Last Updated on 21 Apr 2025
Continuous Adaptive Risk and Trust Assessment (CARTA): Enhancing Enterprise Security
Share in
Introduction: What is CARTA?
CARTA and Modern Security Frameworks
Synergy with Zero Trust Architecture (ZTA)
Comparison of ZTA and CARTA
| Aspect | Zero Trust Architecture (ZTA) | Continuous Adaptive Risk and Trust Assessment (CARTA) |
|---|---|---|
| Core Principle | "Never trust, always verify" – strict verification for all access. | Continuous risk and trust assessment, adapting in real time. |
| Focus | Identity verification and access control at entry points. | Ongoing monitoring of behavior, context, and risk post-access. |
| Adaptability | Static policies applied consistently across sessions. | Dynamic adjustments to access and trust based on real-time data. |
| Response Mechanism | Relies on predefined rules for authentication/authorization. | Automated, context-aware responses like privilege adjustment. |
| Strength | Prevents unauthorized access with rigorous initial checks. | Detects and mitigates risks during active sessions. |
| Use Case Example | Blocks unverified users from accessing a network. | Flags a verified user’s suspicious activity and restricts access. |
History of CARTA
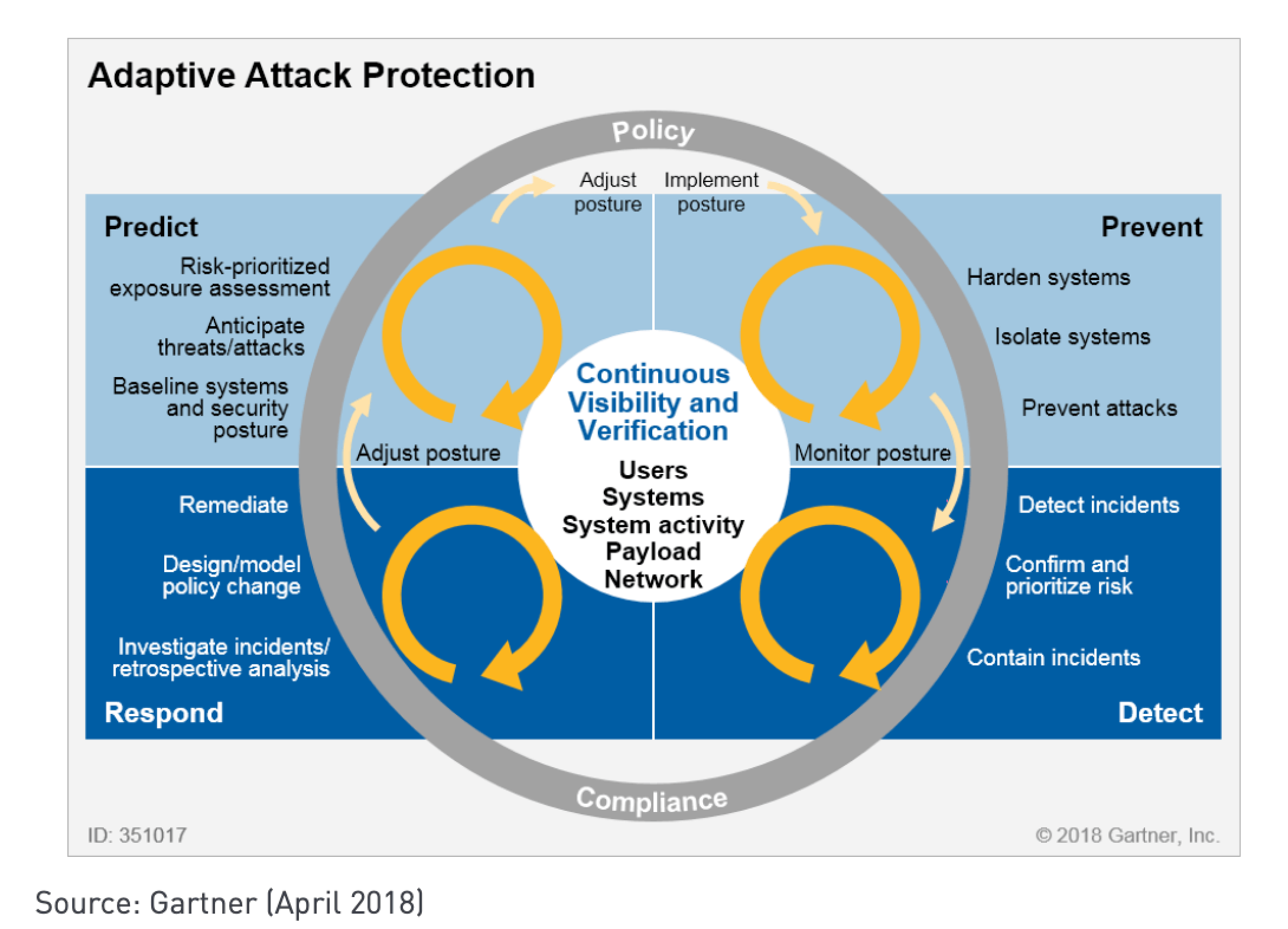
Key Concepts in CARTA Protocols
1.
Risk AssessmentRisk assessment in CARTA isn’t a one-off task—it’s an ongoing process laser-focused on spotting vulnerabilities, tracking threats, and gauging risk levels that shift by the minute. Unlike periodic scans that leave gaps for attackers to exploit, CARTA integrates real-time threat intelligence and predictive analytics to keep security policies ahead of the curve.•
Dynamic Threat Detection: CARTA never sleeps, constantly scanning for changes in threat vectors—whether it’s an external hacker probing your network or an internal user gone rogue.•
Behavioral Analytics: By studying user and system behavior, it pinpoints anomalies—like a sudden spike in data access—that could signal a breach in the making.•
Risk Scoring: Every asset and user gets a real-time risk score, offering a clear, actionable snapshot of exposure across the enterprise, from endpoints to cloud servers.
2.
Trust AssessmentTrust isn’t static in CARTA—it’s a fluid metric, evaluated continuously based on the reliability of users, devices, and systems. This isn’t about blind faith; it’s about building a trust profile that adapts to real-world conditions, ensuring only the right entities get access at the right time.•
Device Trustworthiness: CARTA checks if devices meet security benchmarks—think patched software or malware-free status—before letting them near sensitive resources.•
User Trust Levels: It tracks behavior patterns, login habits, and privilege use to confirm a user’s actions match their profile, flagging anything off-script.•
Contextual Trust: Location, network type, and timing matter—logging in from a shady VPN in a high-risk region might drop your trust score instantly.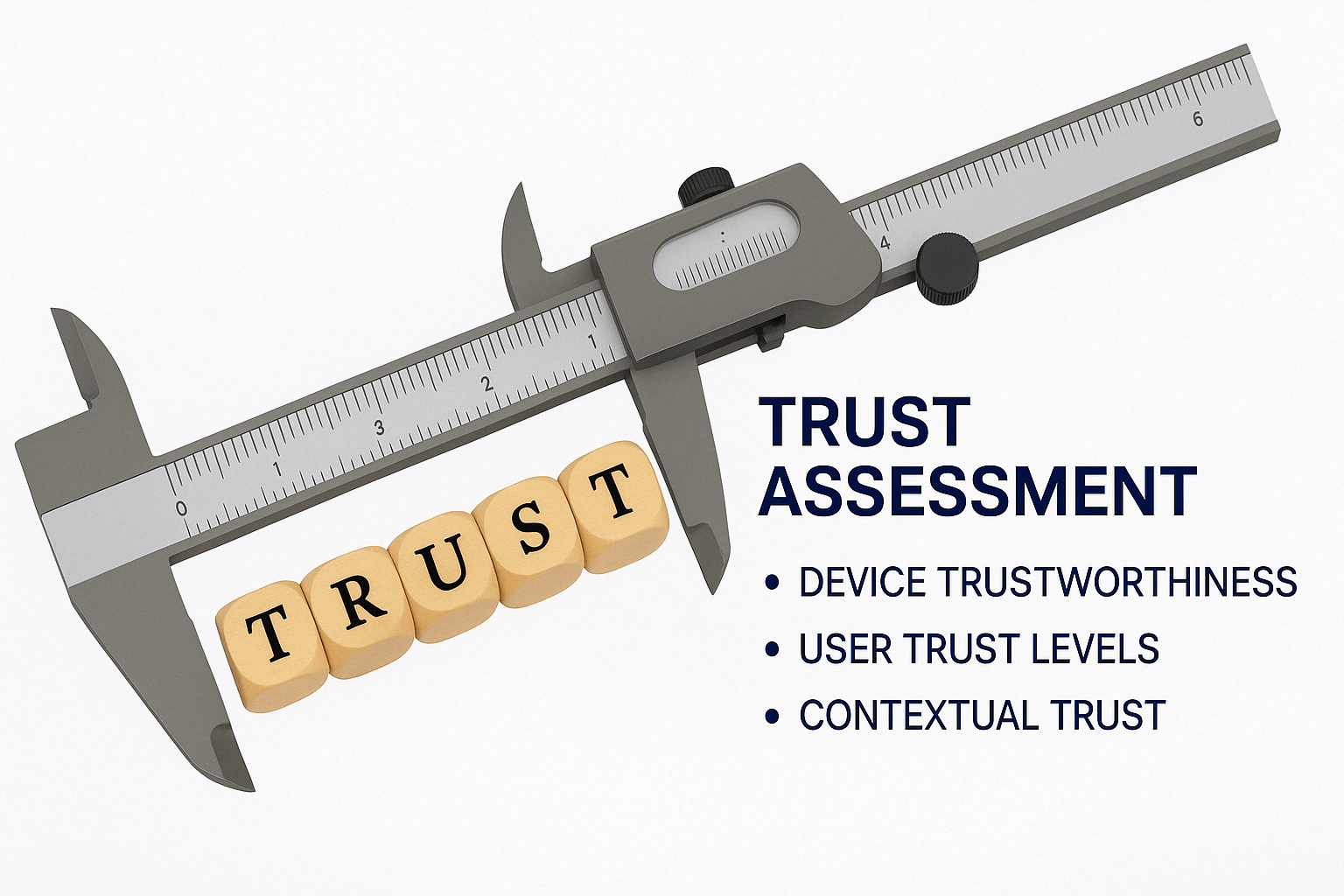
3.
Adaptive Security MechanismsCARTA’s real magic lies in its adaptability—security isn’t locked in stone but reshapes itself as risks evolve. This ensures defenses stay relevant, whether facing a new malware strain or a compromised insider.•
Dynamic Access Control: Access isn’t a blanket approval—it adjusts on the fly. A trusted user might lose privileges if their device pings a suspicious server.•
Automated Incident Response: Spot a risk? CARTA doesn’t wait for a human to act—it can quarantine a device or block traffic in seconds.•
Context-Aware Security Measures:Decisions hinge on real-time context—a late-night login from an unfamiliar IP might trigger extra checks, while a routine office login sails through
CARTA in Practice: Use Cases and Benefits
1.
Enhanced Threat Detection and PreventionCARTA’s continuous vigilance turbocharges threat detection. Where traditional systems lean on scheduled scans or post-breach fixes, CARTA catches threats as they unfold—like spotting a phishing attempt before the payload drops. This proactive edge can mean the difference between a minor alert and a full-blown data leak.2.
Improved User ExperienceAdaptive security doesn’t just protect—it streamlines. Legitimate users with consistent behavior face fewer hoops; a salesperson uploading files from a trusted device won’t get bogged down by endless prompts. CARTA saves the heavy scrutiny for outliers, keeping workflows smooth.
3.
Resource OptimizationBy focusing on high-risk zones—like a server with outdated patches—CARTA lets organizations deploy resources smartly, avoiding wasteful blanket measures. It’s about precision, not overkill, ensuring budgets and IT teams target what matters most.4.
Compliance and Regulatory AlignmentWith regulators breathing down necks, CARTA’s continuous monitoring and detailed logs make compliance a breeze. It tracks every security decision, offering an auditable trail that proves you’re meeting standards like GDPR or HIPAA—no last-minute scramble required.
5.
Post-MFA Security EnhancementMulti-Factor Authentication (MFA) is a solid first line of defense, but it’s not foolproof—once a user passes MFA, traditional systems often assume they’re safe for the entire session. CARTA steps in post-MFA to ensure that trust doesn’t become a liability. After initial authentication, CARTA continuously monitors the user’s session, analyzing behavior for signs of compromise—like unusual data access patterns or connections to risky networks. For instance, if an employee passes MFA but then attempts to download sensitive files from an unfamiliar device, CARTA can lower their trust score, trigger additional verification, or restrict access altogether. This ongoing scrutiny ensures that a stolen session or compromised credential doesn’t turn into a free pass for attackers, bridging the gap that MFA alone can’t cover.6.
Beyond RBAC: Dynamic Privilege ManagementWhile Role-Based Access Control (RBAC) provides a solid foundation by assigning permissions based on predefined roles, it lacks the flexibility to adapt to real-time changes in risk or user behavior. CARTA transcends RBAC by introducing dynamic privilege management that adjusts access rights continuously, not just at the point of entry. For instance, an employee with a finance role might have broad access under RBAC, but if CARTA detects unusual activity—like accessing sensitive data outside normal hours—it can temporarily scale back those privileges or require additional authentication. This ensures that access aligns with the current risk context, not a static role, achieving a higher level of security by preventing unauthorized actions that might slip through RBAC’s rigid framework. CARTA’s real-time adjustments thus offer a more granular, responsive approach, safeguarding enterprises against evolving threats that static role definitions can’t address.7.
Enhancing User Behavior Analytics AppliancesUser Behavior Analytics (UBA) appliances are powerful tools for detecting anomalies by analyzing patterns in user activity, but they often lack the real-time adaptability needed to respond effectively to emerging threats. CARTA supercharges UBA by integrating its continuous risk and trust assessment capabilities, enabling a more proactive and dynamic response to behavioral anomalies. For example, if a UBA appliance flags a user for downloading an unusual volume of data, CARTA doesn’t just log the alert—it immediately reassesses the user’s trust score, cross-references contextual factors like device health or location, and can automatically restrict access or trigger an incident response, such as isolating the user’s session. This seamless integration ensures that insights from UBA are actionable in real time, transforming static anomaly detection into a living defense mechanism that not only identifies risks but actively mitigates them, keeping enterprises a step ahead of potential breaches.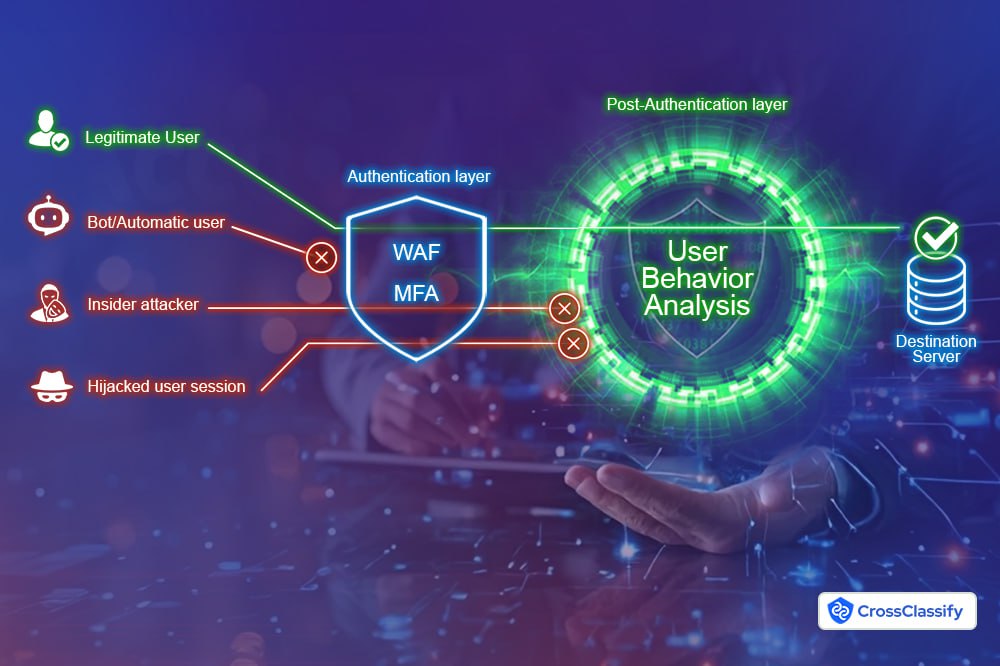
Implementation Challenges
CARTA and Existing Security Tools
Future Implications
Conclusion
See How Protecting Customers from the Growing Threat of Account Takeover
Ensure Continuous Security with Real-Time Account Monitoring

Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Related articles
Frequently asked questions
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required



