Last Updated on 12 Mar 2025
Uncover the Threats WAF & MFA Miss – Real User Behavior Protection
Share in
Key Notes
•
Traditional security measures like WAF and MFA are essential but insufficient in protecting against modern cyber threats.•
WAFs (Web Application Firewalls) block known threats like SQL injection and XSS but cannot detect sophisticated fraud such as account takeovers and credential stuffing.•
MFA (Multi-Factor Authentication) adds an extra layer of security but is not foolproof, as attackers can bypass it through phishing, SIM swapping, and MFA fatigue attacks.•
AI-powered User Behavior Analytics (UBA) continuously monitors user actions, detects anomalies, and responds to evolving fraud tactics in real-time, ensuring proactive threat prevention beyond traditional security measures.
Introduction
The growing sophistication of cybercriminals has resulted in unprecedented financial and operational damages. In 2024, 83% of organizations experienced at least one account takeover, signaling a drastic rise in identity fraud and unauthorized access. Consumer account takeovers have surged from 18% to 24% within a year, emphasizing that attackers are finding new ways to bypass conventional defenses. The financial implications are staggering, with identity fraud alone costing businesses $43 billion in 2023, Furthermore, online payment fraud is projected to escalate to $48 billion, marking a 16% increase from 2022.
Adding to these external threats, insider risks continue to grow. Research indicates that up to 75% of organizations remain vulnerable to insider threats, whether from malicious intent or inadvertent security lapses. Reports from 2023 further reveal a 67% rise in insider security incidents per company, making it clear that threats do not always originate externally.

These figures underscore a critical shift: cyber threats are no longer limited to external attackers attempting to breach firewalls or steal passwords. Instead, attackers are increasingly targeting authenticated sessions and leveraging compromised credentials to execute fraudulent activities. The reliance on traditional security solutions like WAF and MFA, while necessary, is no longer sufficient. This article explores key cyber threats and security measures—MFA, WAF, and CrossClassify—and provides a detailed analysis of their strengths and limitations in mitigating these risks. By analyzing real-world attacks and exploring how modern fraud detection methods work, we aim to highlight why businesses must adopt a multi-layered security approach that extends beyond authentication.
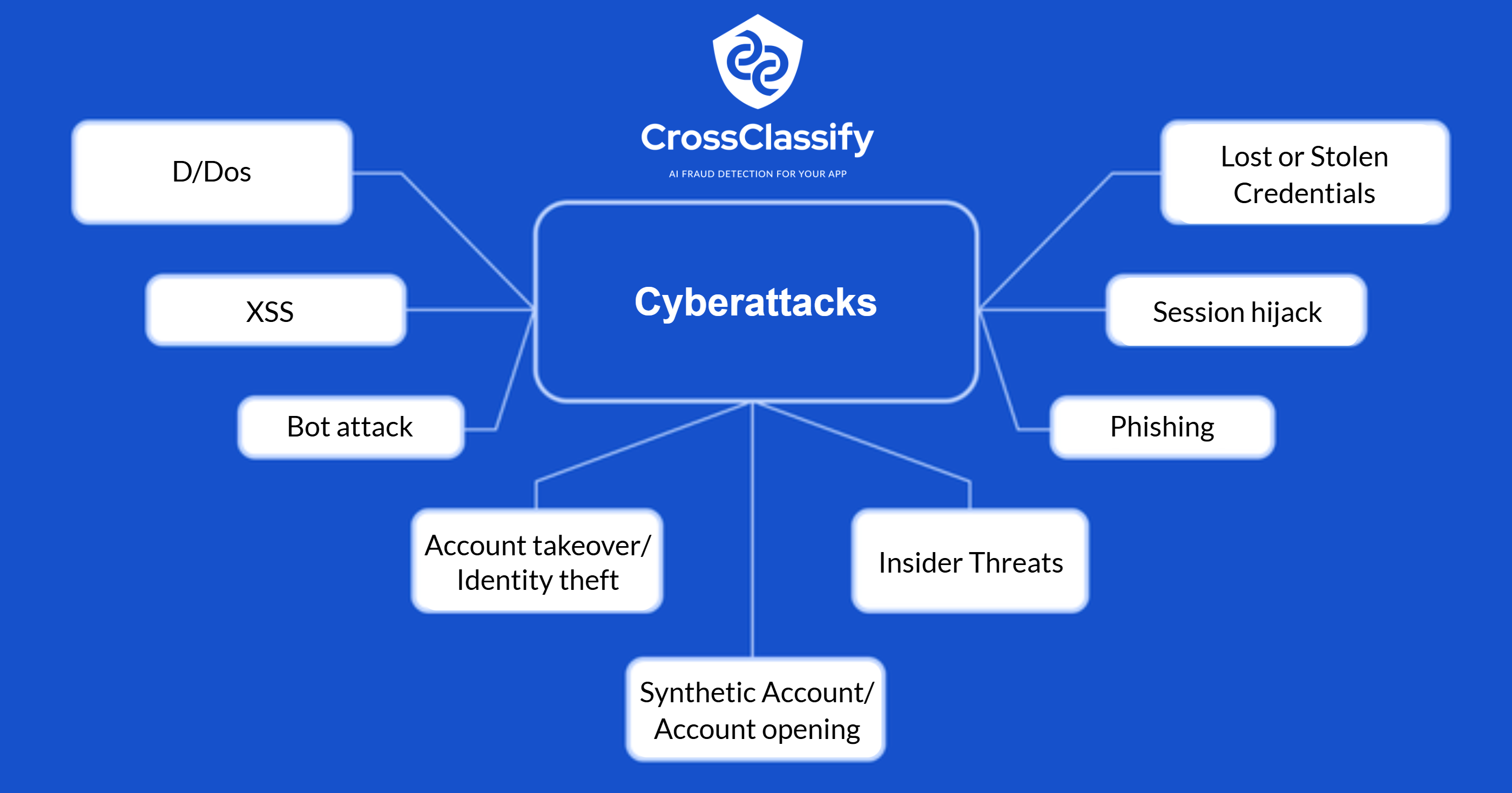
Understanding the Threat Landscape
•
Session Hijacking: Attackers intercept active user sessions to gain unauthorized access to sensitive accounts.•
Distributed Denial of Service (DDoS): Massive amounts of traffic overwhelm a website or service, rendering it inaccessible.•
Cross-Site Scripting (XSS): Malicious scripts are injected into trusted websites to steal information or manipulate user interactions.•
SQL Injection: Attackers exploit vulnerabilities in database queries to access, modify, or delete data.•
Keylogging: Malicious software records keystrokes to steal passwords, credit card details, and other sensitive information.•
Phishing: Cybercriminals deceive users into revealing credentials or financial information via fraudulent emails or websites.•
Lost or Stolen Credentials: Stolen passwords and account details provide attackers direct access to sensitive data.•
Web Scraping: Bots extract content or data from websites, often for malicious or competitive purposes.•
Bot Attacks: Automated scripts impersonate real users to exploit vulnerabilities, commit fraud, or launch brute-force attacks.•
Insider Threats: Employees or individuals with privileged access intentionally or unintentionally cause security breaches.•
Synthetic Account / Account Opening Fraud: Fraudsters create fake identities or use stolen credentials to open fraudulent accounts.•
Zero-Day Exploits: Hackers exploit undiscovered software vulnerabilities before developers can release patches.•
Account Takeover / Identity Theft: Attackers gain unauthorized access to user accounts through compromised credentials or social engineering.
The Role of WAF and MFA in Cybersecurity
Web Application Firewalls (WAF): Protecting Web Traffic
•
Blocking common web-based attacks such as SQL injection, cross-site scripting (XSS), and DDoS attacks.•
Preventing unauthorized access attempts by detecting and stopping malicious traffic before it reaches the application.•
Safeguarding APIs and web applications from exploitation by known attack patterns and automated bot attacks.
Multi-Factor Authentication (MFA): Strengthening Account Security
•
Reducing the risk of account compromise by requiring an additional authentication step beyond just a password.•
Protecting against credential stuffing attacks, where attackers attempt to log in using stolen usernames and passwords from data breaches.•
Providing flexibility with authentication methods, including biometric verification, one-time passcodes, and hardware security keys.
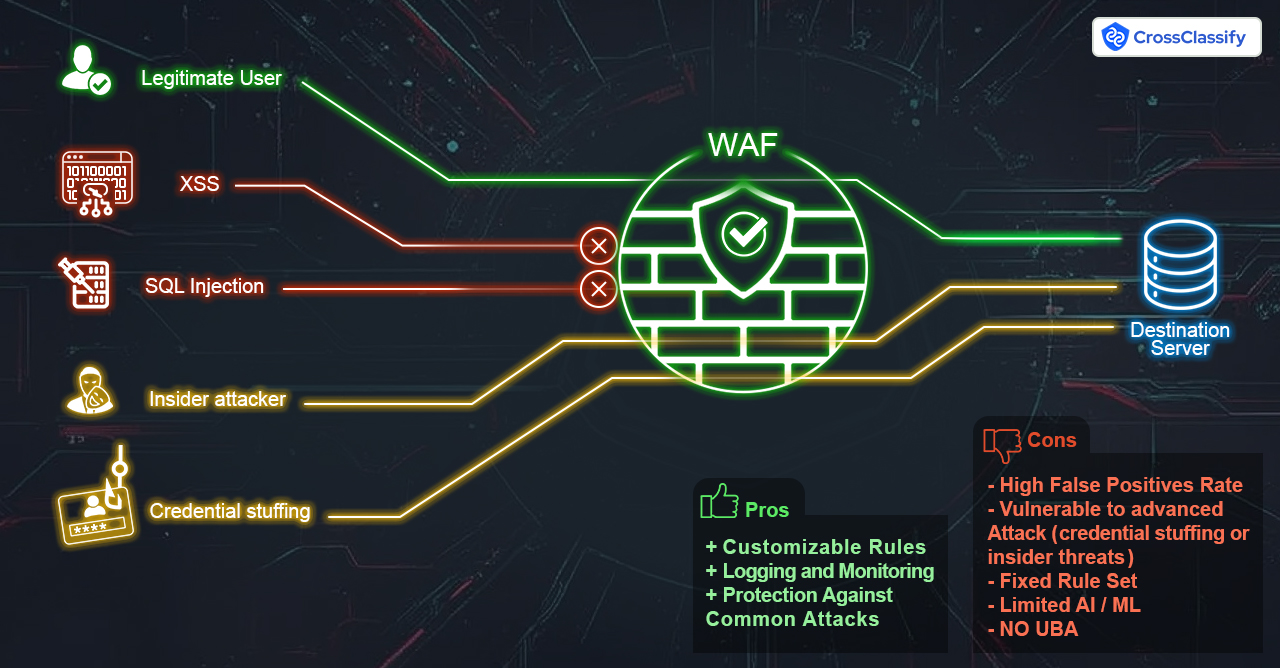
Limitations of WAF and MFA
Web Application Firewalls (WAF): Robust Yet Limited
•
Inability to Detect Sophisticated Fraud: WAFs primarily focus on known threat patterns and lack the capability to identify fraudulent users who utilize stolen credentials or emulate legitimate devices.•
Lack of Behavioral Analysis: WAFs do not monitor user behavior over time, making it difficult to detect anomalies indicative of malicious activity.•
Bypassing with Residential Proxies and Bots: Attackers use residential proxies and bot frameworks to evade WAF detection, making it challenging to distinguish between a genuine user and an attacker.
Multi-Factor Authentication (MFA): Essential but Not Foolproof
•
Credential Stuffing and Phishing: Attackers steal session tokens or credentials, allowing them to bypass MFA.•
SIM Swapping and Social Engineering: Attackers can hijack phone numbers through SIM swapping, intercepting MFA codes to gain access.•
MFA Fatigue Attacks: Attackers bombard users with repeated MFA requests until they approve one out of frustration or mistake.
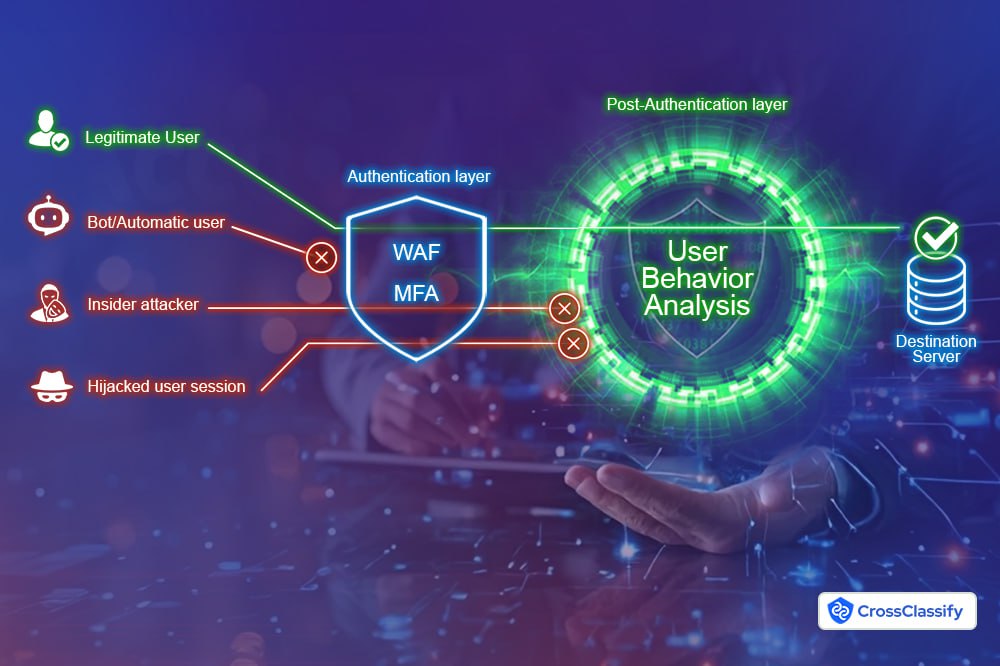
Combined Shortcomings: The Gaps in WAF and MFA
•
Post-Authentication Vulnerabilities: Neither monitors user activities after authentication, leaving room for account takeovers and fraudulent transactions.•
Deception by Sophisticated Attackers: Advanced tactics, such as using device emulators and residential proxies, enable attackers to mimic legitimate users, evading detection by WAF and MFA.
The Imperative for Advanced Fraud Detection: Introducing CrossClassify
1. Device Fingerprinting and Anomaly Detection
•
Emulated Environments: Identifying virtual machines and sandboxed environments often used by fraudsters.•
Proxy and VPN Usage: Detecting anomalies in network configurations that may indicate malicious intent.
2. Behavioral Analysis and Risk Scoring
•
Impossible Travel: Detecting logins from geographically distant locations within an unreasonably short timeframe.•
Rapid Account Access: Identifying unusually quick navigation through sensitive account areas, indicative of automated scripts or malicious intent.

3. AI-Powered Threat Intelligence
•
Real-Time Fraud Detection: Instantly recognizing and responding to emerging threat vectors.•
Adaptive Learning: Continuously updating threat models based on new data, ensuring resilience against evolving attack strategies.
4. Account Takeover and Synthetic Fraud Prevention
•
Account Takeovers (ATO): Identifying unauthorized access attempts even when correct credentials are used.•
Synthetic Fraud: Detecting the creation of fake accounts using a mix of real and fabricated information, a common tactic for fraudulent activities.
Comparative Analysis: WAF, MFA, and CrossClassify
| Security Measure | What It Protects Against | What It Misses | Why CrossClassify is Needed |
|---|---|---|---|
| WAF (Cloudflare, AWS WAF, etc.) | Blocks known threats (SQL injection, XSS, DDoS, bots) | Cannot detect Account Takeover (ATO), credential stuffing, human fraud | CrossClassify detects fraud after authentication, identifying real users vs. fraudsters |
| MFA (Google Auth, Okta, etc.) | Prevents unauthorized logins (phishing, brute-force) | Can be bypassed with stolen sessions, SIM swapping | CrossClassify detects behavioral anomalies even if MFA is passed |
| CrossClassify | Detects sophisticated fraud, session hijacking, device & behavior anomalies | Complements WAF & MFA to detect fraud that happens post-login | Prevents Account Takeover (ATO), synthetic fraud, and insider threats |
Conclusion
See How Protecting Customers from the Growing Threat of Account Takeover
Ensure Continuous Security with Real-Time Account Monitoring

Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Related articles
Frequently asked questions
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required



