Supply chain and logistics
Protect supply chain platforms from identity and automation fraud
Protect onboarding, logins, and data access with continuous risk scoring

Stats on supply chain and logistics breaches
$445M
Fraud losses
In reported cargo fraud losses in recent years, with true supply chain losses estimated over $1B annually.
0in 3
Identity takeovers
Freight fraud cases involved identity takeovers, highlighting poor post-login protection.
$237085
Cargo theft
average cargo theft value, exposing vulnerability in supply chain authentication.
Why Supply chain Data Security Matters
Account takeovers disrupt supply chain operations at scale
Attackers hijack user and vendor accounts to redirect cargo or steal sensitive routing data. Our account takeover protection for supply chain systems detects abnormal behavior post-login, where most solutions fail.
Fake carrier accounts threaten supply chain integrity
Without strong identity validation, fraudsters register as carriers or suppliers. Our account opening fraud detection for logistics companies stops fake accounts before they impact your fulfilment chain.
Leaked credentials expose logistics portals to silent attacks
Stolen passwords and session tokens give attackers backdoor access to freight management systems. We deliver real-time supply chain fraud prevention by analyzing device, behavior, and session fingerprints.
Supply chain compliance failures carry growing financial risk
Frameworks like GDPR, CTPAT, and ISO demand robust fraud controls. Our supply chain data security compliance solution ensures you're protected and audit-ready across global operations.
Blog
Latest from Cross Classify
Solution
Issues We Resolve
We protect your app from the most prevalent cyber attacks
Account Takeover Protection in Supply Chain Systems
Stop Account Hijacks in Supply Chain Platforms
83%
of supply chain portals experienced at least one account takeover in recent years
$455M
in cargo theft losses linked to login-based impersonation fraud
How We Prevent Account Takeover
Prevent identity theft and data breaches caused by unauthorized access to user accounts. Account Takeover (ATO) attacks exploit vulnerabilities using tactics like impersonation, keylogging, smishing and phishing, and session hijacking, putting sensitive information and trust at risk.
Learn More ❯Continuous Monitoring for Supply Chain Platforms
Ensure 24/7 surveillance across your supply chain data and logistics workflows. Our system constantly tracks login activity, vendor behavior, and transactional anomalies across platforms, ensuring early detection of suspicious behavior. This feature supports real-time fraud risk scoring across every user and endpoint in your supply chain.
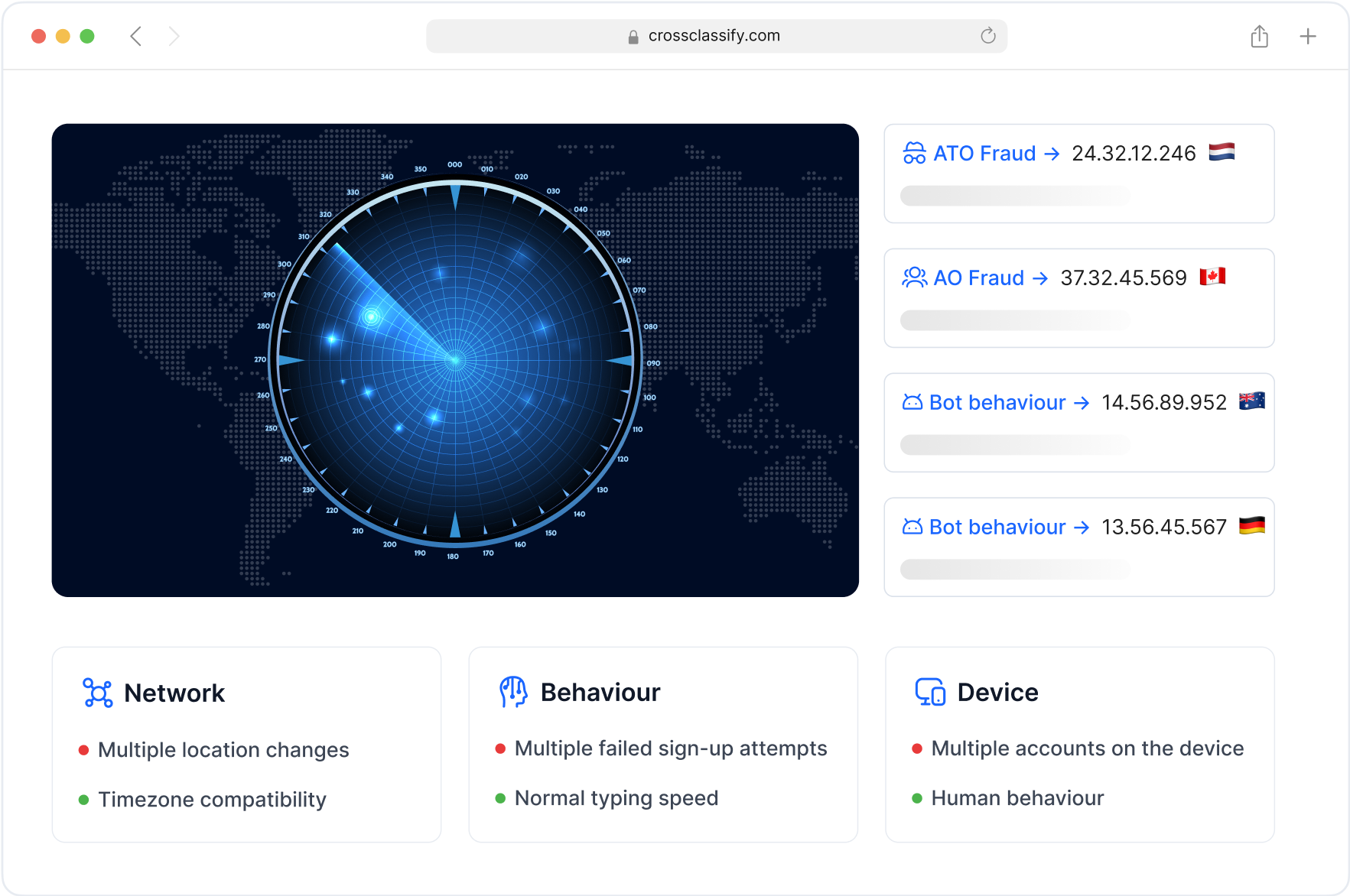
Behavior Analysis for Logistics Applications
Detect behavioral anomalies across warehouse staff, carrier accounts, and third-party vendors. Our behavior analysis for supply chain fraud detection identifies deviations in mouse movements, login timing, and session behavior to detect high-risk users even after login. This helps reduce impersonation and session hijacking in digital logistics environments.
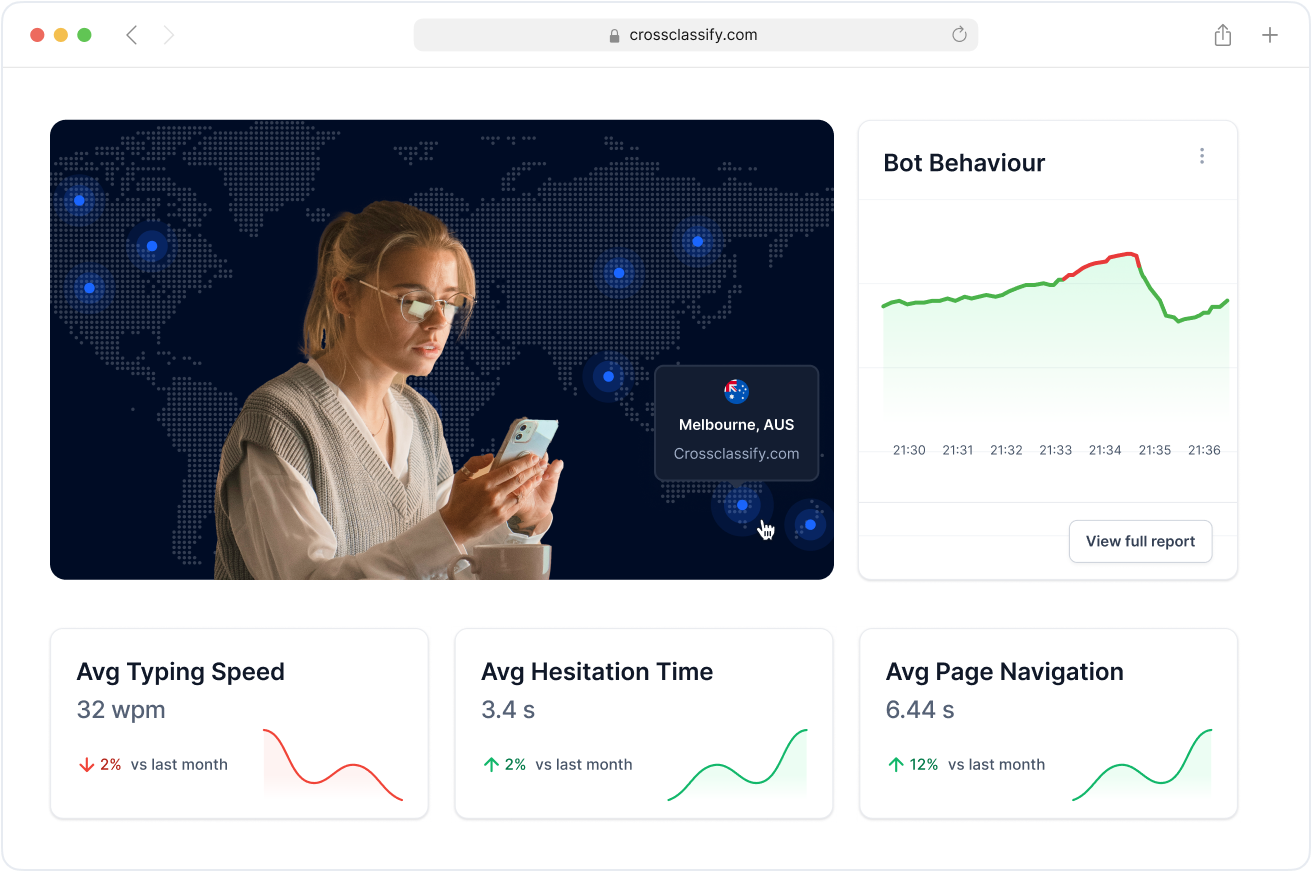
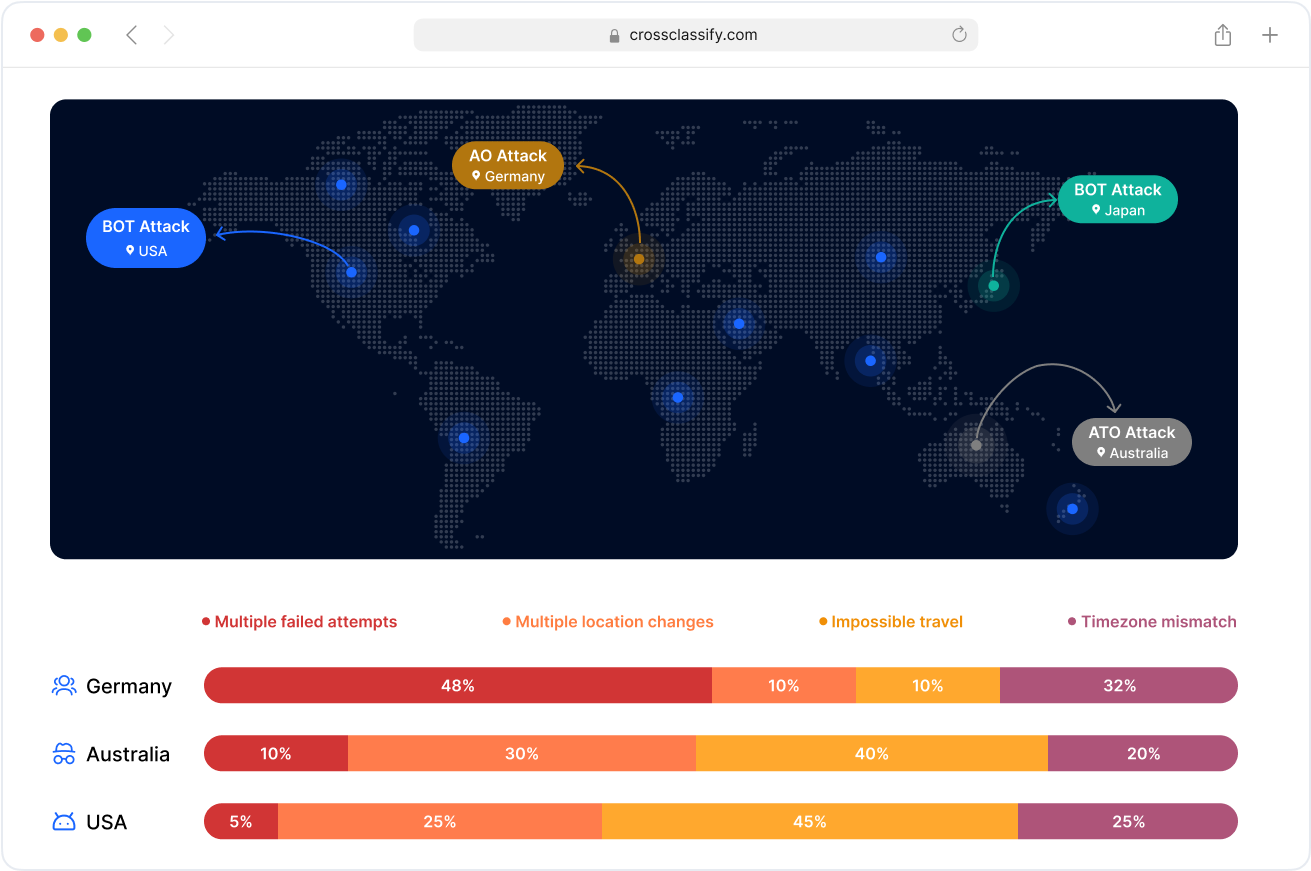
Geo Analysis in Supply Chain Access Control
Monitor access patterns across cross-border freight hubs, regional warehouses, and remote carrier logins. Our geo analysis for supply chain authentication identifies impossible travel, geo-inconsistencies, and spoofed IPs to reduce credential abuse and unauthorized entry into logistics systems.
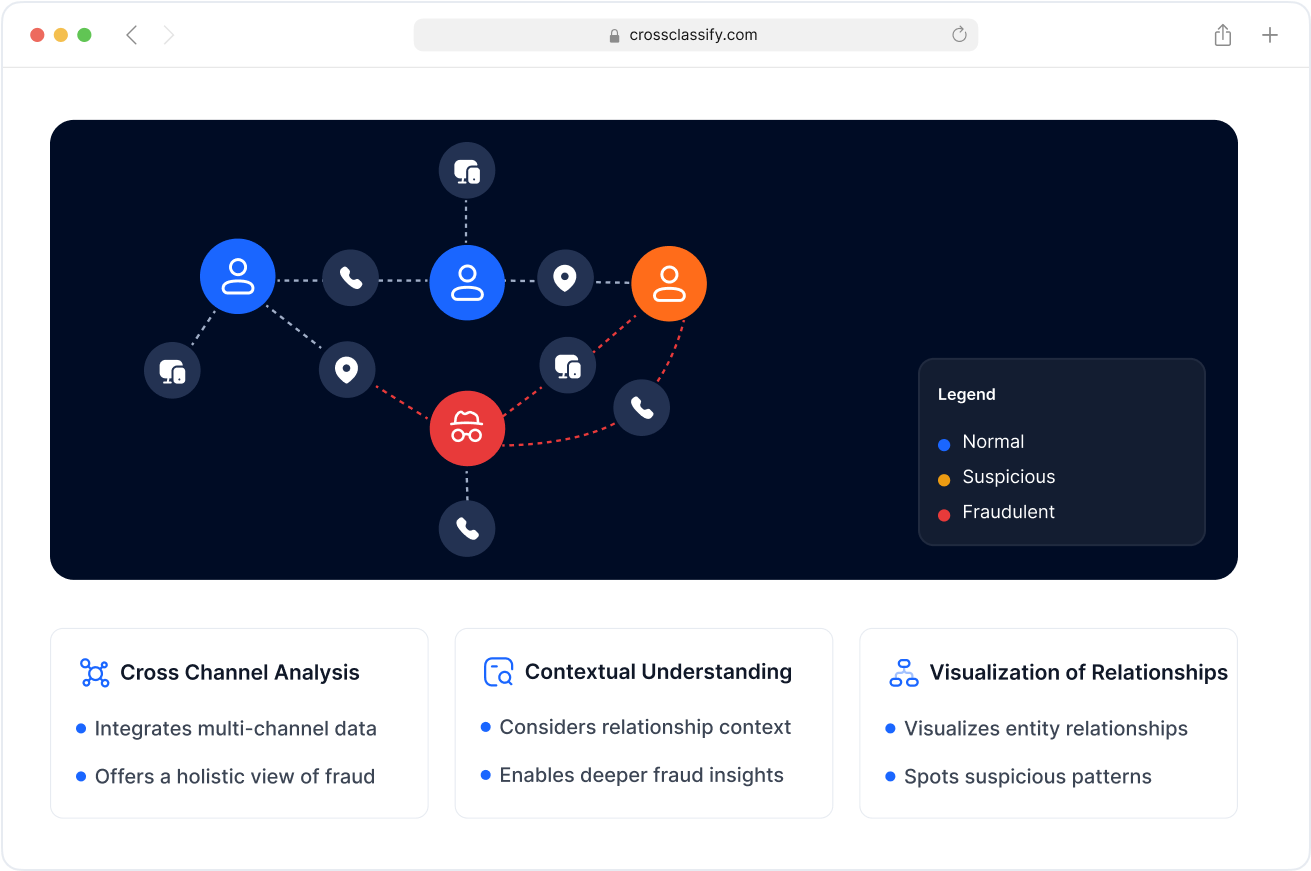
Link Analysis for Supply Chain Fraud Detection
Visualize and detect fraudulent relationships between carriers, suppliers, and transactional endpoints. Our link analysis for supply chain platforms maps connections between accounts, devices, and IP addresses to uncover coordinated fraud attempts and insider abuse.
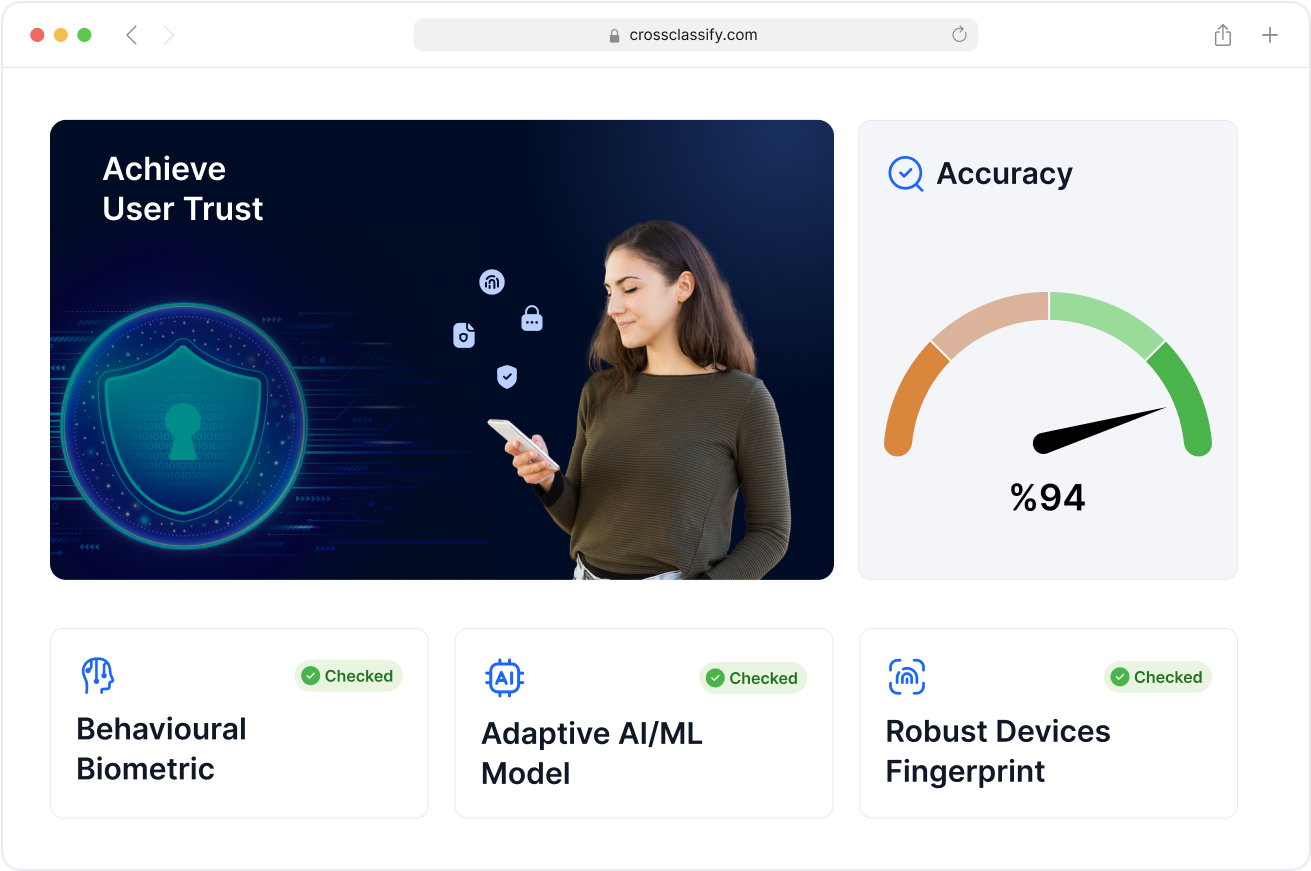
Enhanced Security and Accuracy for Supply Chain Transactions
Apply AI-driven verification to every user interaction across your logistics systems. Our engine improves the accuracy of fraud detection in supply chain portals, minimizing false positives while blocking real threats. Maintain operational uptime while strengthening fraud protection.
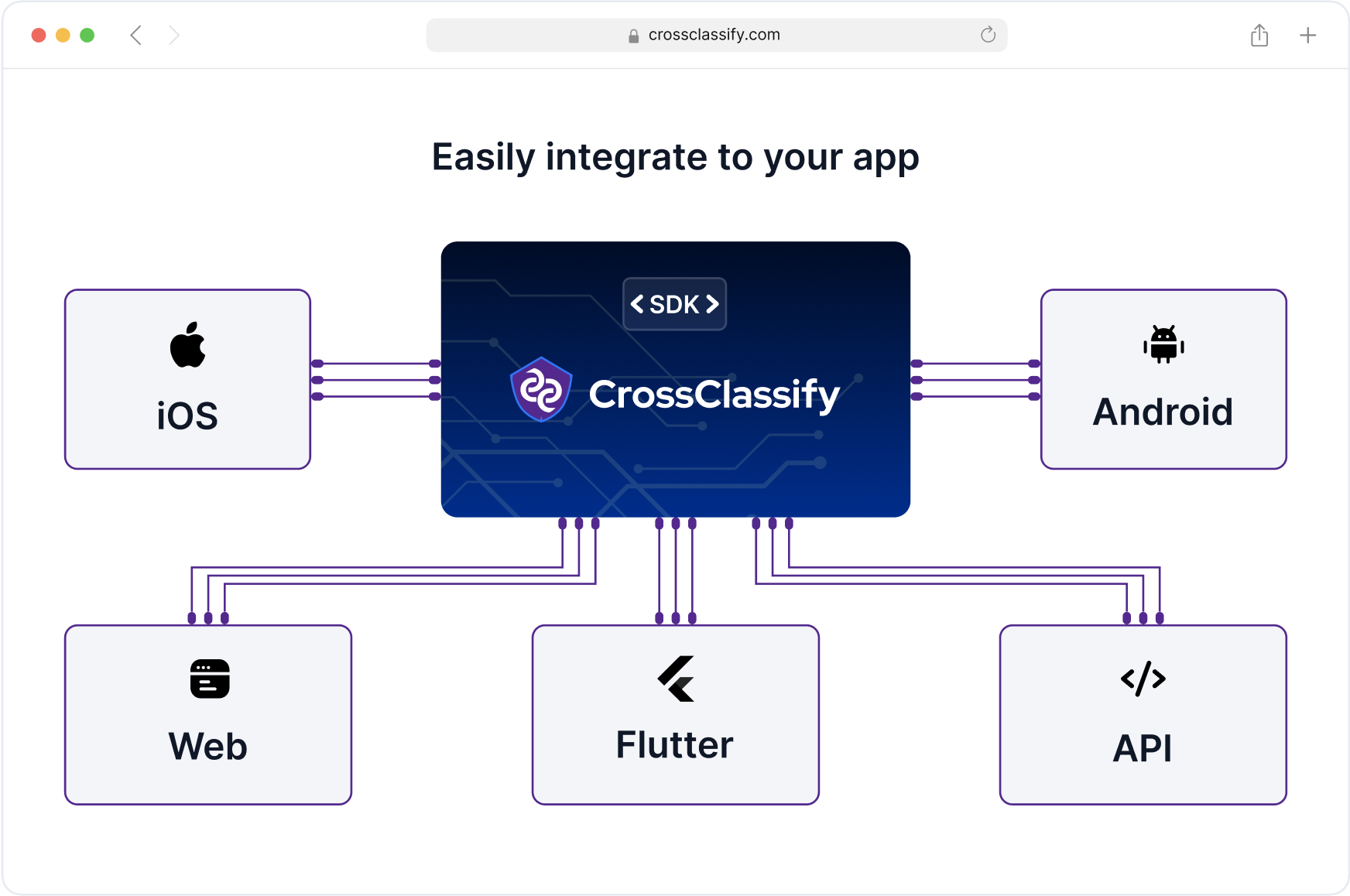
Seamless Integration with Supply Chain Systems
Integrate CrossClassify’s solution with your ERP, TMS, or WMS with minimal setup. Our fraud detection API for supply chain software is designed to work with existing infrastructure without disrupting fulfillment, procurement, or logistics workflows.
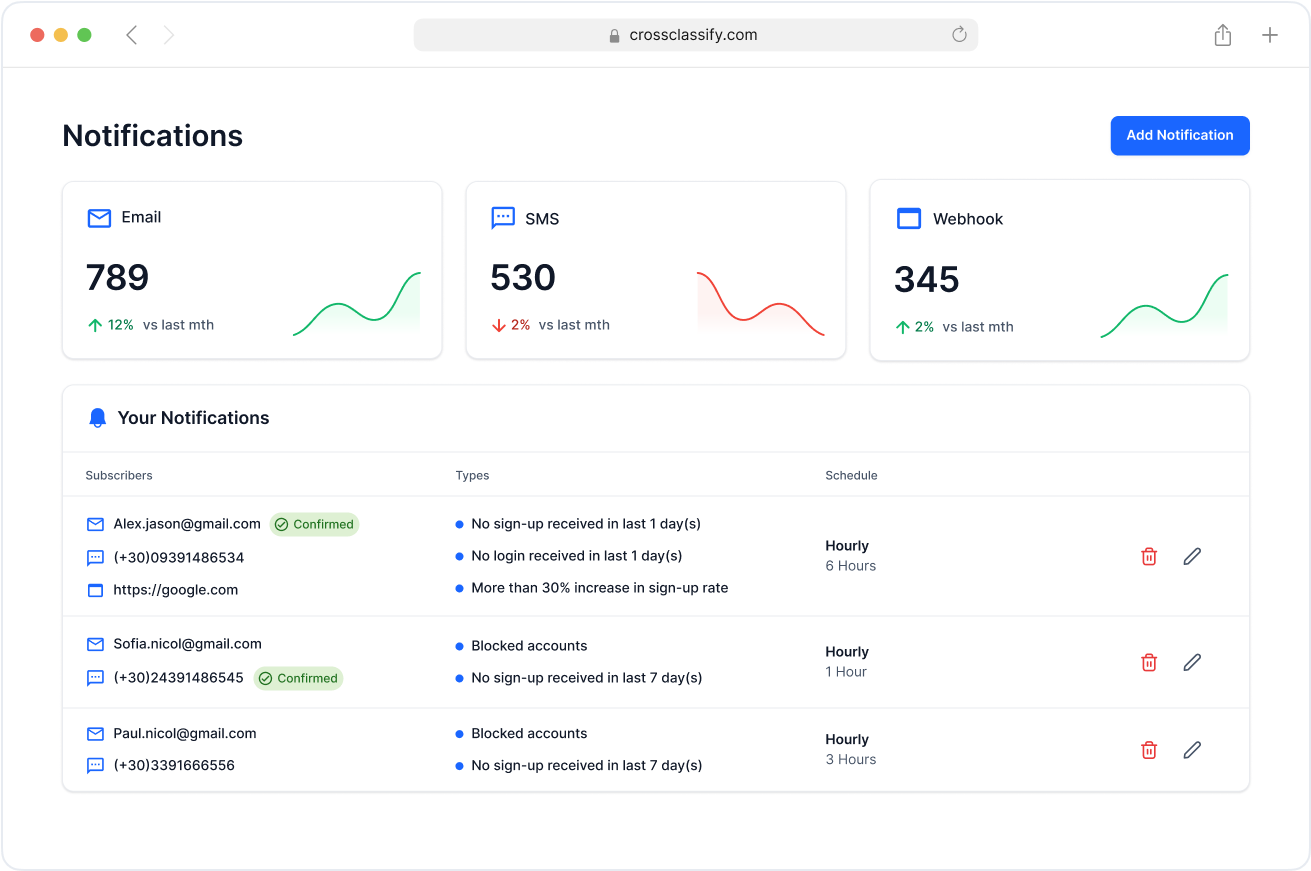
Alerting and Notification for Logistics Risk Management
Receive real-time alerts about suspicious logins, bot activity, or abnormal supplier behavior. Our fraud alert system for supply chain teams delivers actionable notifications to security and compliance officers, enabling rapid response to high-risk activity across vendor ecosystems.
Compliance
From Regulation to Reputation
GDPR - Protecting Cargo and Crew Data
Ensures protection of personally identifiable data collected during logistics operations, delivery tracking, and vendor communications in EU-bound shipments.
Global telecom/logistics firms have been fined up to €20 million or 4% of global turnover for breaches.
Beyond MFA for Supply Chains
Unlike basic MFA or WAF tools, CrossClassify delivers intelligent, behavior-based account takeover protection for logistics systems. Our fraud detection engine monitors post-login actions across supply chain platforms to detect insider threats and credential misuse. Traditional security solutions often miss these subtle anomalies, we catch what others ignore.
Supply Chain-Specific Intelligence
We tailor our fraud detection algorithms for supply chain fraud prevention, including fake carrier signups, credential stuffing on delivery portals, and insider abuse in warehouse systems. CrossClassify understands the multi-party nature of logistics platforms and models risk based on vendors, carriers, and fulfillment partners. Most tools apply generic models, we embed supply chain logic at the core.
Real-Time Risk Profiling
Our platform continuously analyzes user behavior, device fingerprinting, and geo-patterns to deliver real-time fraud prevention for supply chain apps. From login to fulfillment, we detect suspicious sessions before they escalate into data loss or stolen cargo. This proactive defense sharply reduces fraud loss compared to rule-based solutions.
Frequently asked questions
Read more at: The Anatomy of Account Takeover
Read more at: The Battle Against Fake Accounts
Read more at: Detecting Fraud with Device Fingerprinting
Read more at: Continuous Adaptive Risk and Trust Assessment
Read more at: Behavioral Biometrics
Read more at: Detecting Fraud with Device Fingerprinting
Read more at: Behavioral Biometrics
Read more at: Fraud Risk Management
Read more at: The Anatomy of Account Takeover
Read more at: How It Works
Let's Get Started
Elevate your Supply Chain and Logistics platform's security with CrossClassify. Schedule a personalized demo to see how we protect vendor accounts and ensure compliance with industry standards.




