Last Updated on 26 Aug 2025
Behavioral biometrics for fraud prevention and cybersecurity
Share in
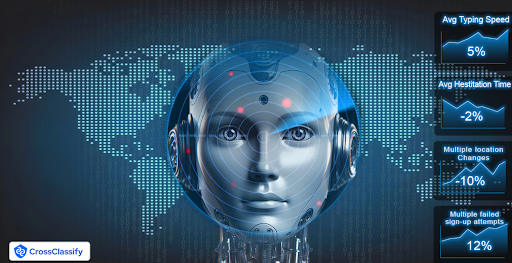
Key Notes
•
The average cost of a data breach reached about 4.88 million dollars per incident in 2024, which keeps rising year over year, according to IBM's Cost of a Data Breach Report.•
The human element, including phishing and misuse of credentials, contributes to about 68 percent of breaches.•
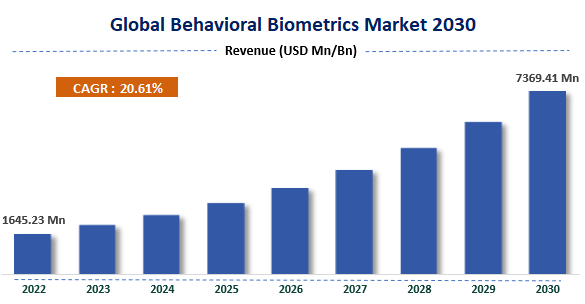
Analysts estimate the behavioral biometrics market to grow from about 1.65 billion dollars in 2022 to about 7.37 billion dollars by 2030, a compound annual growth rate near 20 percent Zion Market Research.
Introduction to behavioral biometrics authentication and digital identity
Behavioral biometrics analyzes how people interact with devices and applications to verify identity continuously in the background. Instead of measuring faces or fingerprints, it learns unique interaction patterns such as keystroke cadence, mouse trajectory, touch pressure and navigation flow. This approach strengthens digital identity by detecting anomalies within live sessions rather than at login alone. With breach costs continuing to climb and attackers industrializing account takeover, continuous behavioral signals help distinguish legitimate users from bots, malware and social-engineered imposters without adding friction. The urgency is underscored by industry research that places the average breach at about 4.88 million dollars and shows most incidents still involve human factors like phishing and weak credentials.
Comparison with physiological methods, physiological vs behavioral biometrics, pros and cons
Physiological approaches such as face and fingerprint are strong for initial proofing but are vulnerable when credentials or tokens are phished or when a device or session is hijacked. Behavioral biometrics complements those checks by analyzing how a trusted user normally types, taps and navigates, surfacing deviations inside a session. It is privacy supportive when designed with minimization because it relies on patterns, not raw content or images. It improves security while reducing interruptions since it works passively most of the time and asks for step up only when risk rises. For a deeper look at attacks that bypass traditional gates, see CrossClassify's guide to account takeover.
How continuous and passive models differ from static checks, continuous authentication using behavioral biometrics
Static authentication verifies once, then trusts the session. Continuous behavioral analytics monitors throughout the journey and recalculates risk as context changes. That difference is critical for defending against session hijacking, remote help desk scams and SIM swap fallout, where the adversary appears legitimate at login but diverges during high risk actions. CrossClassify explains continuous and adaptive risk in depth. Continuous models preserve user experience by remaining passive during low risk activity and escalating to stronger verification only when anomalies breach policy.
Where the behavioral biometrics market is heading and why fraud teams care
Adoption is rising because risk teams need tools that spot synthetic users, bot farms and social engineering without more friction for trusted customers. Market analysts project behavioral biometrics to exceed 7.3 billion dollars by 2030 as banks, fintechs, gaming and ecommerce deploy continuous verification. Vendors are moving beyond single signal classifiers to ensembles that fuse behavior with device intelligence and geo velocity. Fraud teams care because this fusion measurably reduces account takeover, new account fraud and chargeback abuse while lowering manual review. See industry growth estimates at Zion Market Research.
Applications and market landscape for behavioral biometrics solutions
Behavioral biometrics is used wherever identity must be confirmed silently during sensitive actions like money movement, credential change or high value checkout. Banks and fintechs apply it to protect transfers and payout changes. Ecommerce and marketplaces use it to stop scripted signups, coupon abuse and return fraud. Gaming and media rely on it to detect bots, collusion and farmed accounts without degrading play. Public sector and healthcare apply continuous checks to protect portals and sensitive records while meeting compliance obligations.
Growth is fueled by the need to reduce breach impact and to address the 68 percent human factor in incidents with a control that works even when users are tricked. Solutions are often bought by security, fraud and product teams together so that risk decisions can be orchestrated without adding hard friction for legitimate users. Platform categories include behavior analytics SDKs, device and identity intelligence clouds, and orchestration layers that integrate with existing MFA and SSO. Headlines increasingly highlight bank programs that combine layered signals to flag scam-induced transfers in real time. For related background on new account fraud, see CrossClassify at guide on new account fraud and article on avoiding fake accounts.

Growth is fueled by the need to reduce breach impact and to address the 68 percent human factor in incidents with a control that works even when users are tricked. Solutions are often bought by security, fraud and product teams together so that risk decisions can be orchestrated without adding hard friction for legitimate users. Platform categories include behavior analytics SDKs, device and identity intelligence clouds, and orchestration layers that integrate with existing MFA and SSO. Headlines increasingly highlight bank programs that combine layered signals to flag scam-induced transfers in real time. For related background on new account fraud, see CrossClassify at guide on new account fraud and article on avoiding fake accounts.

Technology foundations, signals and patterns
Behavioral analytics depends on signal quality, modeling strategy and privacy by design. It strengthens security by learning a user's stable patterns while allowing for natural variation over time and across devices. The strongest deployments do not rely on a single metric; they use ensembles that correlate behavior with device, network and journey context. CrossClassify also fuses device intelligence to improve accuracy and reduce false positives, which is detailed at our article on device fingerprinting and our guide on how fingerprinting works.
Data signals and behavioral patterns
- Keystroke dynamics:
Keystroke dynamics focuses on how a person types, not just how fast. Systems learn a user's rhythm across dwell time (how long a key is held) and flight time (time between releasing one key and pressing the next), along with pressure, typical error rate, and even preferences such as left- or right-shift usage. During a session, the live pattern is compared against historical behavior to surface anomalies like sudden slowness, excess errors, or machine-like cadence. Even for new users, overly even or rapid typing can signal automation and bots. - Mouse movement:
Behavioral engines observe pointer location over time, curvature of trajectories, speed changes, and click timing or pressure to profile how a person actually uses a mouse or touchpad. Small hand motions add up to a unique signature that distinguishes a legitimate user from a fraudster. Deviations such as unnaturally straight lines, erratic jitter that doesn't match the user's past sessions, or switching from an external mouse to only touchpad with very different motion can be flagged for review or step-up. - Touch interaction:
On mobile and touch laptops, the system models how a user scrolls, taps, and swipes, including pressure, duration, and speed of gestures. Profiles also capture handedness cues such as a preference to scroll on one side of the screen. When pressure, gesture speed, or side of interaction shifts significantly during sensitive actions like payment or credential change, the session's risk rises and additional checks can be triggered without breaking the flow. - Motion sensors:
Behavioral biometrics can also learn device movement patterns using the phone's gyroscope and accelerometer to understand orientation, rotation, and acceleration. Typical "carry" states and grip style become part of a baseline for the legitimate user. If sensor streams show an unexpected posture or movement profile at odds with prior sessions, the system can require re-authentication or other verification before allowing high-risk actions. - Navigation flow:
Beyond individual signals, behavior is evaluated across the full session: how users progress through pages, time they spend on steps, and the sequence of actions during onboarding or checkout. Continuous, passive monitoring makes it possible to detect anomalies that appear after login—like an unusual path to add a new payee or a scripted, zero-depth registration flow. Patterns consistent with account takeover or new-account bots can be surfaced in real time and routed to investigation or step-up controls with minimal friction for legitimate customers.
Model strategies
- Ensemble learning: Blending specialized models for keystrokes, pointers and touch reduces variance and resists single signal evasion. Ensembles assign calibrated weights that adapt by channel and action.
- Drift handling: Profiles evolve as users change devices or habits. Robust systems apply rolling baselines and forget old data gracefully to avoid brittleness while staying sensitive to true anomalies.
- Device change tolerance: Models should distinguish a legitimate new device from a mule device farm. Cross linking to device intelligence lowers friction for true users and raises scrutiny for risky clusters.
- Passive versus active: Passive behavioral biometrics monitors silently until policy thresholds are crossed. Only then does the system request a step up, preserving conversion while controlling risk.
Device intelligence fusion
- Device fingerprinting:
Correlating user behavior with a persistent device identity raises confidence and collapses fraud rings that cycle credentials. A high fidelity fingerprint can include stable signals such as hardware model, OS build, browser entropy, font and canvas characteristics, sensor availability, time zone, and TLS stack traits. When the same device appears behind many new accounts or returns with slightly altered attributes, clustering exposes synthetic umbrellas that would otherwise look unrelated. Pairing the fingerprint with behavioral profiles lets you distinguish a trusted customer on a new device from a mule device farm reusing scripted flows. See a deeper overview. - Geo and velocity:
Location and movement context add another dimension to risk scoring. Improbable travel, sudden ASN category shifts from residential to hosting, or geo hopping during a live session are strong precursors to account takeover and payout diversion. When these geo anomalies occur at the exact moment behavior patterns drift from a user's baseline, the combined signal produces a precise step up trigger without blocking legitimate customers. Geo velocity also helps detect session handoffs where an attacker proxies through a new region to finalize a high value action. - Link analysis:
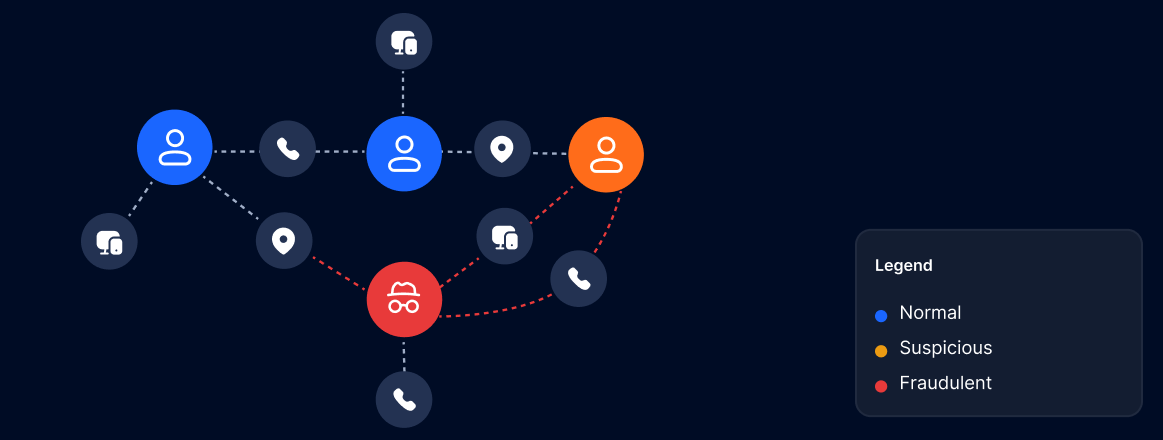
Graphing relationships across devices, accounts, emails, phone numbers, cards, and bank destinations connects entities that try to stay separate. Many to one payout hubs, shared hardware across multiple KYC identities, and repeated contact details across applications reveal organized abuse at scale. Link analysis enriches every behavioral decision by adding cluster context, so a borderline session tied to a known mule network is automatically escalated while an isolated anomaly can be allowed with monitoring. Combining link scores with device intelligence and geo velocity produces evidence ready for case management and dispute response.
Deployment and SDK considerations
- Mobile and web SDKs
CrossClassify's mobile and web SDKs are designed for high-risk journeys where latency, reliability and privacy all matter. Capture only the minimum behavioral inputs needed to build robust features, then transform them on the client into compact, derived vectors that never include raw text, images or field contents. The SDKs batch events intelligently, honor app frame rates, back off under load, and buffer securely when the device is offline so sessions remain coherent. Integration patterns support synchronous scoring for login, credential change, payout setup and checkout, plus asynchronous analysis for lower priority flows. For an end-to-end view of event capture, risk scoring and orchestration, see the integration flow. - Privacy by design
Behavioral analytics only works at scale when privacy is first class. Engineer for data minimization: collect interaction timings, trajectories and device context that are useful for modeling, and avoid content altogether. Generate and transmit derived features rather than raw keystrokes or form data, apply on-device redaction for sensitive screens, and support regional consent modes so capture aligns with user choices. Provide clear, human-readable notices and maintain configurable retention so you keep just enough history to learn a baseline without storing excess. CrossClassify documents these principles and the controls behind them. - Integration patterns and orchestration
Use lightweight SDK hooks to start and stop capture around risky steps, then call the risk API for a calibrated score and reason codes. Tie outcomes to your existing SSO and MFA so step up happens only when risk crosses a policy threshold, and use webhooks to trigger holds on payouts, password edits or high-value actions. The "How it works" guide shows common blueprints for inline decisions, queue-based review, and evidence-pack generation that explain exactly which signals drove a decision: How it works. - Security and data protection
Protect every stage of the pipeline. Encrypt in transit with modern TLS, encrypt at rest with strong keys and rotation, restrict access through least-privilege roles and administrative SSO, and log every access for audit. Support private connectivity patterns, data-residency choices and environment isolation so development and production never mingle. Detailed program controls, including retention management, key handling, vulnerability management and incident response, are outlined at CrossClassify’s data security overview. - Performance, resilience and observability
Behavioral capture must be invisible to users. Keep CPU and memory footprints small, stream features in compact payloads, and hold p95 decision latency within your UX budget for login and payment paths. Ship versioned SDKs with remote kill switches, feature flags and graceful degradation so you can pause capture or roll back safely if conditions change. Export health, error and decision metrics to your observability stack, and align alerting with your SOC so anomalies are detected early. Reference integration best practices and security expectations. - Governance and compliance
Back modeling with governance: document lawful bases, support data subject requests, and keep reproducible model versions with audit trails for every score used in production. Calibrate retention by jurisdiction, run bias and drift checks, and ensure acceptable-use constraints limit signals to fraud and security purposes. CrossClassify's security and privacy posture, including organizational and technical safeguards, is summarized at CrossClassify’s data security page.
Real world cases of behavioral biometrics fraud detection
Financial institutions use behavioral analytics to stop account takeover where stolen credentials would otherwise pass traditional checks. When a login appears typical, the system monitors transfer setup and payout edits for behavior shifts that signal coercion or remote control. Ecommerce companies apply behavior to block scripted signups, coupon farming and cart testing without harming real customers. Gaming platforms detect bot play and collusion by measuring reaction time distribution and input entropy across sessions. These results are strongest when behavior is fused with device fingerprinting and link analysis so that shared hardware and payout hubs are visible to risk teams. For related ATO patterns, see CrossClassify at the anatomy of account takeover.
Case archetypes
- Account takeover interdiction in online banking: A user logs in with a valid password, but typing rhythm and navigation path diverge as the attacker moves to add a new payee. Step up MFA is triggered before funds move.
- Account takeover interdiction in online banking: A user logs in with a valid password, but typing rhythm and navigation path diverge as the attacker moves to add a new payee. Step up MFA is triggered before funds move.
- Checkout bot suppression in ecommerce: Session input shows machine like stability and zero browsing depth prior to promo redemption. The flow is throttled and challenged, preserving inventory for real customers.
- Payout diversion in fintech: Contact detail change is followed by behavior shifts and a new beneficiary. The system pauses the payout and routes the case to review with evidence linking device and address reuse.
Consequences of not deploying behavioral biometrics for fraud and data breach
Session exposure between login and payout:
Static checks verify only once at the beginning of a session. Attackers use remote access tools, SIM swaps, or social engineering to take control after login and then change payees, reset credentials, or drain balances. Without continuous behavior analysis, the system treats the attacker as the account owner during these high risk steps. This creates a gap where funds move and audit trails still look legitimate.
Direct financial losses and recovery costs:
Missing behavioral signals increases account takeover, refund abuse, and payout diversion. Losses include principal, chargeback fees, dispute handling time, and operational headcount for manual reviews. Fraud rings repeat the same play across many accounts before detection, multiplying the hit. Once funds leave to mule hubs, recovery odds drop sharply.
Soaring manual review queues and false positives:
Coarse rules based on device or IP create many borderline alerts that require human review. Teams spend time triaging good users while true fraud slips through. Approval rates fall, unit economics worsen, and customers abandon checkout due to unnecessary friction. Behavioral scoring would separate natural human patterns from automation and reduce noise.
Regulatory, audit, and brand liabilities:
In regulated sectors, repeated disputes and poor payment hygiene trigger findings and fines. Failure to apply proportionate controls during high risk actions can jeopardize compliance programs and increase oversight. Publicized scams lead to consumer advisories, negative press, and claims that consume legal resources. The brand pays twice through penalties and lost trust.
Customer churn and lifetime value erosion:
Victims of takeover or scam induced transfers often blame the platform even when credentials were phished elsewhere. They close accounts, reduce usage, and warn peers. Heavy friction added to compensate for weak detection also drives abandonment. Behavioral analytics preserves smooth experiences for trusted users while stopping the small fraction of risky sessions.
Scaling of organized abuse and ring activity:
When detection depends only on credentials or IP, adversaries industrialize with device farms and synthetic identities. They automate signups, bonus abuse, and payout routing at volume. Lack of behavior and link intelligence allows clusters to operate for months, turning small leaks into systemic losses.
Operational fatigue and talent burnout:
Large alert backlogs and frequent incident spikes push fraud and support teams into constant firefighting. Expert analysts spend time on repetitive checks instead of strategic improvements. Hiring more reviewers becomes the default response, raising cost without improving outcomes. Behavior driven prioritization focuses effort on the few sessions that truly matter.
Limited forensics and weak evidence for disputes:
After an incident, teams need to prove what happened and when. Without behavioral telemetry, cases rely on logs that show only that a valid session executed an action. This weakens chargeback representment and recovery. Behavioral timelines provide clear evidence of abnormal input patterns, session handoffs, and coercion.
Product roadmap drag and lost revenue:
Persistent fraud forces teams to delay features like instant payouts, high value promos, or frictionless onboarding. Risk appetite shrinks, reducing conversion and competitiveness. Mature behavioral controls unlock these growth levers safely by gating only the risky micro moments rather than entire user segments.
Compounding data breach impact:
Stolen credentials are inevitable in the current threat landscape. Without behavior based defenses, every breach elsewhere converts into active compromise on your platform. Attackers test lists, find hits, and move quickly before detection. Continuous monitoring limits credential reuse and reduces the blast radius from external incidents.
Static checks verify only once at the beginning of a session. Attackers use remote access tools, SIM swaps, or social engineering to take control after login and then change payees, reset credentials, or drain balances. Without continuous behavior analysis, the system treats the attacker as the account owner during these high risk steps. This creates a gap where funds move and audit trails still look legitimate.
Direct financial losses and recovery costs:
Missing behavioral signals increases account takeover, refund abuse, and payout diversion. Losses include principal, chargeback fees, dispute handling time, and operational headcount for manual reviews. Fraud rings repeat the same play across many accounts before detection, multiplying the hit. Once funds leave to mule hubs, recovery odds drop sharply.
Soaring manual review queues and false positives:
Coarse rules based on device or IP create many borderline alerts that require human review. Teams spend time triaging good users while true fraud slips through. Approval rates fall, unit economics worsen, and customers abandon checkout due to unnecessary friction. Behavioral scoring would separate natural human patterns from automation and reduce noise.
Regulatory, audit, and brand liabilities:
In regulated sectors, repeated disputes and poor payment hygiene trigger findings and fines. Failure to apply proportionate controls during high risk actions can jeopardize compliance programs and increase oversight. Publicized scams lead to consumer advisories, negative press, and claims that consume legal resources. The brand pays twice through penalties and lost trust.
Customer churn and lifetime value erosion:
Victims of takeover or scam induced transfers often blame the platform even when credentials were phished elsewhere. They close accounts, reduce usage, and warn peers. Heavy friction added to compensate for weak detection also drives abandonment. Behavioral analytics preserves smooth experiences for trusted users while stopping the small fraction of risky sessions.
Scaling of organized abuse and ring activity:
When detection depends only on credentials or IP, adversaries industrialize with device farms and synthetic identities. They automate signups, bonus abuse, and payout routing at volume. Lack of behavior and link intelligence allows clusters to operate for months, turning small leaks into systemic losses.
Operational fatigue and talent burnout:
Large alert backlogs and frequent incident spikes push fraud and support teams into constant firefighting. Expert analysts spend time on repetitive checks instead of strategic improvements. Hiring more reviewers becomes the default response, raising cost without improving outcomes. Behavior driven prioritization focuses effort on the few sessions that truly matter.
Limited forensics and weak evidence for disputes:
After an incident, teams need to prove what happened and when. Without behavioral telemetry, cases rely on logs that show only that a valid session executed an action. This weakens chargeback representment and recovery. Behavioral timelines provide clear evidence of abnormal input patterns, session handoffs, and coercion.
Product roadmap drag and lost revenue:
Persistent fraud forces teams to delay features like instant payouts, high value promos, or frictionless onboarding. Risk appetite shrinks, reducing conversion and competitiveness. Mature behavioral controls unlock these growth levers safely by gating only the risky micro moments rather than entire user segments.
Compounding data breach impact:
Stolen credentials are inevitable in the current threat landscape. Without behavior based defenses, every breach elsewhere converts into active compromise on your platform. Attackers test lists, find hits, and move quickly before detection. Continuous monitoring limits credential reuse and reduces the blast radius from external incidents.
Privacy, ethics and compliance for behavioral biometrics
Behavioral analytics can be privacy supportive when built with intentional limits and clear governance. Data minimization focuses on patterns rather than raw content and stores derived features with strict retention. Teams should document lawful bases, transparency notices and opt out pathways consistent with regional laws. Model governance includes measurement for bias, reproducibility of scores and audit logging for all risk decisions. Clear acceptable use guidelines ensure signals are applied only to fraud prevention and security, not unrelated profiling.
Why MFA and WAF are not enough for modern threats
Traditional controls like web application firewalls and multi factor prompts stop many commodity attacks, but sophisticated adversaries route around them. Social engineering can coerce victims to complete MFA challenges, and application layer automation can look human enough to sidestep simple defenses. Continuous behavior with device and link intelligence closes the gap by watching how actions are performed, not just whether a code was entered. CrossClassify details the blind spots and the layered approach required in this article on WAF and MFA blind spots. For complementary reading, see CrossClassify’s article on device fingerprinting and guide to continuous adaptive risk and trust assessment (CARTA).
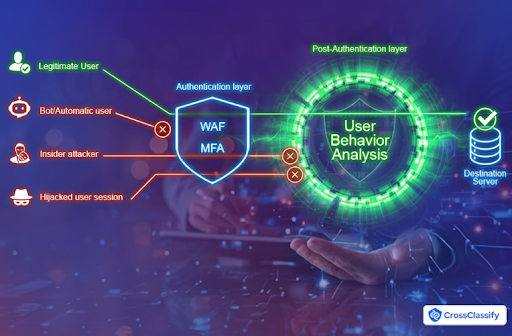

How CrossClassify protects with behavioral biometrics solutions
CrossClassify delivers a layered behavioral engine tuned to the riskiest journeys, including login, credential change, payout setup and high value checkout. Our models analyze keystroke cadence, pointer dynamics, touch interactions, motion sequences and navigation flow, then fuse those with device intelligence, geo velocity and link analysis. Policies orchestrate step up MFA and SSO only when needed, preserving conversion and customer satisfaction. Evidence packs make disputes and internal reviews faster by showing the precise signals that triggered decisions. To learn more about fraud program design, see fraud risk management and our overview on behavioral analytics.
CrossClassify signal fusion
- Device and geo intelligence: Binding identity to device while checking improbable travel and risky networks improves precision and reveals multi account rings. Read more at device fingerprinting.
- Link and velocity analysis: Shared devices, addresses and payout accounts connect clusters and expose synthetic umbrellas that hide inside volume. See account opening risks at the growing threat of account opening fraud.
Industry playbooks: Behavioral biometrics in action
Healthcare
Protect patient portals, telehealth, e-prescribing and EHR access where stolen credentials and social engineering can expose PHI. Behavioral biometrics profiles how staff and patients normally type, tap and navigate, then flags anomalies during sensitive actions such as prescription changes, record exports and insurance updates. Fusing behavior with device intelligence and geo velocity helps catch session hijacking and shared workstations used outside shift patterns, without slowing legitimate care.
- Top threats we stop: patient portal takeover, insider misuse, telehealth session hijacking, prescription diversion, bot registration.
- Behavioral signals we watch: keystroke cadence on e-prescribe forms, navigation flow through chart views, touch dynamics on mobile check-in, improbable travel during live sessions.
- What you get: fewer PHI exposures, lower manual review, audit-ready evidence for HIPAA investigations.

Fintech
Money movement, payout edits and limit changes are the highest risk moments in digital finance. Behavioral biometrics detects subtle deviations that occur when an impostor uses a good password or coerces a victim to add a new payee. Combined with device fingerprinting, link analysis and geo checks, the system pauses risky transfers, challenges step up only when necessary and reduces dispute losses.
- Top threats we stop: account takeover, payout diversion, card testing on on-ramps, refund abuse.
- Behavioral signals we watch: typing rhythm on beneficiary forms, unusual path to limits, touch pressure changes at step-up screens, rapid retries with machine-like timing.
- What you get: fewer chargebacks, less friction for trusted users, faster investigations with behavioral evidence.
Crypto
Exchanges and wallets face fast moving attacks such as API key abuse and withdrawal to tainted addresses. Behavioral biometrics monitors order entry, credential edits and withdrawal setup to catch bot cadence, session handoffs and coached victims, before assets leave the platform. Linking behavior to device and network reputation tightens controls without hurting pro traders.
- Top threats we stop: exchange account takeover, rogue trading bots, API key compromise, mixer adjacency cash-outs, promotion abuse.
- Behavioral signals we watch: orders per second against throttle, navigation anomalies to withdrawal allowlists, touch patterns during 2FA edits, abrupt mouse trajectories at API key pages.
- What you get: safer withdrawals, fewer frozen false positives, clear trails for compliance teams.
Travel
OTAs, airlines and hotels battle credential stuffing, loyalty fraud, refund loops and rate scraping. Behavioral biometrics separates real travelers from bots by analyzing zero depth sessions, machine-like inputs and odd paths to voucher and refund pages. The result is stronger account protection and better fare integrity with minimal friction.
- Top threats we stop: account takeover of loyalty wallets, coupon and voucher farming, refund abuse, large scale scraping of fares and availability.
- Behavioral signals we watch: session depth before redemption, pointer jitter on passenger details, keystroke cadence at payment, geo velocity during itinerary changes.
- What you get: protected loyalty balances, higher conversion on trusted customers, reduced call center load.
iGaming
Operators must detect automated play, collusion and bonus abuse while keeping gameplay smooth. Behavioral biometrics measures reaction time distribution, input entropy and session pacing to expose bots and coordinated rings. Tied to device and link analysis, it collapses farms that recycle identities and wallets across promos.
- Top threats we stop: bonus abuse, bot gameplay, chip dumping and collusion, account takeover, self exclusion evasion.
- Behavioral signals we watch: reaction time variance, navigation flow to bonus endpoints, typing and touch changes at cash-out, improbable travel during live sessions.
- What you get: cleaner liquidity, fewer promo losses, stronger player protection controls.

Mining
Modern mining operations run on connected portals for contractors, procurement and OT monitoring. Behavioral biometrics protects privileged sessions by learning how operators and vendors normally work, then flagging anomalies during configuration changes, inventory adjustments and vendor payouts. Combined with device, geo and link intelligence, it curbs third party risk and internal misuse.
- Top threats we stop: contractor account abuse, off window configuration changes, inventory and PO manipulation, payout diversion to mule accounts.
- Behavioral signals we watch: navigation on OT dashboards, keystroke rhythm during config edits, session timing versus shift calendars, unusual paths to bank detail changes.
- What you get: fewer safety and compliance incidents, tighter third party access, audit-grade evidence for investigations.
Freight and Transportation
Broker, carrier and shipper portals are targets for double brokering, dispatch manipulation and ELD tampering. Behavioral biometrics detects accept then cancel games, orchestrators running many carriers from one device and abnormal flows to bank changes. It pairs behavior with device fingerprinting and link analysis to expose payout hubs and credential sharing.
- Top threats we stop: double brokering and impersonation, accept then cancel manipulation, account takeover of portals, payout diversion, ELD edit fraud.
- Behavioral signals we watch: session depth before tender acceptance, pointer patterns on document upload, cadence changes at bank edits, geo velocity mismatches during dispatch.
- What you get: cleaner carrier networks, fewer chargebacks and claims, stronger marketplace trust.
Supply Chain and Logistics
Supplier and buyer systems face synthetic onboarding, RFQ botting, PO edits after approval and inventory shrink. Behavioral biometrics reveals scripted registrations, zero depth quote harvesting and unusual navigation to approval overrides. When linked with device and link graphs, it uncovers multi account rings and shared payout targets early.
- Top threats we stop: fake supplier onboarding, RFQ scraping, PO and invoice manipulation, payout diversion, warehouse adjustment abuse.
- Behavioral signals we watch: keystroke and touch cadence on onboarding forms, session flow to approvals, timing anomalies near truck arrivals, device reuse across distinct tax IDs.
- What you get: resilient procurement, lower fraud loss, faster root cause analysis across sites.

Implementation playbook and ROI for behavioral biometrics
A successful rollout starts with a tight pilot that focuses on a few critical journeys and clear success criteria like fewer blocked good users and earlier interdiction of risky transfers. Teams should evaluate data coverage, calibrate thresholds and simulate policy changes before production. Integration patterns must meet latency budgets for login and checkout paths while allowing asynchronous analysis for lower priority flows. Change management is essential so operations, product and support teams understand alerts and can act quickly. The business case combines avoided fraud losses, reduced chargebacks, lower manual review and preserved conversion to calculate payback. For step by step guidance on continuous risk, see continuous adaptive risk and trust assessment and for device strategy see how does fingerprinting work.
Conclusions and next steps
Behavioral biometrics strengthens identity by evaluating how actions are performed throughout a session, not only who logged in. By analyzing keystrokes, gestures and navigation patterns, organizations can detect automation, session hijacking and social engineering at the moment of risk. The approach scales across banking, fintech, ecommerce, gaming and healthcare, and it is most effective when fused with device intelligence and link analysis. Industry research continues to show high breach costs and the dominant role of human factors, which makes continuous behavior an essential control rather than a nice to have.
CrossClassify operationalizes this approach with a production ready engine, low code policies and integrations that minimize friction for trusted users. Our platform pairs behavior with device fingerprinting, geo velocity, velocity checks and link analysis, then orchestrates just the right step up at the right time. Review our deep dives on account takeover, account opening risk, device intelligence, zero trust strategy and behavioral analytics.
CrossClassify operationalizes this approach with a production ready engine, low code policies and integrations that minimize friction for trusted users. Our platform pairs behavior with device fingerprinting, geo velocity, velocity checks and link analysis, then orchestrates just the right step up at the right time. Review our deep dives on account takeover, account opening risk, device intelligence, zero trust strategy and behavioral analytics.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Behavioral biometrics learns how real users type, swipe and navigate, then flags anomalies in live sessions to prevent imposters and bots. It works silently in the background, adding security without extra friction. CrossClassify enriches behavioral biometrics for online fraud prevention with device intelligence, geo velocity and link analysis to catch takeover attempts at payout edits and credential changes. Learn more: "Behavioral Biometrics"
Physiological methods verify what you are, while behavioral biometrics verifies how you act throughout the session. The second layer is crucial when MFA is phished or sessions are hijacked. CrossClassify combines behavioral biometric authentication with adaptive policies that trigger just-in-time step up when risk spikes. See why static gates miss threats: "Uncover the Threats WAF and MFA Miss"
In production, keystroke cadence, mouse trajectory, touch pressure and motion sensor sequences are high signal features. These behavioral biometrics in banking patterns expose scripted transfers, payout diversion and social-engineered sessions. CrossClassify fuses these behavioral biometrics patterns with device fingerprinting to cut false positives during money movement. Details: "Behavioral Biometrics"
Continuous models reevaluate risk at every step rather than trusting a single login event. This stops SIM swap fallout and remote desktop scams that appear legitimate at the door. CrossClassify orchestrates behavioral biometrics solutions with policy based step up and evidence packs so teams can act quickly. Read more: "Continuous Adaptive Risk and Trust Assessment"
Yes. Accuracy jumps when behavioral biometrics is fused with device identifiers, IP reputation and improbable travel checks. CrossClassify provides platforms combining behavioral biometrics with risk based authentication by binding users to trusted devices and isolating mule clusters. Get the device view: "Device Fingerprinting" and "How Does Fingerprinting Work?"
Modern ensembles reduce noise by mixing multiple signals and auto adapting to natural user change. Careful drift handling avoids brittle profiles and keeps friction low. CrossClassify tunes thresholds per journey to maximize the advantages of behavioral biometrics while minimizing manual review. Program design guidance: "Fraud Risk Management"
It detects machine-like inputs, zero depth sessions and coupon farming while letting trusted shoppers sail through. That means fewer blunt CAPTCHAs and fewer abandoned carts. CrossClassify applies behavioral biometrics fraud detection with velocity checks and risk scoring that only steps up when abuse is likely. Explore layered defenses: "Uncover the Threats WAF and MFA Miss"
Best practice is data minimization, storing derived features rather than raw text or images, and transparent notices. Proper governance ensures models are auditable and bias tested. CrossClassify implements privacy by design for behavioral biometrics technology, with controls aligned to modern zero trust architecture. See our approach: "Zero Trust Architecture and Modern AI Cybersecurity"
Most enterprises start with a focused pilot on risky flows like payout changes and limits updates, then expand. Integration works via lightweight web and mobile SDKs with policy orchestration. CrossClassify ships low code policies that align behavioral biometrics solutions with your MFA and SSO for immediate protection. Implementation tips: "Continuous Adaptive Risk and Trust Assessment"
Keystroke dynamics and pointer or touch analytics are widely deployed due to signal richness across devices. Isolated single metrics can be noisy, which is why ensembles outperform any one signal. CrossClassify uses multi signal models so no single weak behavioral biometrics example can sink accuracy. Foundations: "Behavioral Biometrics"
Prioritize vendors that prove lift on your top fraud journeys, measure false positive reduction and preserve UX. Include manual review savings and chargeback reduction in ROI. CrossClassify benchmarks behavioral biometrics solution market outcomes like fewer ATOs and lower dispute rates, then shares clear success criteria. Learn how to size value: "Fraud Risk Management"
Yes. Behavior shifts after profile edits, combined with device reuse and beneficiary convergence, expose mule networks early. CrossClassify correlates behavioral biometrics in banking with device graph and link analysis to pause risky payouts in real time. See related ATO mechanics: "The Anatomy of Account Takeover"
Scripted form fill shows robotic cadence, uniform error patterns and reused devices across many applications. These signals expose synthetic kits and farmed identities. CrossClassify pairs behavioral biometrics use cases with device binding to collapse identity umbrellas at onboarding. Deeper reading: "The Growing Threat of Account Opening Fraud" and "Avoid Fake Accounts"
Victims often navigate in unnatural sequences under attacker instruction, with hesitations near sensitive steps. Those micro patterns are reliable early warnings. CrossClassify detects these behavioral biometrics patterns and triggers human friendly step up that disrupts scams before money moves. Context: "Behavioral Biometrics"
When tuned correctly they remain invisible during low risk activity and only escalate when anomalies exceed thresholds. Latency is minimal because features stream efficiently. CrossClassify optimizes behavioral biometric authentication pipelines to meet strict mobile and web performance budgets. See continuous strategy: "Continuous Adaptive Risk and Trust Assessment"
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
