09 Jul 2025
Insider Threats: You’re Tracking 1 of 4—Here’s What You’re Missing
Most companies only track 1 out of 4 insider threats.
Guess which one?
The Malicious Insider.
The “obvious” one—the angry employee with a plan.
And yes—those exist.
But they’re not the full picture. Not even close.
Insider attacks are rising.
They don’t knock.
They log in.
And that’s the problem—because once someone’s inside, your WAF, your MFA, your firewall...
None of it matters.
Here’s what most teams miss:
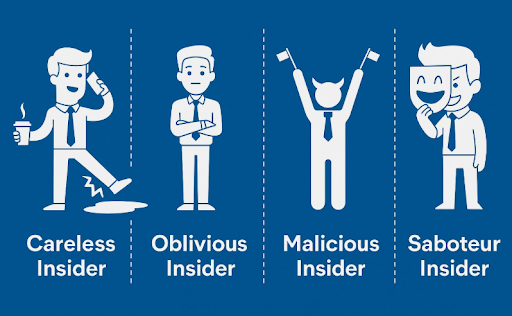
There are 4 types of insiders—only 1 is intentionally harmful:
Careless Insider
Not malicious. Just negligent. A shared password. A forgotten logout. A device left open. One moment of sloppiness = full compromise.
Oblivious Insider
They’ve been compromised and don’t know it. Phished. Hacked. Hijacked. Now a threat in disguise.
Malicious Insider
The one you’re watching for. And probably the only one you’re actively monitoring.
Saboteur Insider
Rare, but lethal. They’re in it to burn bridges, break systems, or quietly kill momentum from the inside.
Here’s the catch:
Most CEOs and CISOs only plan for Malicious or Saboteur insiders.
But the real damage often starts with Careless or Oblivious ones— people who don’t even realize they’re opening the door.
You don’t stop that kind of threat with policies or guesswork.
You stop it with visibility.
That’s why we built CrossClassify.
To watch behavior, not just credentials.
To flag intent, not just logins.
To protect the business, even from people who don’t mean to break it.
- Real-time behavior analytics.
- Continuous trust assessment.
- Protection that starts after the login.
Because insider threats don’t always look like threats—until it’s too late.
