Last Updated on 25 Aug 2025
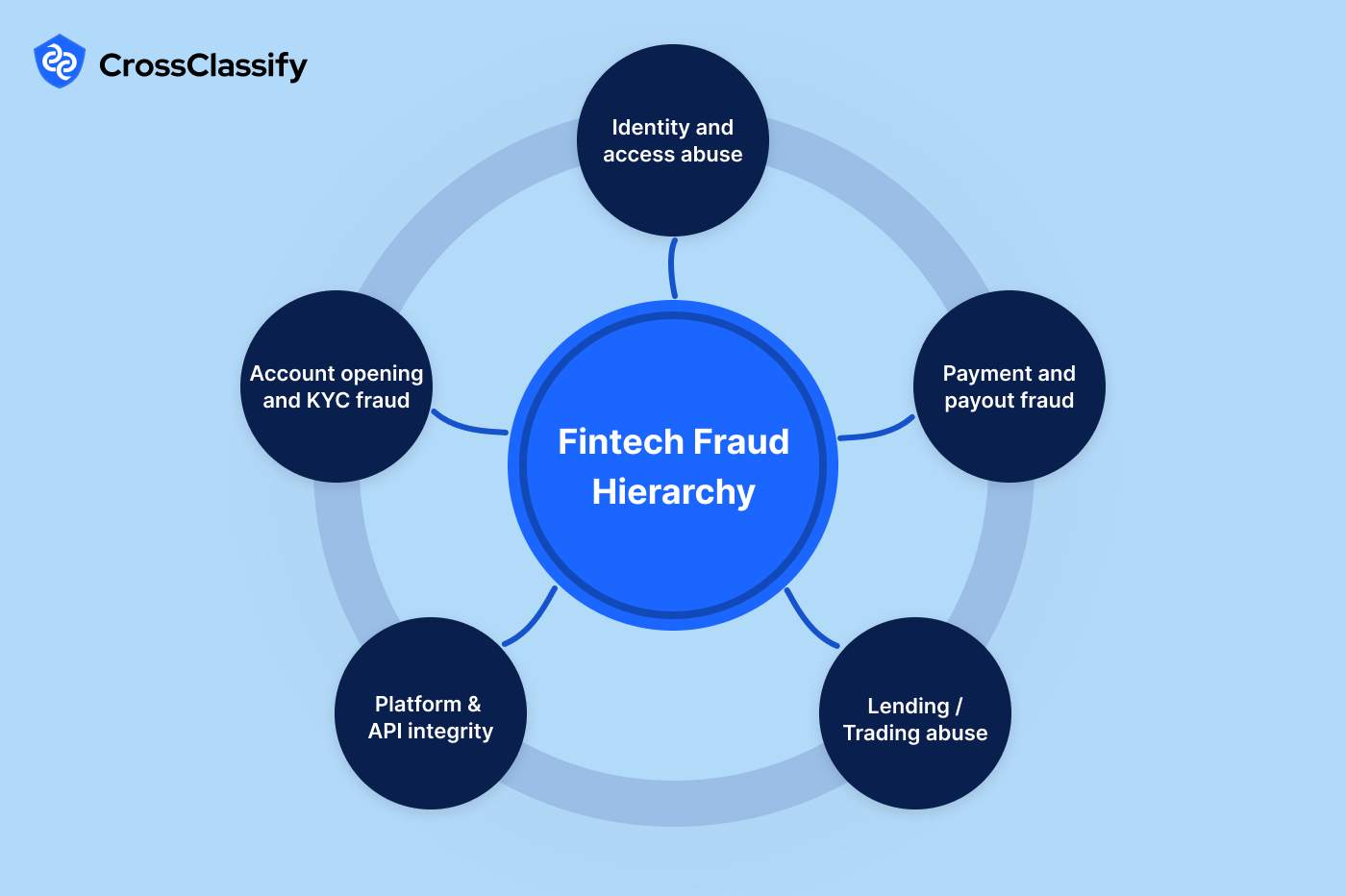
The Fintech Fraud Hierarchy: From Signals to Evidence and Action
Share in
Introduction
Fintech growth comes with a parallel surge in sophisticated attacks that target identity, payouts, onboarding, lending, trading, and APIs. This guide turns a complex threat landscape into a practical hierarchy you can use to prioritize controls, align teams, and choose evidence backed actions. Throughout, we highlight enterprise fintech fraud prevention platform patterns and how continuous intelligence across identity, device, behavior, payments, and content can close the gaps attackers exploit.
Identity and Access Abuse in Fintech
Modern attackers do not rush the front door. They live off the land inside identity flows, move between devices, and time their actions around high risk moments. You need to connect people, devices, and behavior continuously rather than rely on a single gate at login. Programs that win make identity decisions with context from session history, help desk touch points, network reputation, and payment intentions. This is where fintech device fingerprinting solution and behavioral biometrics for financial services deliver outsized value.
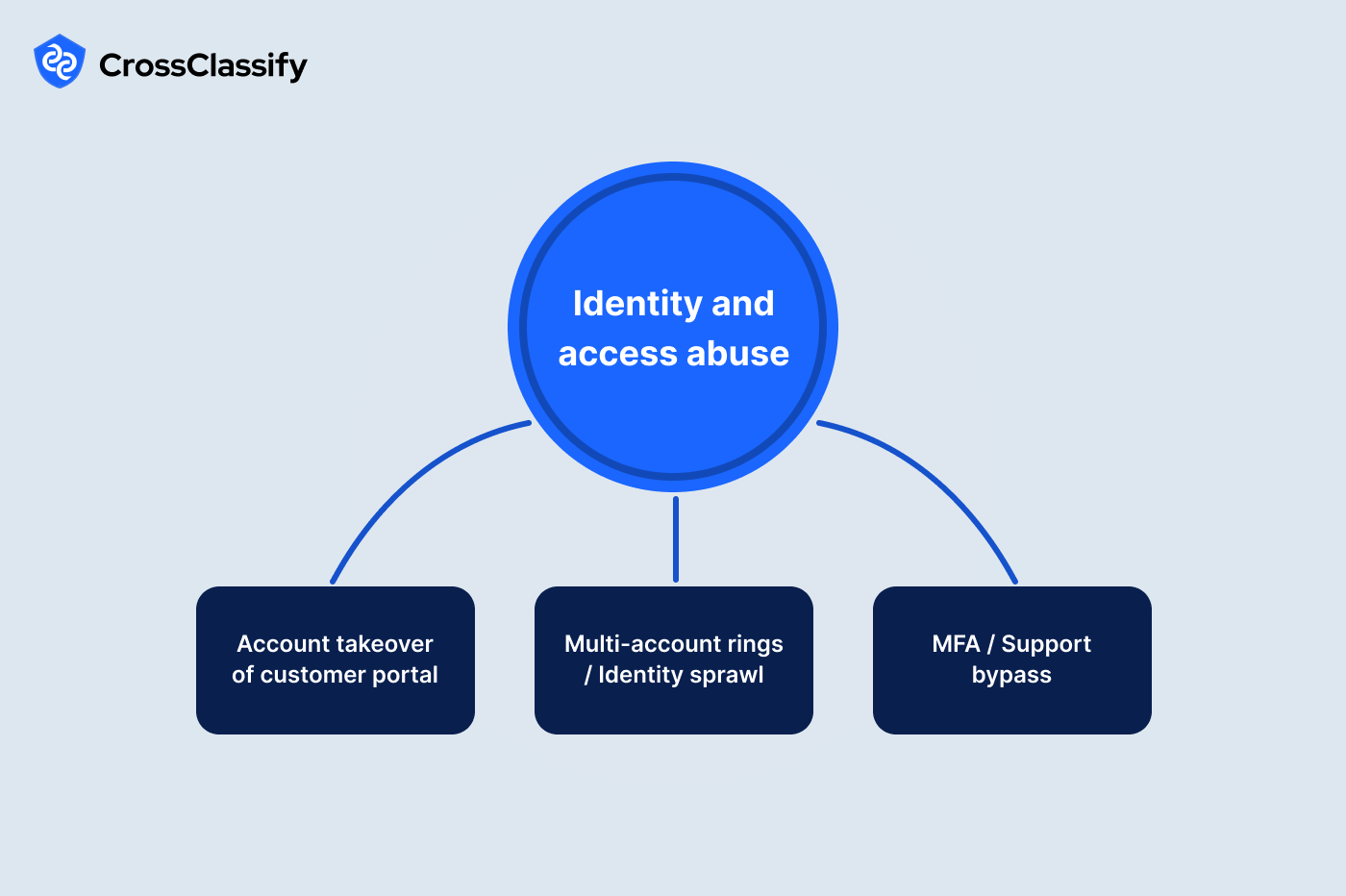

1. Account takeover of customer portals
Account takeover is the fastest path to loss because it converts immediately to withdrawals, crypto transfers, and settings abuse. Attackers stage with password stuffing, subtle social engineering, and support interactions that appear legitimate. The strongest defenses bind identity to the true device, watch for risky geo velocity, and step up friction only when risk rises. Well publicized incidents in consumer finance have shown how quickly small anomalies escalate into large losses when identity signals are siloed. Use continuous adaptive risk assessment for fintech to recompute risk at every sensitive step.
Signals and evidence
- Unfamiliar regions minutes before high risk actions: When the same account appears in a new geography and quickly attempts a withdrawal or limit edit, the pattern points to staged takeover. Evidence includes timing proximity between unusual access and the sensitive action plus device identity that does not match prior enrollments.
- Burst of failed logins that flips to a success near a limit change: A wave of failures followed by success just before a critical change often indicates credential stuffing. Evidence includes conversion after failure clusters and the correlation with a security sensitive step that normally happens far from login.
2. Multi account rings and identity sprawl
Fraud rings scale by spreading actions across many accounts that quietly share a small set of devices, browsers, and networks. Their goal is to look like many distinct customers while acting in lockstep. Defenders collapse those fragments back to the underlying hardware and behavior to expose the ring. The key is persistent device identity that holds through private browsing and VPN scenarios. Programs that deploy device fingerprinting for banking and fintech gain early detection and durable ring disruption.
Signals and evidence
- Many accounts tied to the same device or IP while submitting similar actions: Coordinated account groups reuse hardware to move funds, pass KYC, or request offers. Evidence includes device affinity across accounts and synchronized activity patterns.
- Reused device fingerprints across different KYC identities: Synthetic umbrellas reuse the same setup across multiple applicants. Evidence includes a single device fingerprint linked to unrelated identity records and repeated use of the same browser traits.
3. MFA and support bypass
Attackers increasingly script the human layer. They change a contact point, then request a reset, or they work the help desk to move authentication boundaries. Programs should enforce cooling periods, require step up only when the sequence is risky, and capture human context in the risk score. Strong teams instrument service channels so identity changes right after tickets get treated with caution. This is an ideal use of risk based MFA for fintech inside a Zero Trust identity and access program.
Signals and evidence
- Contact change followed by password or MFA reset in minutes: Tight timing between profile edits and resets often indicates a playbook. Evidence focuses on elapsed time between the changes and the presence of prior failed authentications.
- Support tickets that immediately precede credential changes: Help desk assisted changes without strong verification are a common bypass. Evidence includes the proximity of ticket closure to the credential update and the risk posture of the session.
Payments and Payout Fraud
Payment flows are monetization paths for attackers. They probe cards and wallets, redirect beneficiaries, and abuse chargebacks. Winning programs combine continuous device identity, anomaly detection, and strict beneficiary governance. The goal is to pause risky payouts automatically and let trusted money move without drag. This section maps to payment fraud prevention for fintech driven by linked identity signals.
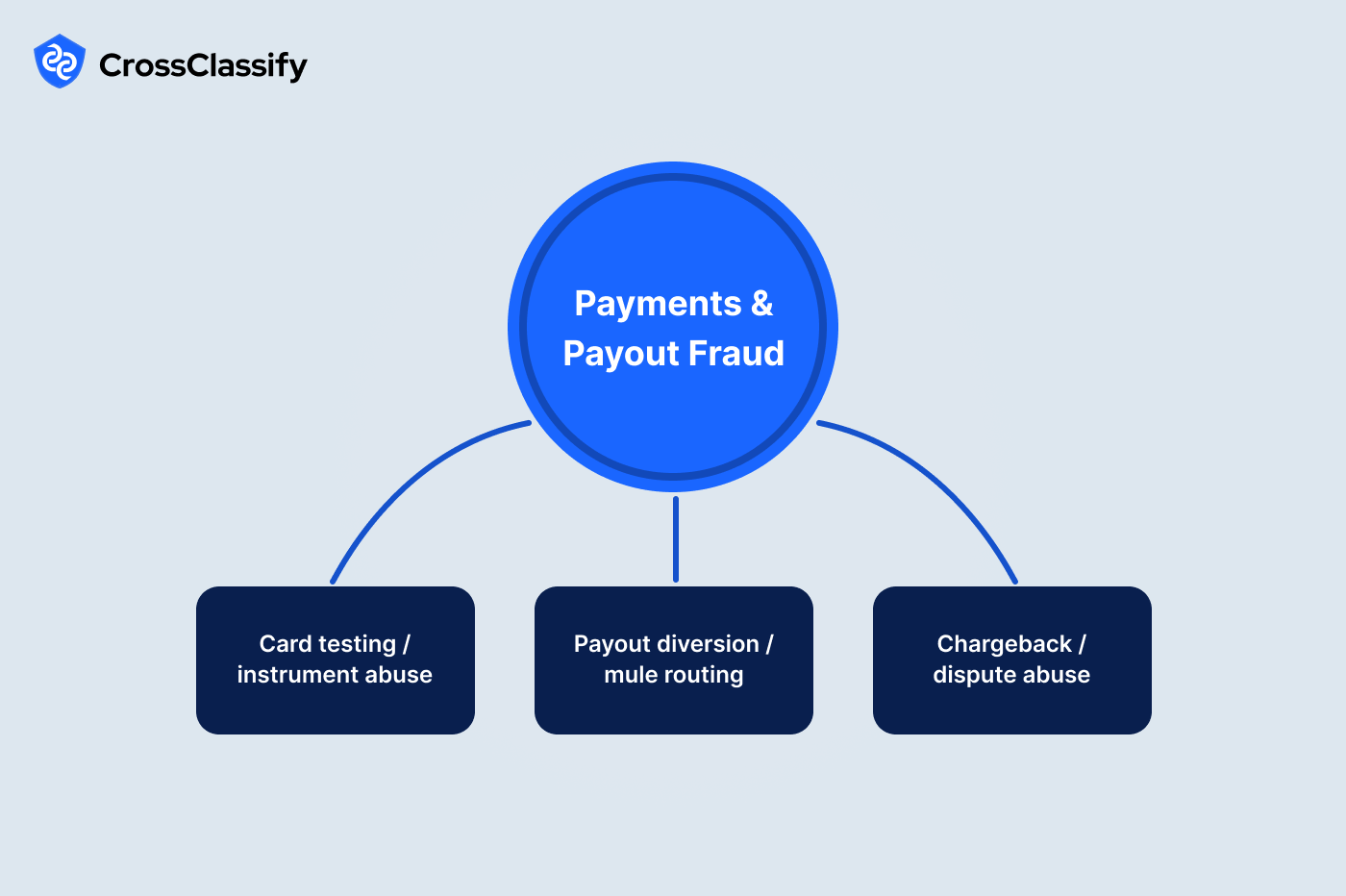

1. Card testing and instrument abuse
Card testing is noisy at the edge and quiet in the core. It starts with mismatch patterns then blends into normal spend if not contained. Controls must combine device binding, velocity limits, and BIN level anomaly detection. Effective teams push decisions in session rather than after reconciliation. Strong AI driven fintech fraud detection helps isolate the early waves.
Signals and evidence
- AVS or CVV mismatch spikes by BIN: Attackers focus on a small number of issuing ranges to learn rules. Evidence includes elevated mismatch rate for a BIN relative to peers and new devices driving the attempts.
2. Payout diversion and mule routing
Once inside, fraudsters change where the money goes. They edit a bank or add a wallet then push funds through shared destinations. Your defense is beneficiary verification, separation of duties, and device anchored step up. Evidence led controls let you hold payouts only when the risk is real. This protects customer experience while stopping loss.
Signals and evidence
- Bank change followed by a large payout within a day: Tight coupling between edits and payouts points to diversion. Evidence centers on timing proximity and the risk profile of the session that made the change.
- Multiple wallets funnel into the same beneficiary account: Shared destinations indicate mule hubs. Evidence includes many senders converging on one payout endpoint and shared device traits.
3. Chargeback and dispute abuse
Disputes are sometimes legitimate. Fraud programs go wrong when they block everyone or allow repeat abusers. Smart controls track the relationship between settled volume and disputes by cohort and device. The goal is to identify serial disputers early and preserve healthy customers. This ties directly to chargeback reduction for fintech with case ready evidence.
Signals and evidence
- Chargebacks rise while settled volume is flat: Divergence between disputes and sales often reflects abuse. Evidence includes disproportionate growth in dispute rates by account or device compared with stable processing volume.
Account Opening and KYC Fraud
The cheapest dollar is the dollar you never let in. Fraudsters industrialize fake onboarding with document kits, young domains, and automated bursts. Programs that align device identity, document integrity, and behavioral analysis at the first touch win earlier and cheaper. This is where account opening fraud prevention for fintech pays off fast.
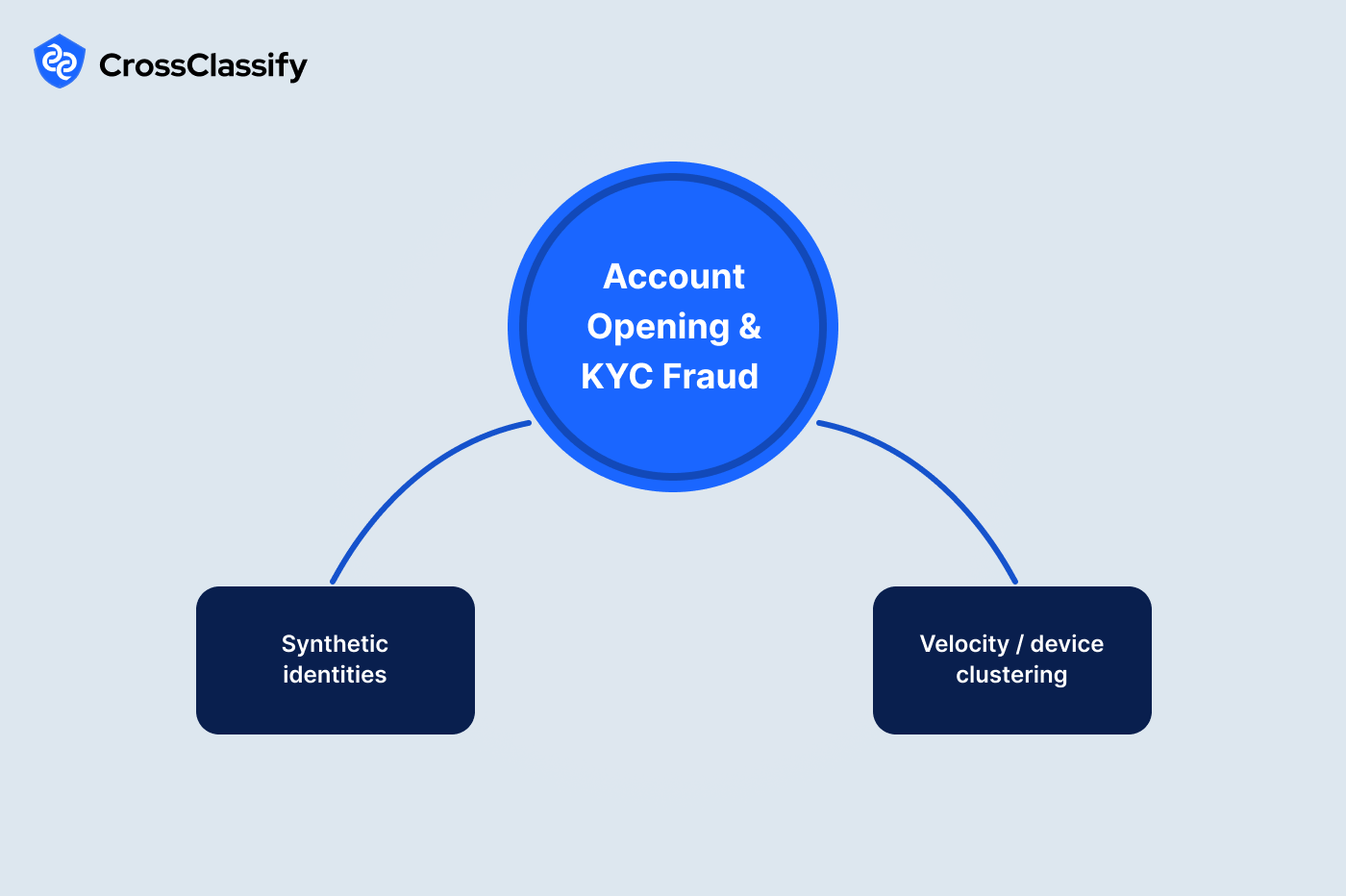

1. Synthetic identities
Synthetics reuse document elements, combine fragments of real data, and arrive from the same hardware. Device anchored identity, document hashing, and session behavior are your best early signals. Teams that catch kits at the perimeter avoid downstream losses such as chargeoffs, loans to ghosts, and money mule activity.
Signals and evidence
- Document fingerprint or hash appears across many applicants: Repeatable kits show the same file traits across unrelated people. Evidence includes identical document hashes or repeated metadata across submissions.
2. Young domains and low reputation email sources
Throwaway inboxes and newly registered domains are a favorite of farms. Alone, domain age is not enough. Combined with device sharing and velocity it becomes a high precision filter. Use behavioral biometrics during onboarding to separate careful humans from scripted flows.
Signals and evidence
- Submissions cluster in very young email domains: Concentration of new domains suggests temporary infrastructure. Evidence includes domain age, low deliverability reputation, and synchronized signup timing.
3. Velocity and device clustering
Fraud farms spike signups from the same device clusters within short windows. The fix is simple in concept and subtle in practice. Persistently identify devices and throttle only when cohort risk is real. That keeps growth teams happy and blocks the farms.
Signals and evidence
- Short window spikes in signups from the same device cluster: Velocity that exceeds organic patterns indicates automation. Evidence includes repeated hardware traits and identical navigation rhythm.
4. Face match anomalies in selfie and ID checks
Biometrics are powerful when used with context. Watch for score tails, overconfident matches, and repeated borderline outcomes from the same hardware. Use step up with liveness or re capture rather than default denial to keep safe customers moving.
Signals and evidence
- Abnormal concentration of borderline or extreme face match scores: Tails in the distribution suggest spoofing or template gaming. Evidence includes repeated borderline outcomes and reuse of the same capture setup.
Lending and Trading Abuse
After onboarding, fraud shifts into credit and market misuse. Bust out patterns start clean, then borrow and disappear. Trading abuse ranges from rate floods to circular counterparties. Controls must recompute risk by cohort, connect origination devices to repayment, and watch for self dealing in order flow. This is the domain of lending fraud analytics for fintech and market abuse surveillance for fintech.

1. Early default and bust out
Bust outs build trust then strike quickly. You need cohort monitoring for first payment default, device linkages to origination, and policy snapshots for limit changes. Programs that catch the leading edge reduce chargeoffs significantly.
Signals and evidence
- First payment default outliers by cohort: Elevated early default in a specific segment indicates concentrated risk. Evidence includes shared devices at origination and unusual application timing.
2. Loan stacking and identity sharing
Fraudsters stack loans across many devices with the same identity fragments. The cure is strong device binding at credit decision time and limits that adjust to identity confidence. Device intelligence for credit risk should be part of every underwriting stack.
Signals and evidence
- The same national ID or SSN appears across many devices: Wide device spread for one identity suggests sharing or theft. Evidence includes device graph expansion over short windows and inconsistent session behavior.
3. Market manipulation
Automated order floods and repeated trades between the same parties distort markets. Surveillance should combine order cadence, slippage impact, and counterparty networks. A risk engine that throttles when cadence breaks human limits will protect liquidity without punishing active traders.
Signals and evidence
- Abnormally high order rate per second: Orders that exceed human cadence indicate automation. Evidence includes short spike bursts concentrated in narrow windows.
- Repeated trades among the same counterparties: Closed loops reveal wash activity. Evidence includes frequent matched interactions between the same nodes.
Platform and API Integrity
APIs are your business engine and attackers know it. They scrape prices and routes, tamper with parameters, and manufacture deltas between quotes and charges. Treat your APIs like products with identity, rate, and content controls. This is the heart of bot detection for fintech and secure API gateway for financial services.
1. Scraping and botting
Scraping hurts conversion, compresses margins, and disrupts customer experience. The best defenses avoid static challenges and shift to invisible device and behavior sensing with adaptive throttles. Connect bot intelligence to commercial rules so you can slow the bad and serve the good.
Signals and evidence
- Excessive requests from headless or script agents: Non human access patterns concentrate on critical endpoints. Evidence includes agent fingerprints that match automation frameworks and short interval request bursts.
- Extreme search to action ratio by IP block: Reconnaissance ranges poll but rarely convert. Evidence includes disproportionate lookup to transaction mixes localized to a few networks.
2. Deep link and parameter tampering
When quotes are computed client side or parameters are weakly enforced, attackers will manufacture price deltas. Your best response is server side recomputation, strict allow lists, and full audit of who changed what and when. These steps pay back instantly by preventing underbilled or overbilled transactions.
Signals and evidence
- Mismatch between quoted and charged price: Positive deltas point to manipulation or misrouting. Evidence includes consistent overcharges tied to a narrow set of sessions.
- Unsupported parameters in requests: Rogue fields indicate probing and fuzzing. Evidence includes spikes in unknown codes hitting sensitive endpoints.
Pulling It Together
Successful fintech programs make risk a continuous product feature. They bind identity to devices, learn human rhythm, and watch money movement in context. Most important, they allow safe customers to move quickly while presenting friction only when the evidence demands it. If you are building an enterprise fraud prevention platform for fintech, combine device fingerprinting for banking and fintech, behavioral biometrics for secure fintech onboarding, and continuous adaptive risk to get there faster.
Further reading tailored to fintech leaders
Solution overview: fintech solution page
Industry article: "Hidden Threats in Fintech"
Core techniques: "How Does Fingerprinting Work?" and "Device Fingerprinting" and "Behavioral Biometrics"
Program approach: "Continuous Adaptive Risk and Trust Assessment" and "Fraud Risk Management"
Onboarding risk: "The Growing Threat of Account Opening Fraud" and "New Account Fraud"
ATO details: "The Anatomy of Account Takeover" and "Uncover the Threats WAF and MFA Miss"
Further reading tailored to fintech leaders
Solution overview: fintech solution page
Industry article: "Hidden Threats in Fintech"
Core techniques: "How Does Fingerprinting Work?" and "Device Fingerprinting" and "Behavioral Biometrics"
Program approach: "Continuous Adaptive Risk and Trust Assessment" and "Fraud Risk Management"
Onboarding risk: "The Growing Threat of Account Opening Fraud" and "New Account Fraud"
ATO details: "The Anatomy of Account Takeover" and "Uncover the Threats WAF and MFA Miss"
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Most programs win by binding identity to the real device and recomputing risk at each sensitive step. CrossClassify adds device fingerprinting and behavioral biometrics to deliver just in time step up and stop takeovers without blanket friction. Read more: "The Anatomy of Account Takeover"
Link accounts by persistent device identity and navigation rhythm rather than blunt IP rules. CrossClassify collapses clusters with device fingerprinting and continuous risk so you throttle only the ring while letting legitimate signups through. Learn how fingerprinting works: "How Does Fingerprinting Work?"
Treat help desk interactions as identity events and enforce cooling periods after contact edits. CrossClassify fuses support metadata into adaptive risk so resets immediately after edits trigger verification instead of blind trust. Approach details: "Continuous Adaptive Risk and Trust Assessment"
Use proximity between beneficiary changes and payout attempts, device trust, and session behavior. CrossClassify's real time risk scoring pauses only the risky payouts and releases trusted ones automatically. Program patterns: "Fraud Risk Management"
Watch for BIN specific mismatch waves and headless agent traffic on the on ramp. CrossClassify combines velocity checks, bot intelligence, and device identity to block tests at source. Gaps WAF and MFA miss: "Uncover the Threats WAF and MFA Miss"
Hash documents, anchor applicants to devices, and compare behavior across submissions. CrossClassify ties document reuse to device reuse and steps up KYC only where evidence supports it. Overview: "The Growing Threat of Account Opening Fraud"
Target automation signals such as session depth, cadence, and device clustering, not broad segments. CrossClassify's device fingerprinting and behavioral models separate organic traffic from farms so marketing can scale safely. Foundations: "Avoid Fake Accounts"
Use it alongside device identity to verify the human behind the session without extra prompts. CrossClassify measures typing, field to field timing, and navigation rhythm to keep trusted users fast and flag impostors. Primer: "Behavioral Biometrics"
Adopt a policy layer that recomputes trust on every sensitive action and triggers the right control when needed. CrossClassify plugs into existing flows and delivers adaptive step up, beneficiary checks, or throttles based on live risk. Method: "Continuous Adaptive Risk and Trust Assessment"
Establish clear risk ownership, measurable KPIs, and audit ready controls. CrossClassify helps instrument evidence for every decision so risk reviews and audits run on data not anecdotes. Guide: "Fraud Risk Management"
Yes because MFA can be phished or socially engineered, while device identity persists and flags reuse across accounts. CrossClassify shows how fingerprinting complements MFA rather than replaces it. Learn more: "Device Fingerprinting"
Use a blended score of identity confidence, device trust, behavior consistency, and action sensitivity. CrossClassify's adaptive engine applies verification only when risk rises so conversion remains high. Framework: "Continuous Adaptive Risk and Trust Assessment"
Human cadence varies and respects throttle limits while bots create sharp micro bursts and repetitive sequences. CrossClassify monitors order rhythm and counterparty patterns to trigger protective throttles only for automated abuse. Insight: "Uncover the Threats WAF and MFA Miss"
SIEMs collect and visualize while dedicated risk engines drive in session decisions. CrossClassify feeds SIEM with high fidelity signals and closes the loop by acting on risk at the point of decision. Program view: "Fraud Risk Management"
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
