stats and Case Studies
Supply chain fraud takes various sophisticated forms:
- Procurement Fraud: Often orchestrated internally with colluding vendors, this includes inflated invoicing, duplicate payments, and kickbacks. Global procurement fraud exceeds $3.5 billion annually.
- Invoice Fraud: Criminals alter legitimate invoices or create fake vendors entirely, redirecting payments into fraudulent accounts.
- Cargo Theft: Common in high-value sectors such as electronics, pharma, and automotive. Physical theft now combines with digital manipulation (e.g., falsified tracking data).
- Return & Warranty Fraud: Especially in e-commerce, this involves falsely claimed returns or forged warranty documentation.
- Fake or Counterfeit Parts: Manufacturing supply chains are plagued by counterfeit components, affecting quality and safety.
- Third-party Vendor Exploits: Many attacks begin with phishing or malware delivered through trusted vendors. TraxTech reports 45% of ransomware incidents originate from third-party portals.
Insider Threats in the Supply Chain Industry
Insider threats account for over one-third of all supply chain fraud cases. As outlined in CrossClassify's insider threats analysis, these threats include:
- Negligent Insider: Employees who accidentally leak access credentials or upload sensitive data to public drives.
- Malicious Insider: Deliberately leaks information, manipulates vendor data, or reroutes payments for personal gain.
- Compromised Insider: An employee whose device or credentials are hijacked by external attackers.
- Unintentional Insider: Those unaware of the risk their actions pose, such as approving fake vendors or using weak passwords.
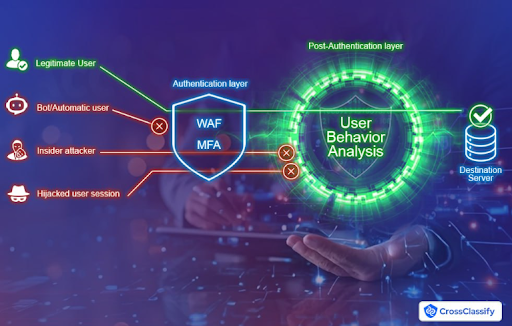
Why MFA and WAF Alone Are Not Enough
While multi-factor authentication (MFA) and web application firewalls (WAFs) are important, they are not sufficient in isolation. Attackers are bypassing MFA via session hijacking, SIM swapping, and phishing-resistant tactics. Malware injected via third-party code and plugins can render WAFs ineffective. For deeper protection, supply chain platforms need behavioral biometrics, device fingerprinting, and anomaly detection tools.
Read more: Uncover the Threats WAF and MFA Miss
Emerging Sections
How to Prevent Cargo Theft and Insurance Fraud in Logistics
Combining GPS tracking with anomaly detection and behavioral analysis is key. Cross-referencing sensor data with behavioral trends can alert teams in real-time before cargo theft occurs.
Compare Procurement Fraud Detection Software for Manufacturers
Manufacturers must look beyond basic audit logs. Advanced tools use machine learning to flag suspicious procurement workflows, collusion patterns, and overbilling anomalies.
Best Anti-Fraud Solutions for Supply Chain Finance
Supply chain financing platforms should integrate real-time fraud scoring, vendor fingerprinting, and behavioral risk analytics to prevent abuse of invoice financing.
Top Supply Chain Cyber Threat Monitoring Solutions for 2025
Look for platforms offering continuous behavioral monitoring, IP risk scoring, and device fingerprinting with low latency.
Best Vendor Risk Management Software for Supply Chain Cybersecurity
Choose solutions that provide geo-analytics, third-party behavior insights, and link analysis between suppliers and suspicious entities.
Combining GPS tracking with anomaly detection and behavioral analysis is key. Cross-referencing sensor data with behavioral trends can alert teams in real-time before cargo theft occurs.
Compare Procurement Fraud Detection Software for Manufacturers
Manufacturers must look beyond basic audit logs. Advanced tools use machine learning to flag suspicious procurement workflows, collusion patterns, and overbilling anomalies.
Best Anti-Fraud Solutions for Supply Chain Finance
Supply chain financing platforms should integrate real-time fraud scoring, vendor fingerprinting, and behavioral risk analytics to prevent abuse of invoice financing.
Top Supply Chain Cyber Threat Monitoring Solutions for 2025
Look for platforms offering continuous behavioral monitoring, IP risk scoring, and device fingerprinting with low latency.
Best Vendor Risk Management Software for Supply Chain Cybersecurity
Choose solutions that provide geo-analytics, third-party behavior insights, and link analysis between suppliers and suspicious entities.
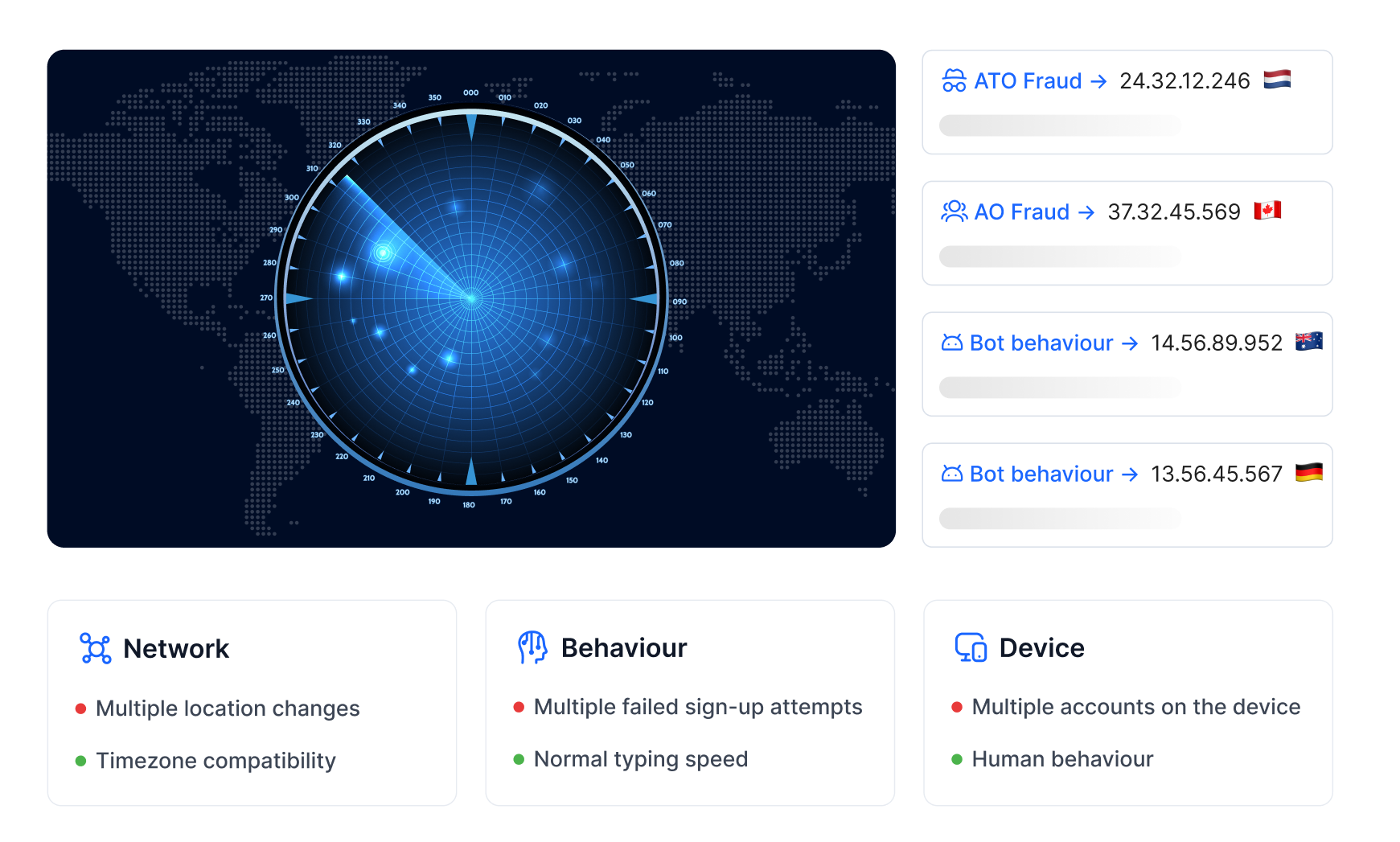
How CrossClassify Helps Supply Chain Organizations Stay Secure
Continuous Monitoring in Supply Chain Platforms: Track real-time user activity across procurement portals, logistics dashboards, and supplier tools. Early detection of anomalies can stop fraud before it escalates. Read more
Behavior Analysis in Supply Chain Workflows: Identify deviations in employee or vendor behavior, such as unusual order volumes, off-hour logins, or data scraping. Read more
Geo Analysis in Global Supplier Networks: Detect suspicious access from unexpected regions, rerouted cargo manipulation, or access anomalies based on geo-patterns. Read more
Link Analysis Across Vendor Chains: Uncover hidden relationships between vendors, identify collusion, or detect vendor-reseller fraud rings. Read more
Enhanced Security and Accuracy in Fraud Detection: Score risks more accurately by combining fingerprinting, behavioral trends, and anomaly detection. Read more
Seamless Integration with Supply Chain Platforms: Whether it's SAP, Oracle SCM, or custom logistics dashboards, CrossClassify offers easy SDK/API integration. Read more
Alerting and Notification in Logistics Fraud Scenarios: Instant alerts for policy violations, supplier mismatches, or login anomalies allow security teams to respond before damage occurs.
Behavior Analysis in Supply Chain Workflows: Identify deviations in employee or vendor behavior, such as unusual order volumes, off-hour logins, or data scraping. Read more
Geo Analysis in Global Supplier Networks: Detect suspicious access from unexpected regions, rerouted cargo manipulation, or access anomalies based on geo-patterns. Read more
Link Analysis Across Vendor Chains: Uncover hidden relationships between vendors, identify collusion, or detect vendor-reseller fraud rings. Read more
Enhanced Security and Accuracy in Fraud Detection: Score risks more accurately by combining fingerprinting, behavioral trends, and anomaly detection. Read more
Seamless Integration with Supply Chain Platforms: Whether it's SAP, Oracle SCM, or custom logistics dashboards, CrossClassify offers easy SDK/API integration. Read more
Alerting and Notification in Logistics Fraud Scenarios: Instant alerts for policy violations, supplier mismatches, or login anomalies allow security teams to respond before damage occurs.
Conclusions and Future Outlook
The supply chain industry is undergoing a major transformation, driven by digitization, globalization, and increasing complexity. Unfortunately, these trends have also expanded the attack surface for cybercriminals and fraudsters. From insider threats to sophisticated invoice scams and vendor exploits, the threat landscape is wide and fast-evolving. Regulatory pressure, customer expectations, and operational continuity demand a proactive, adaptive approach to cybersecurity.
CrossClassify offers a comprehensive fraud detection and behavior monitoring platform tailored for supply chain use cases. By integrating link analysis, device fingerprinting, behavioral monitoring, and geo-based tracking, organizations can gain real-time insights into emerging threats. Whether it's catching insider anomalies or blocking suspicious devices, CrossClassify helps secure supply chains before threats become crises.
CrossClassify offers a comprehensive fraud detection and behavior monitoring platform tailored for supply chain use cases. By integrating link analysis, device fingerprinting, behavioral monitoring, and geo-based tracking, organizations can gain real-time insights into emerging threats. Whether it's catching insider anomalies or blocking suspicious devices, CrossClassify helps secure supply chains before threats become crises.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Invoice fraud detection in supply chain systems is critical as fake or altered invoices can siphon millions from procurement budgets. CrossClassify uses behavioral analytics and device fingerprinting to flag anomalies in billing patterns and payment approvals. Learn more →
Insider threat in logistics platforms can cause massive damage through data leaks, collusion, or sabotage. CrossClassify identifies negligent, malicious, and compromised insiders using behavior profiling and access monitoring. Explore more →
Cargo theft prevention in supply chain logistics must go beyond GPS. CrossClassify combines behavioral data, geo-analysis, and device intelligence to catch cargo rerouting attempts in real-time. See how it works →
Why MFA and WAF are not enough in supply chain cybersecurity is evident in today's advanced threat landscape. CrossClassify extends protection using anomaly detection, risk scoring, and behavioral biometrics. More here →
Procurement fraud detection software for manufacturers should identify overbilling, vendor collusion, and unusual ordering. CrossClassify uses ML-driven workflows and access visibility to expose fraud in supplier interactions. Full article →
Vendor risk management in supply chain cybersecurity is essential due to third-party breaches. CrossClassify applies link analysis and behavior scoring to identify high-risk supplier accounts or collusion patterns. Explore more →
Supply chain fraud detection through continuous monitoring gives teams real-time alerts on suspicious behavior. CrossClassify tracks sessions, login attempts, and user actions across procurement and logistics platforms. Learn more →
Fake supplier detection in supply chain finance can prevent loss and brand damage. CrossClassify flags risky domains, fake MC numbers, and login behavior that diverges from known vendors. Full breakdown →
Geo-behavioral analytics for logistics fraud prevention helps catch suspicious access from unauthorized regions. CrossClassify integrates geo-pattern analysis into fraud scoring to reveal spoofing or bot-based access. Explore feature →
Accurate fraud detection in logistics with AI balances security and business continuity. CrossClassify uses layered context, devices, location, behavior, and intent, to reduce alert fatigue and catch real threats. Learn more →
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
