Last Updated on 17 Aug 2025
Travel Fraud Prevention Hierarchy: A Complete Guide For OTAs, Airlines, and Hospitality
Share in
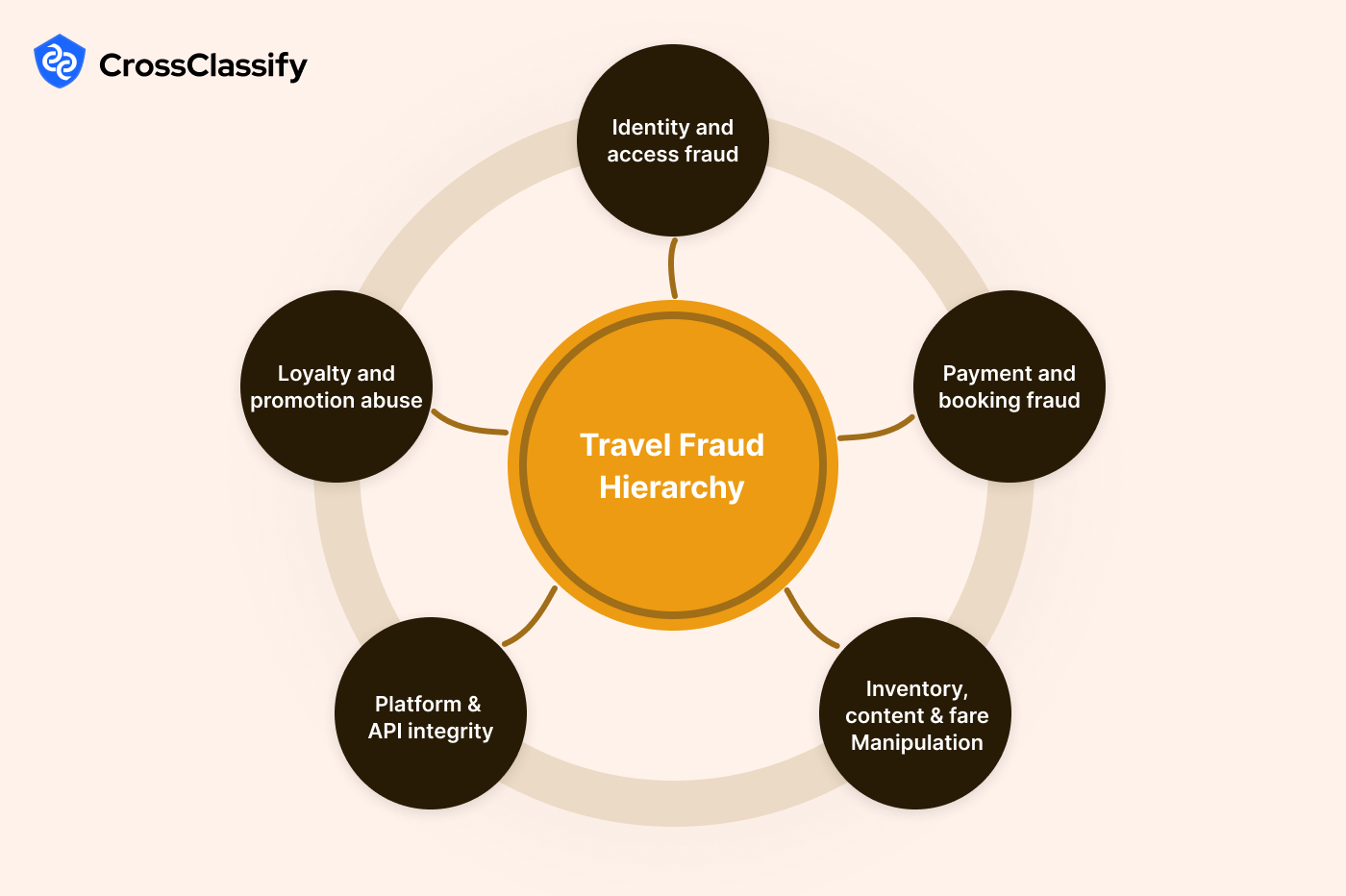
Why travel apps need continuous fraud defense now
Digital bookings and loyalty programs turned travel into a target rich environment for cybercrime and abuse, with fraud losses in recent years cited around 21 billion dollars worldwide. Travel fraud prevention software for OTAs, airline account takeover protection, and loyalty fraud detection for travel apps have shifted from nice-to-have to foundational risk controls. Attackers love the high value of tickets and points, the resale market for vouchers, and the speed of modern checkout flows.CrossClassify focuses on continuous, AI-driven monitoring of identity, devices, and post-login behavior to stop threats before tickets are issued or miles are drained. The case for proactive defense is also regulatory and reputational: travel breaches and scraping disputes routinely make headlines, which slows growth and pushes up acquisition costs. crossclassify.com
Identity and Access Fraud in Travel Applications
Identity threats in travel come from credential stuffing, phishing, social engineering of support desks, and household account sharing that crosses into abuse. The business impact shows up as stolen miles, unauthorized bookings, and customer churn after lockouts. A modern stack uses layered defenses: device intelligence, behavioral biometrics, and adaptive challenges only when risk is high.Continuous monitoring matters because attackers often pass static controls then pivot to change emails and phone numbers before making high-value moves. Real incidents like airline data breaches and loyalty drain stories show how fast attackers monetize access once they are in. Learn more
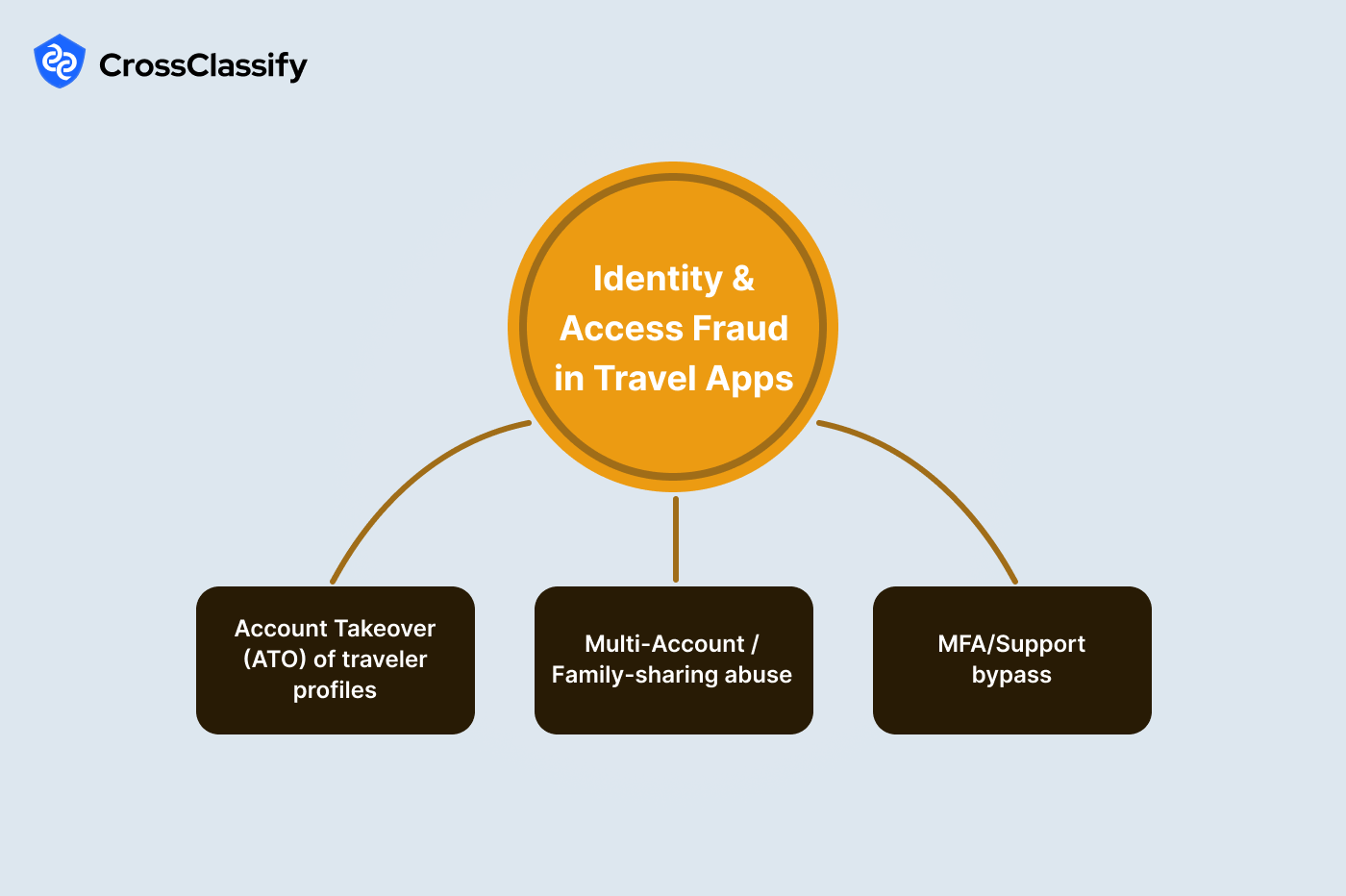

Sub-type: Account Takeover in travel (ATO)
- Signal: New login from unfamiliar country or device immediately before points or card redemption
Evidence: Heatmap of logins by country × hour
Explanation: The pattern is a fresh geo or device that appears just before redemption or ticketing. The heatmap should cluster around expected home markets and local hours for legitimate travelers. A sudden hotspot at unusual hours or regions that do not match the customer's history is an ATO red flag. - Signal: Spike in failed logins followed by a successful login
Evidence: Line graph showing failed versus successful logins over time
Explanation: Credential stuffing campaigns drive failures first, then a narrow band of successes once combinations hit. A stable baseline of failures suggests low attack pressure. Co-movement where failures surge then successes rebound in the same window indicates takeover events that need immediate containment.
Real-world note: The British Airways breach led to regulatory action and significant fines, underlining the stakes of identity and web-app exposure for airlines. Wikipedia
Sub-type: Multi-account or family-sharing abuse
- Signal: Many accounts on the same device or IP making overlapping bookings
Evidence: Bipartite network of devices or IPs to accounts
Explanation: In normal households you see tight clusters with one or two accounts per device. Abuse rings create hub nodes that connect to many accounts placing similar itineraries or overlapping stays. The graph should be sparse in good traffic and very hubby in abuse. - Signal: Reused device fingerprint across unrelated surnames
Evidence: Table listing device_id, linked accounts, and surnames
Explanation: Travel households often share surnames and addresses. When the same fingerprint powers numerous unrelated surnames, the risk shifts from genuine family usage to identity sharing, farms, or organized refund exploits.
Sub-type: MFA and support bypass
- Signal: Email or phone change followed by password reset within 10 minutes
Evidence: Line chart with contact changes and resets in 15-minute bins
Explanation: Social engineering often convinces users or agents to change recovery channels, then the attacker rushes a reset. Healthy apps show weak coupling between profile edits and resets. Tight clustering suggests a bypass pattern. - Signal: Support interaction directly precedes credential change
Evidence: Table with ticket channel, change event, and minutes before change
Explanation: Investigate cases where chat or phone tickets are closely followed by password, MFA, or payout changes. Normal service flows show wide gaps. Narrow gaps point to support-assisted takeovers that require agent playbooks and step-up verification.
Payment and Booking Fraud
Payment flows in travel are perfect for testing cards and laundering value through refundable bookings. Fraudsters exploit weak AVS or CVV handling, geographic misalignments, and generous refund terms. The best defenses track route and airport context, monitor BIN behavior over time, and link search-to-book ratios by IP range. The aim is to stop risky bookings before settlement and to reduce friendly chargebacks through evidence and policy.High seasonality in travel also creates cover for abnormal activity that looks like rush hour noise unless you model the baseline correctly.
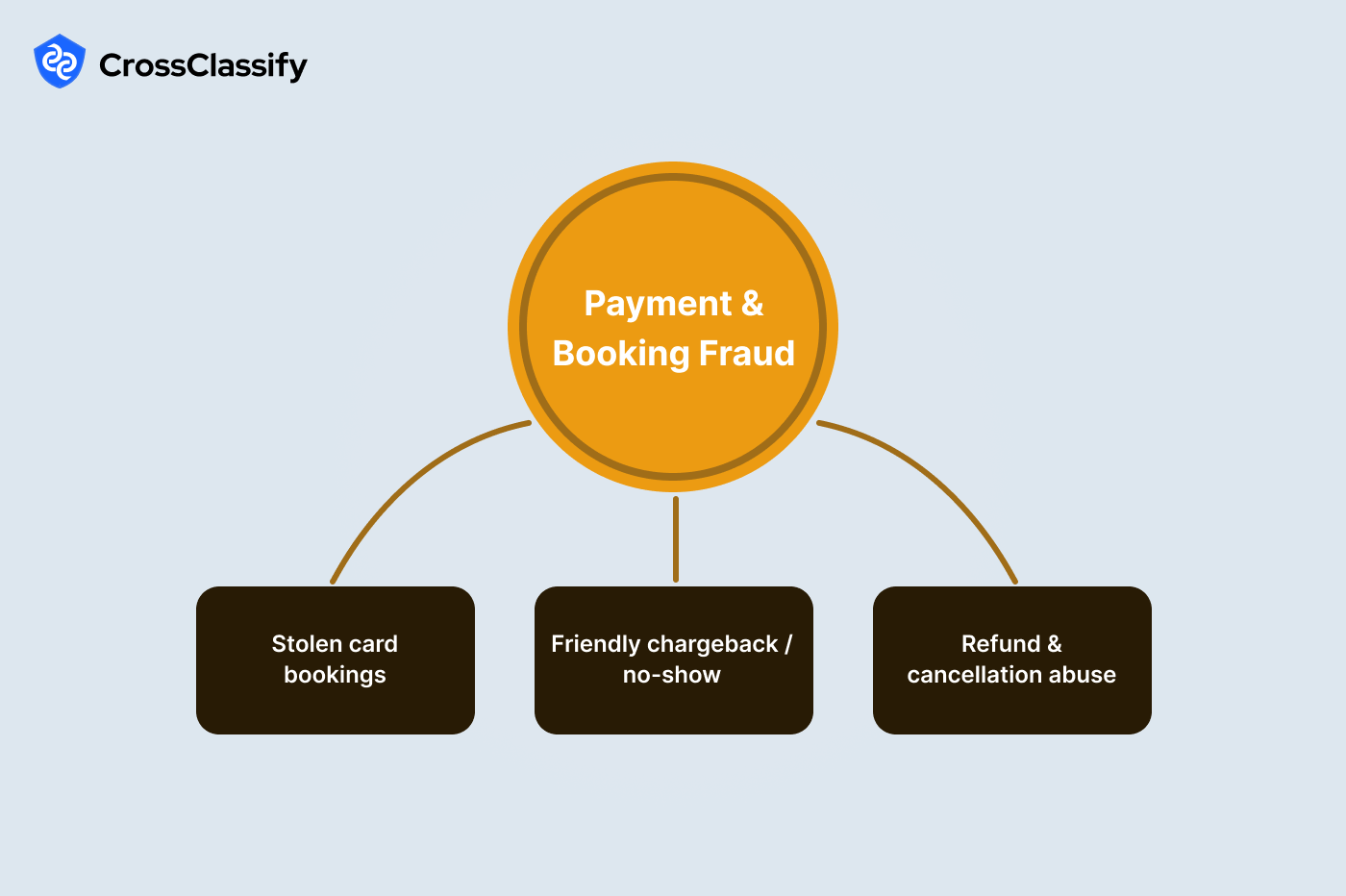

Sub-type: Stolen card bookings
- Signal: IP country mismatches departure airport country
Evidence: Crosstab table of IP country by departure country
Explanation: Most legitimate bookings align roughly with traveler origin and departure. Off-diagonals are expected for business or remote purchases, although they should be rare. High off-diagonal concentrations, especially on certain routes, are a sign of carding. - Signal: AVS or CVV mismatch rate spikes on a specific BIN
Evidence: Line chart of mismatch rate by BIN over time
Explanation: When testing campaigns target one issuing bank, you see a sharp, isolated increase in AVS or CVV fails for that BIN. Stable, bounded lines across BINs suggest healthy traffic, while one outlier indicates targeted testing.
Real-world note: EasyJet disclosed a large breach affecting about nine million customers, which demonstrates how valuable travel data and payment flows are for attackers who later reuse credentials and cards. Wikipedia
Sub-type: Friendly chargeback
- Signal: Short-stay, high-value prepaid bookings with no check-in
Evidence: Heatmap of chargeback rate by stay length and price band
Explanation: Abuse clusters on one-night stays at premium prices and on dates with quick refund windows. A balanced heatmap is normal. Hot cells around short stays and high price bands indicate a friendly dispute pattern. - Signal: Multiple disputes from the same traveler across merchants
Evidence: Bar chart of disputes per traveler, with top offenders
Explanation: Serial disputers are rare in healthy cohorts. Tall outliers with repeated disputes across brands or properties are classic revenue leakage you can curb with velocity rules and shared intelligence.
Sub-type: Refund and cancellation abuse
- Signal: Repeated cancellations near a free-cancel deadline
Evidence: Line chart of cancellations versus minutes before deadline
Explanation: A flat curve means customers cancel at mixed times for genuine reasons. A spiky curve near the deadline shows deadline gaming, often coordinated with promo stacking. - Signal: Refunds to multiple cards from the same device
Evidence: Table of device to unique refunded cards
Explanation: One device mapping to many payout instruments is rare and risky. Normal devices show one-to-one or one-to-few card mappings.
Loyalty and Promotion Abuse
Loyalty points act like a parallel currency. Attackers drain balances, flip gift cards, and farm vouchers with synthetic accounts. Since program rules often favor low friction, you need silent controls that watch sequences and device behavior rather than friction at every click. The best signals look at order of events, such as login then profile change then transfer, and at bursty redemption patterns from atypical regions.
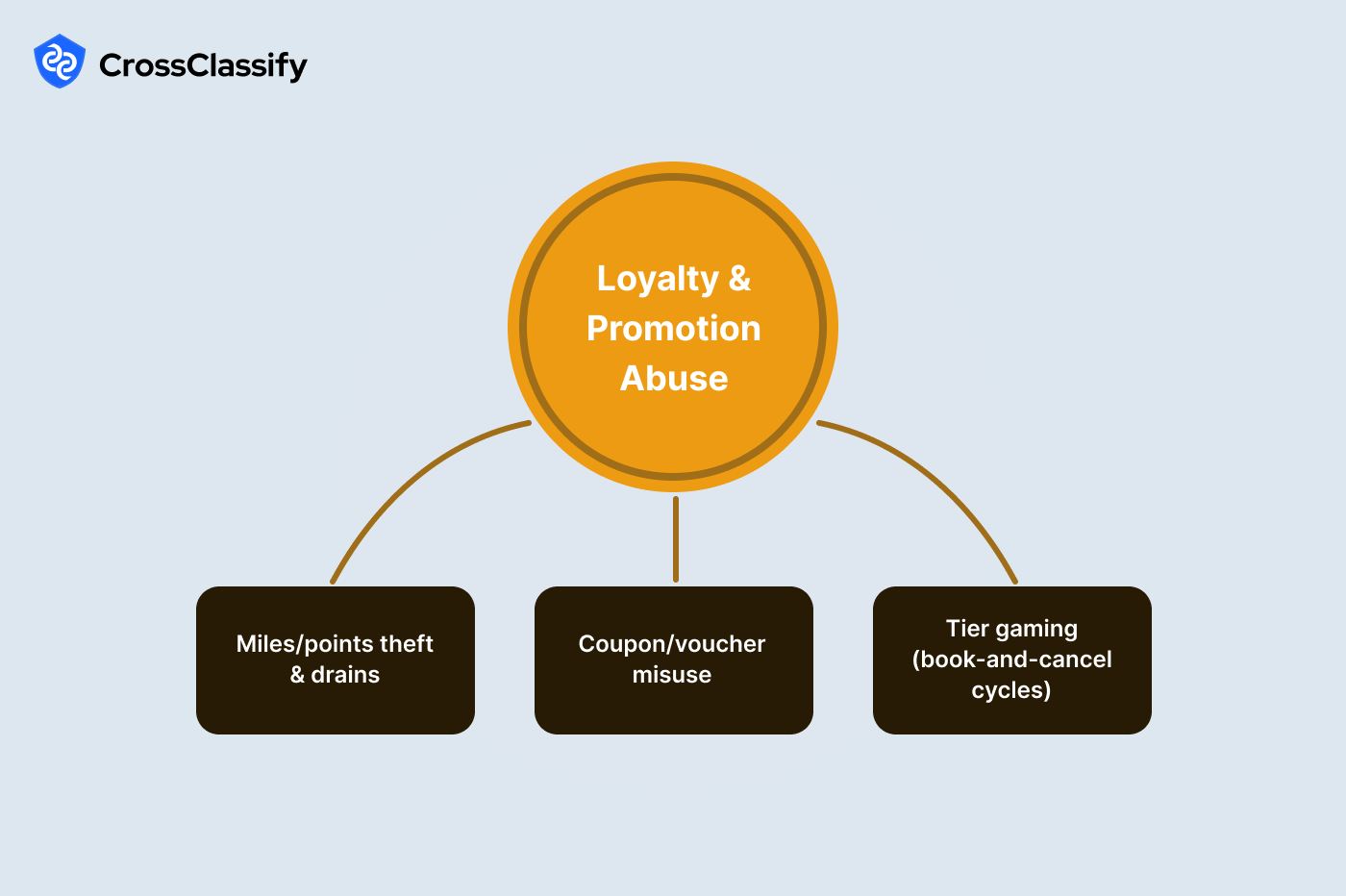

Sub-type: Miles and points theft or drains
- Signal: Login followed by contact change then same-day points transfer
Evidence: Line chart of logins, contact changes, and transfers per hour
Explanation: This sequence is highly predictive. In safe apps the three lines do not align. When peaks appear in order within the same day, freeze and verify. - Signal: Redemptions from atypical regions or destinations
Evidence: Heatmap of redemptions by region and award type
Explanation: Programs have stable regional patterns. A sudden hotspot for gift cards in regions without prior activity is a theft tell.
Real-world note: Marriott and Starwood saw multi-year breaches that exposed sensitive guest data, which turned into regulatory actions and settlements, a reminder that loyalty and guest identity are high value targets. AP News
Sub-type: Coupon or voucher misuse
- Signal: Multiple voucher redemptions from the same device within one hour
Evidence: Line chart of redemptions per device in 10-minute bins
Explanation: Real travelers redeem infrequently. Short bursts from a single device suggest voucher farming, often with emulators. - Signal: Voucher used without qualifying spend
Evidence: Table of voucher_id, basket_total, min_spend, qualified
Explanation: Most uses should meet the threshold. When many rows fail qualification, adjust enforcement and block device clusters.
Sub-type: Tier gaming
- Signal: Book-then-cancel cycles to accrue status segments
Evidence: Line chart of segments versus cancellations per week
Explanation: When cancellations rise in lockstep with segment accrual periods, members are gaming thresholds. Real travel segments do not co-spike with cancels. - Signal: Many bookings canceled within 24 hours of booking
Evidence: Bar chart of cancellation time buckets
Explanation: Healthy programs skew to longer windows. Heavy bars in the under-24-hour bucket show quick-cancel tactics tied to status chasing.
Inventory, Content, and Fare Integrity
Content quality and fare accuracy drive conversion and trust. Scrapers degrade pricing strategies and affiliate economics. Fake listings and reviews poison the marketplace. Fare parameter tampering creates chargebacks and regulatory risk. Controls here blend bot management, link analysis, and price integrity checks between quote and charge.

Sub-type: Scraping of inventory and fares
- Signal: Excessive search requests with uncommon user agents
Evidence: Bar chart of requests per user-agent group
Explanation: Real traffic is dominated by modern browsers on desktop and mobile. Bars labeled as automation frameworks or headless drivers should be low. When these bars rise, add device integrity checks and throttle. - Signal: High search to booking ratio from specific IP ranges
Evidence: Table of IP range, searches, bookings, and ratio
Explanation: Scrapers poll heavily without converting. IP ranges with extreme ratios need rate limits and block-lists, plus behavioral checks to confirm non-human patterns.
Real-world note: Ryanair's long running legal fight against unauthorized scraping produced a United States court ruling that Booking.com's access violated the Computer Fraud and Abuse Act, underscoring the economic damage scraping can cause to airlines. Reuters
Sub-type: Fake listings and reviews
- Signal: Review bursts from new accounts within the same day
Evidence: Line chart of reviews per day by account cohort
Explanation: Genuine reviews arrive gradually. Cohorts of new accounts that surge together suggest coordination. - Signal: IP clusters posting across multiple properties
Evidence: Bipartite network of IPs to properties
Explanation: In healthy ecosystems, IPs connect to a few properties at most. Hubs that push reviews across many properties point to manipulation.
Sub-type: Deep link and parameter tampering
- Signal: Mismatch between quoted fare and charged fare
Evidence: Table of booking_id, quoted, charged, and delta
Explanation: Deltas near zero are expected. Non-zero deltas indicate fare injection or rounding exploits at checkout. - Signal: Unsupported fare class codes in requests
Evidence: Bar chart of invalid fare code counts
Explanation: Invalid codes should be rare and static. Elevated and varied bars reveal probing or fuzzing and merit tighter validation.
Bots in Conversion Funnels
Fraudsters deploy automation to poll prices, occupy seats or rooms, and distort marketing traffic. Because these actions often do not transact, they hide behind ”harmless” browsing metrics. Identifying machines that emulate sessions without genuine depth is key, as is protecting hold flows and affiliate budgets.

Sub-type: High-velocity search and price polling
- Signal: Request rates above threshold to the search endpoint per device
Evidence: Line chart of requests per minute per device
Explanation: Human users have smooth curves. Sharp spikes beyond reasonable limits expose bots harvesting fares for resale or metasearch arbitrage. - Signal: No session depth or zero detail page views
Evidence: Bar chart of sessions by depth
Explanation: Healthy sessions read details, add to carts, and revisit itineraries. A dominant zero-page bar indicates bot browsing that never engages product.
Sub-type: Seat or room hold bots
- Signal: Many holds without purchase across routes or dates
Evidence: Heatmap of holds by route and date
Explanation: Normal holds distribute across routes. Hot clusters with low conversion signal inventory denial or scalping attempts. - Signal: Same device creates holds across many accounts
Evidence: Table of device, accounts, and total holds
Explanation: Corporate travel desks may centrally manage, although that pattern is limited and known. Unknown devices spanning many unrelated accounts are suspect.
Sub-type: Affiliate and metasearch click fraud
- Signal: Very high clicks with near zero bookings per source
Evidence: Bar chart of conversion rate by source
Explanation: Sources should cluster around a stable conversion band. Extreme lows point to manufactured clicks, misattributed traffic, or misconfigured tagging. - Signal: Abnormal referrers or domains generating bounce traffic
Evidence: Table of referrer, visits, bounces, and bounce rate
Explanation: A balanced table shows healthy bounce rates across partners. Outliers with extreme bounce rates merit investigation and potential auto-exclusion.
How CrossClassify operationalizes this hierarchy for travel
CrossClassify connects signals from identity, payment, loyalty, content, and funnel automation into one real time risk picture. Behavioral biometrics model genuine traveler patterns across keystrokes, gestures, and navigation to catch bots and imposters silently. Device fingerprinting links accounts, payouts, and holds back to persistent device profiles even when cookies disappear, which breaks multi-account abuse rings.
Adaptive risk scoring introduces step-up challenges only when needed, preserving conversion while protecting margins. The hierarchy above becomes prescriptive product telemetry: heatmaps, networks, and tables every analyst can use in daily investigations and rule tuning. Explore the travel solution overview here.
Real-world reminders
•
British Airways regulatory fine highlights the cost of poor web and identity security in airline contexts. Gdprregister•
EasyJet's disclosure shows how travel data becomes a springboard for later ATO and card abuse. Wikipedia•
Marriott and Starwood actions show regulators expect durable data protection around guests and loyalty assets. AP News•
Ryanair's anti-scraping victory underscores that scraping is not harmless traffic and has real business impact. Reuters
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Successful teams layer behavior and device signals after login so only risky sessions get challenged. CrossClassify scores every session in real time and introduces smart MFA only when needed, which protects bookings and points with minimal friction. Read more
Look for device fingerprints bridging unrelated surnames and overlapping bookings. CrossClassify's device intelligence and link analysis surface hub devices instantly and can auto-restrict risky holds or redemptions. Learn how device intelligence works
Sequence-aware analytics that watch login, profile edits, and transfers catch attackers before the drain completes. CrossClassify's behavior timeline flags the risky sequence and can freeze the transfer for manual review. Travel deep dive
Measure requests per user agent, search-to-book ratios by IP range, and session depth. CrossClassify classifies automation with behavior models and device signals, letting you throttle bad actors and keep quality traffic. See why WAF and MFA are not enough alone
Target the risk quadrant of short stay and high price with pre-authorization checks and post-stay validation. CrossClassify's risk scoring prior to issuance lowers exposure, while evidence dashboards strengthen representment. Program guidance
Watch per-device redemption bursts and validate qualifying spend. CrossClassify correlates device fingerprints with voucher usage and blocks serial abusers automatically. Device insights
They stop many infrastructure attacks but miss human-like fraud after authentication. CrossClassify adds continuous user behavior analytics and device intelligence to catch ATO, bots, and synthetic users. Why this matters
Adopt continuous, adaptive trust with real time monitoring of session behavior, device trust, and context. CrossClassify supports CARTA style controls that adapt during the session to block misuse. Framework overview
Compare conversions by source and bounce outliers by referrer , then apply behavior and device validation before crediting clicks. CrossClassify enriches attribution with risk signals so budgets flow to real buyers. Threats and behavior analytics
Map holds by route and date for hotspots and look for devices creating holds across many accounts. CrossClassify detects non-human navigation and device emulation and can require step-up or block holds in real time. Travel article for context
It profiles genuine traveler behavior and flags anomalies that even valid credentials cannot hide. CrossClassify uses keystroke dynamics, touch patterns, and navigation flow to stop imposters silently. Learn more
Zero trust reduces implicit trust and requires continuous verification of users and devices. CrossClassify operationalizes this with device fingerprinting and behavior analytics that feed adaptive access decisions. Reference architecture
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
