Verify real customers with behavioral biometrics and device intelligence
Detect bots, mules, and stolen credentials without adding friction.

Solution
Why Behavioral Biometrics Security Matters For Continuous Authentication
Continuous authentication and fraud detection without compromising user experience.
Stop Emulator Spoofing
Fraud teams face bots that mimic human motion and replay keystroke cadence at scale. CrossClassify pairs behavioral biometrics authentication with device fingerprinting and behavioral biometrics fraud detection to expose scripted sessions before they touch money movement.
Enforce Continuous Authentication
Login checks alone miss takeovers during payouts, limit changes, and profile edits. We deliver continuous authentication using behavioral biometrics with risk based authentication so trusted users stay fast while risky flows receive just in time step up.
Reduce Friction And Noise
Passive checks can create false positives that anger customers and drain analysts. Our passive behavioral biometrics with AI driven anomaly detection filters natural variability from genuine users and isolates automation without added prompts.
Protect Models And APIs
Attackers probe endpoints to learn features and degrade performance over time. CrossClassify shields behavioral biometrics technology with secure API gateways, Zero Trust Architecture, and rate limits that block feature scraping and model extraction.
Harden Banking Compliance
Financial services must balance accuracy with PSD2 and regulator expectations. We operationalize behavioral biometrics in banking for Strong Customer Authentication and auditable behavioral biometrics digital identity controls that compliance teams can defend.
Bind Identity Across Devices
VPNs, virtual machines, and shared hardware break signal continuity across channels. CrossClassify fuses device fingerprinting with behavioral biometrics patterns to maintain a single behavioral biometric authentication view of the user across web and mobile.
Preserve Data Trustworthiness
Model drift and poisoned training data erode detection quality and credibility. We enforce encryption and least privilege while quarantining outliers so behavioral biometrics solutions learn from clean signals and remain reliable for long term operations.
Our Approach to behavioral biometrics
We use the latest industry-level technologies to monitor and detect behavioral patterns for continuous authentication and fraud prevention.
Continuous Monitoring
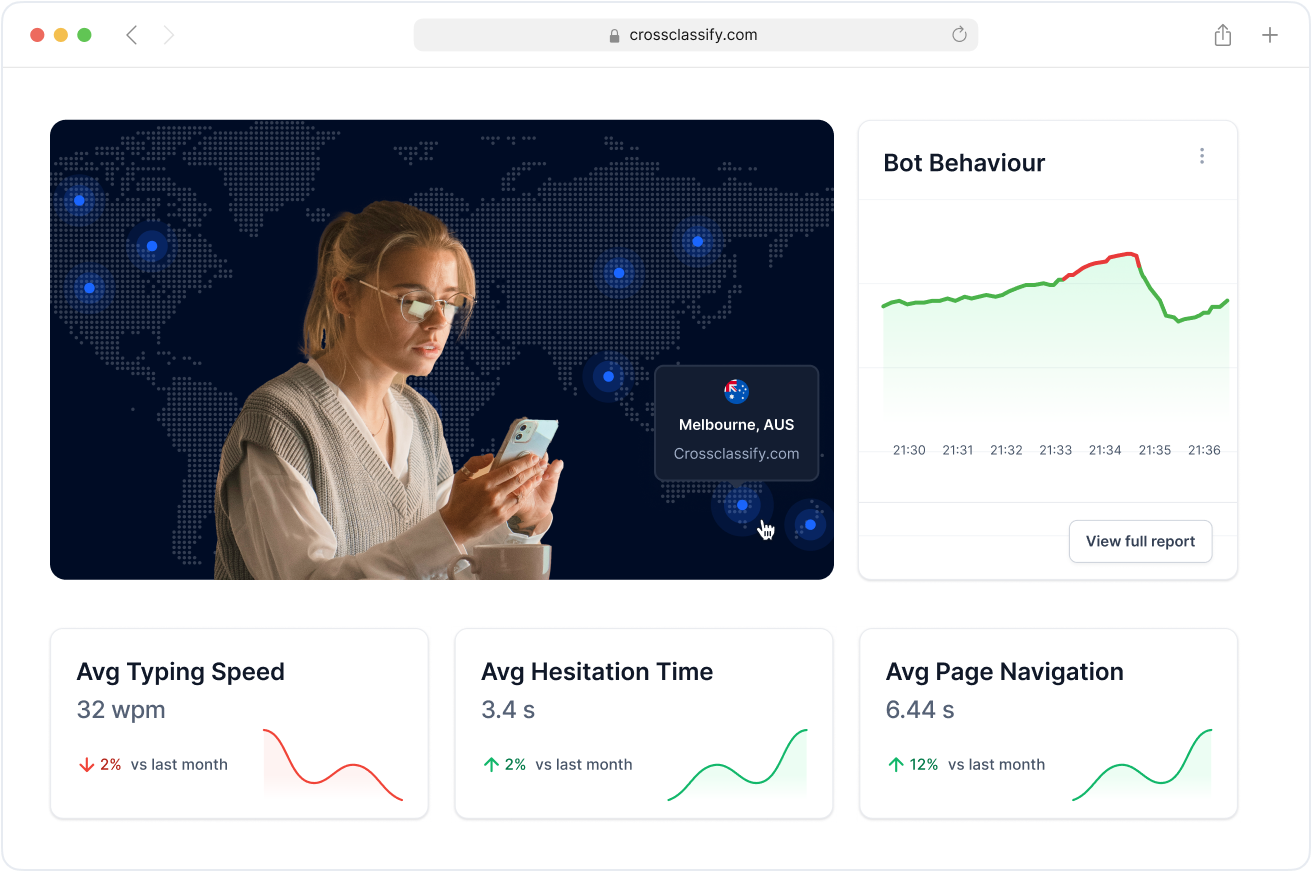
Our engine runs continuous behavioral biometrics authentication across every step, not just login, combining keystroke dynamics, pointer trajectory, touch pressure, scroll rhythm, accelerometer tilt, and session context with device fingerprinting for online fraud prevention. Risk based authentication adapts in real time to limit changes, payouts, KYC edits, and live transactions, so trusted users remain fast while high risk flows get step up. Passive behavioral biometrics keeps friction low and detects automation patterns that static checks miss.
Behavior Analysis
We learn behavioral biometrics patterns like dwell time, field to field timing, swipe speed, micro pauses, and navigation rhythm to separate genuine users from bots and impostors. Our behavioral biometrics solutions use AI and ML to model user intent and spot anomalies such as replayed cadence, emulator jitter, and scripted mouse arcs. The result is continuous authentication using behavioral biometrics that preserves UX and blocks account takeover before money moves.
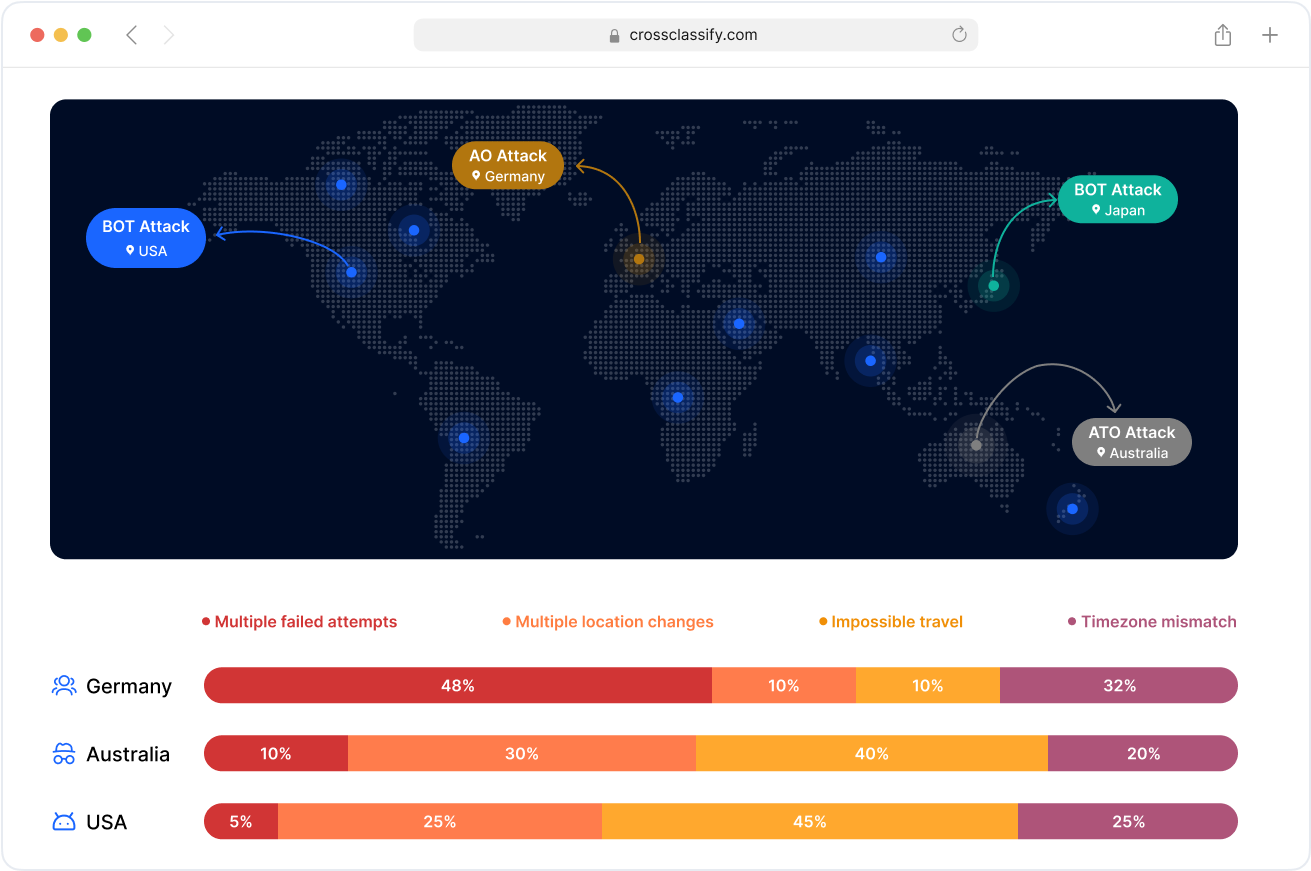
Geo Analysis
CrossClassify fuses geo velocity checks with behavioral signals to expose impossible travel, VPN and hosting ASN misuse, and region hopping that aligns with risky edits or withdrawals. Device fingerprinting plus behavioral biometric authentication binds identity across devices and networks, even in private browsing. You get precise geo risk scoring for banking behavioral biometrics and ecommerce flows without brittle rules.
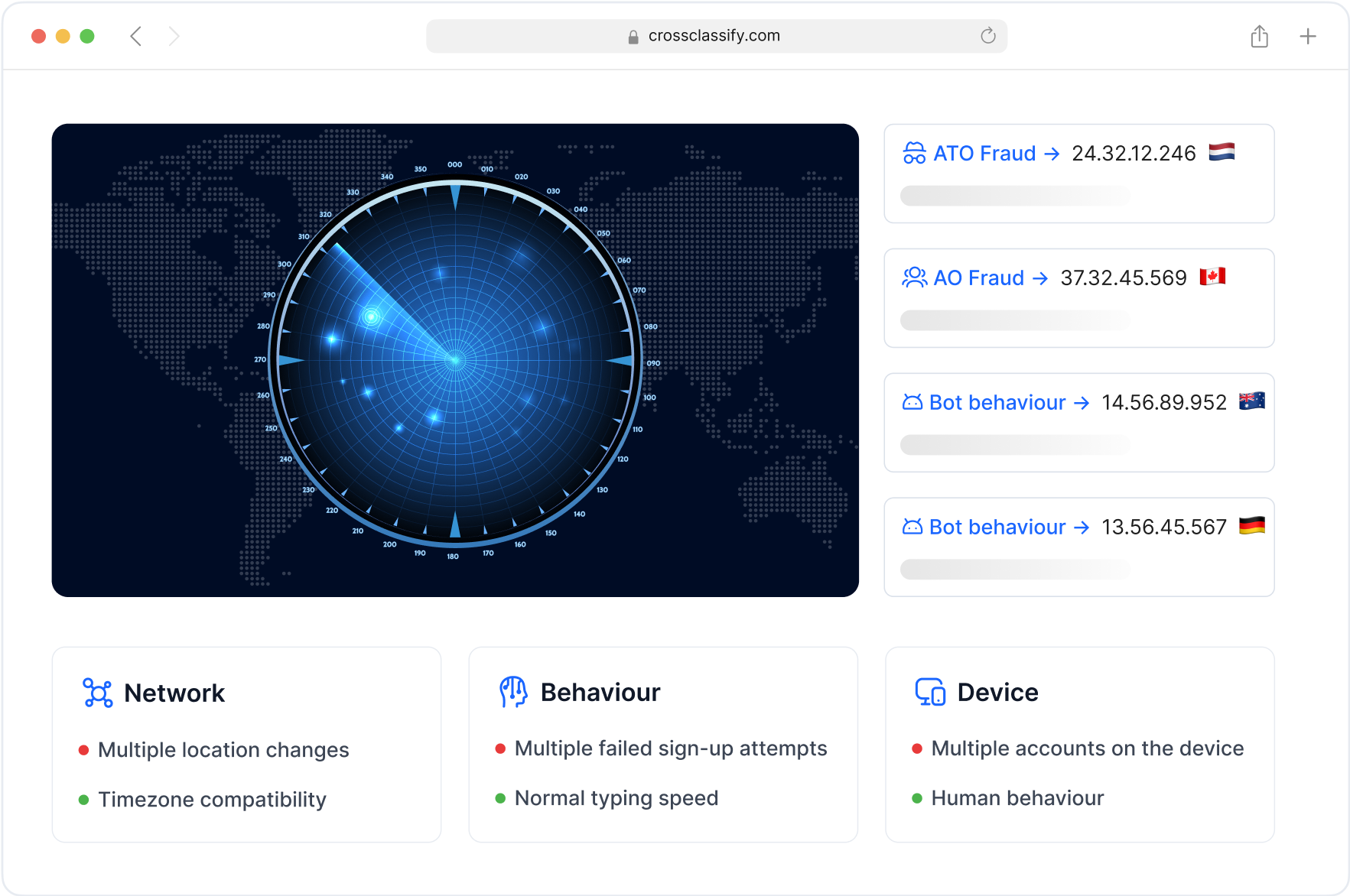
Link Analysis
Our graph analytics connects devices, accounts, payment instruments, and beneficiaries to reveal multi account rings that share the same behavioral biometrics examples like identical field timing or identical swipe rhythm. We correlate passive behavioral biometrics with device fingerprint clusters to surface collusion hubs and synthetic identity umbrellas. This link analysis powers targeted controls for behavioral biometrics fraud detection at scale.
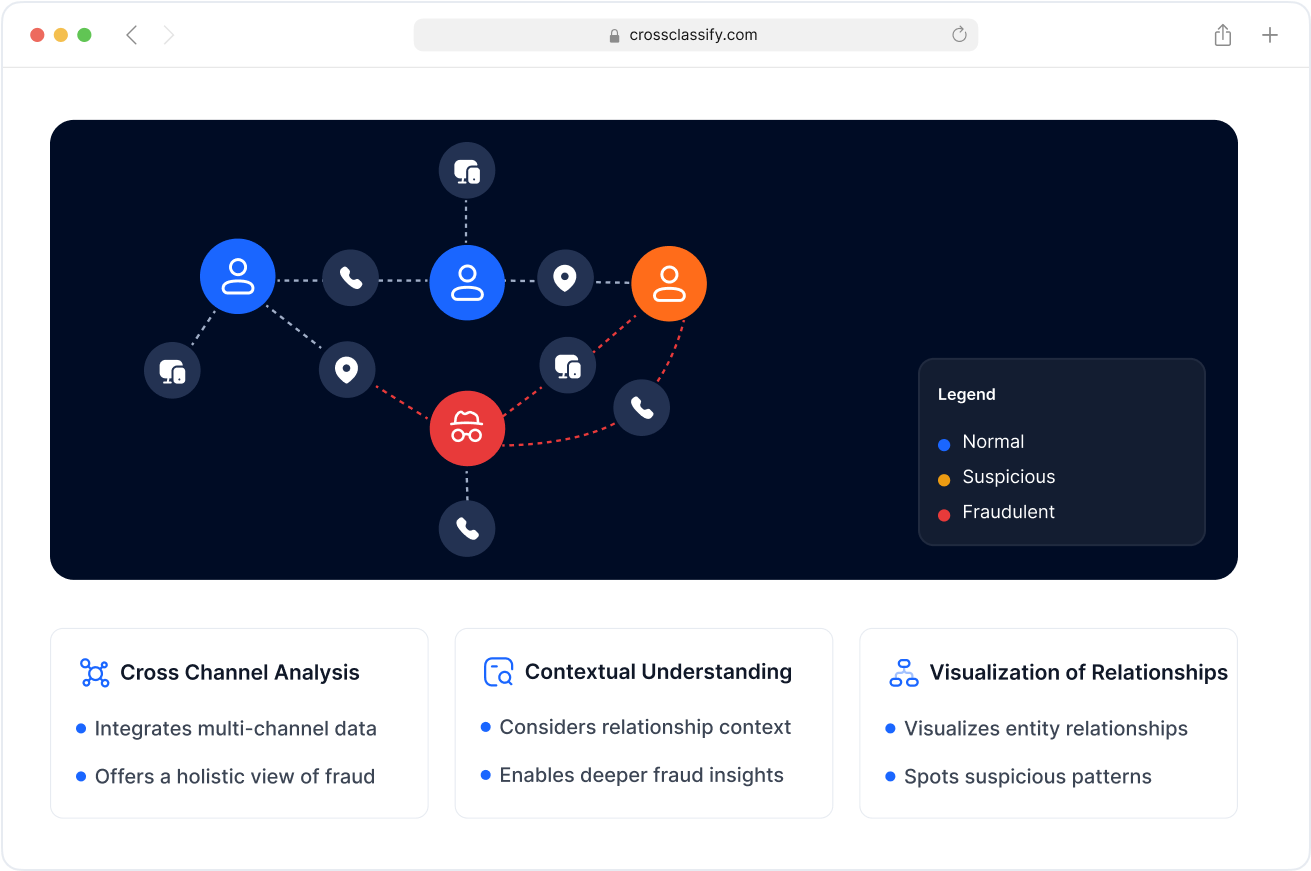
Enhanced Security and Accuracy
By combining behavioral biometrics technology with device fingerprinting, IP reputation, and velocity checks, we reduce false positives and cut manual review while improving catch rates. Risk based authentication decisions are transparent and auditable for regulators in banking and payments, with continuous authentication that adapts to model drift. The stack is built for behavioral biometrics fraud prevention where accuracy and low friction both matter.
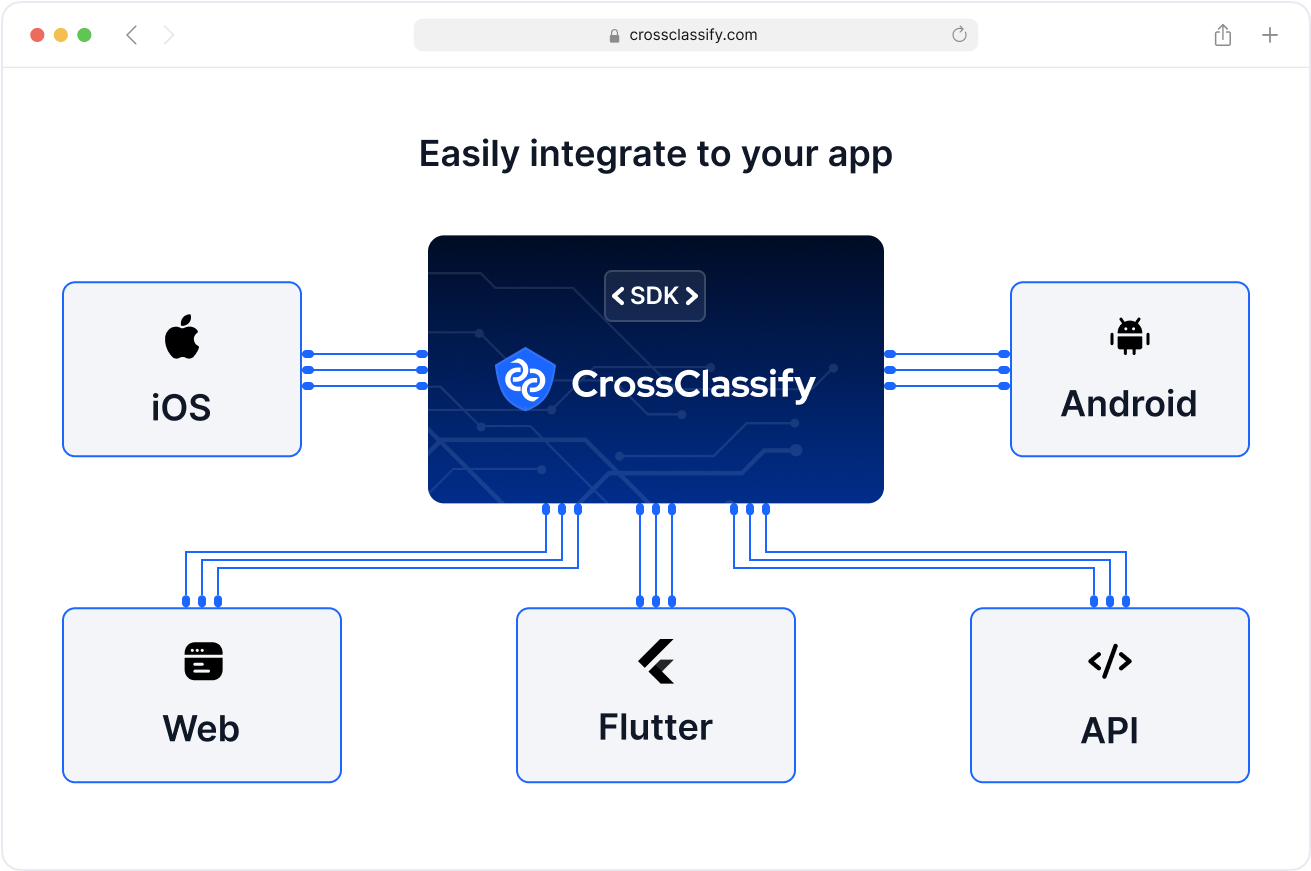
Seamless Integration
Deploy behavioral biometrics authentication with lightweight SDKs and high performance APIs that stream signals server side and client side. CrossClassify fits existing SSO, MFA, and CIAM workflows, and supports privacy by design with regional data residency for regulated industries. Start with targeted endpoints like login, payout, and profile edit, then expand to full behavioral biometrics use cases.
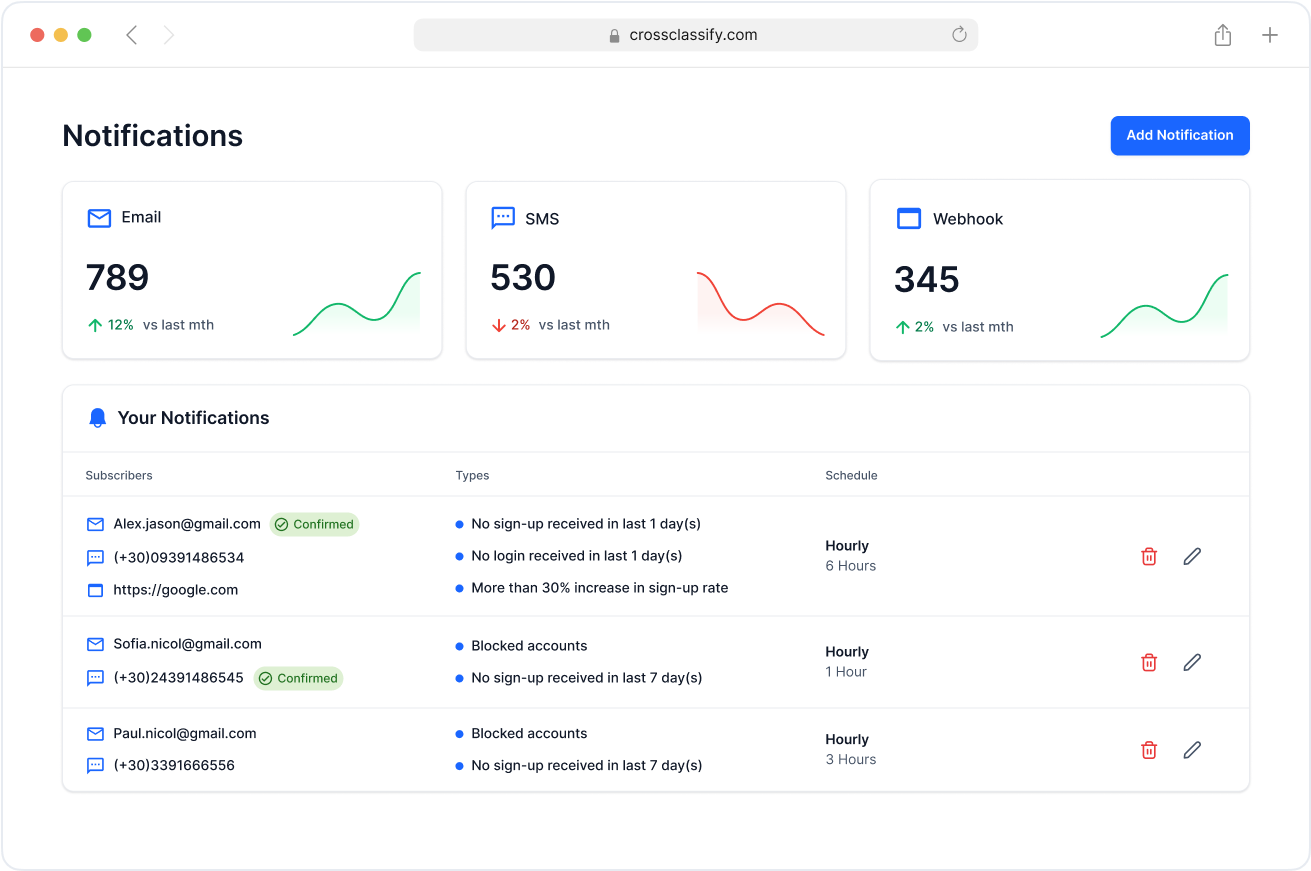
Alerting and Notification
Trigger real time alerting on behavioral risk thresholds for events such as fail to success login flips, device binding breaks, payout edits, and high velocity bot traffic. Route notifications to SIEM, Slack, email, or webhooks with enriched context from behavioral biometrics patterns and device intelligence, so fraud and SOC teams act quickly with evidence. Playbooks support auto hold, session lock, or step up MFA when risk crosses policy.
Blog
Latest from Cross Classify
Frequently asked questions
Learn more
Deep dive
Overview
See
Read
Learn how device intelligence adds lift
Governance guidance
See risk tuning practices
Device intelligence primer
Explore related attacks
More on new account risks
See adaptive modeling
Implementation considerations
Read more
Related guidance
Program governance
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required