Last Updated on 08 Sept 2025
Fraud Prevention and Cybersecurity in the Recruitment Industry
Share in

Introduction
The recruitment industry is undergoing digital transformation at unprecedented speed. Online job boards, mobile-first recruitment platforms, and AI-driven candidate matching have expanded opportunities for employers and job seekers. However, these innovations also open the door for new recruitment fraud schemes, cybersecurity risks, and fake employer and candidate profiles that put platforms, recruiters, and applicants at risk. According to industry reports, fraudulent job postings and account takeover fraud in recruitment platforms cost businesses and individuals billions annually. The stakes are high: one fake recruiter profile can lead to stolen candidate data, financial scams, and reputational loss for the entire platform.
CrossClassify helps recruitment businesses combat these risks with a combination of device fingerprinting, behavioral biometrics, account takeover protection, and continuous risk scoring. By creating a detailed hierarchy of the most dangerous fraud and cybersecurity concerns in the recruitment sector, businesses can identify red flags early and protect both employers and job seekers.
CrossClassify helps recruitment businesses combat these risks with a combination of device fingerprinting, behavioral biometrics, account takeover protection, and continuous risk scoring. By creating a detailed hierarchy of the most dangerous fraud and cybersecurity concerns in the recruitment sector, businesses can identify red flags early and protect both employers and job seekers.
Identity and Access Abuse in Recruitment Platforms
Identity and access fraud in recruitment refers to malicious actors hijacking recruiter or candidate accounts to gain unauthorized access. Once in control, fraudsters can manipulate job listings, harvest resumes, or scam job seekers. Real-world cases include the LinkedIn account takeover scams where fake recruiters posed as legitimate HR managers to trick candidates into paying "application fees."
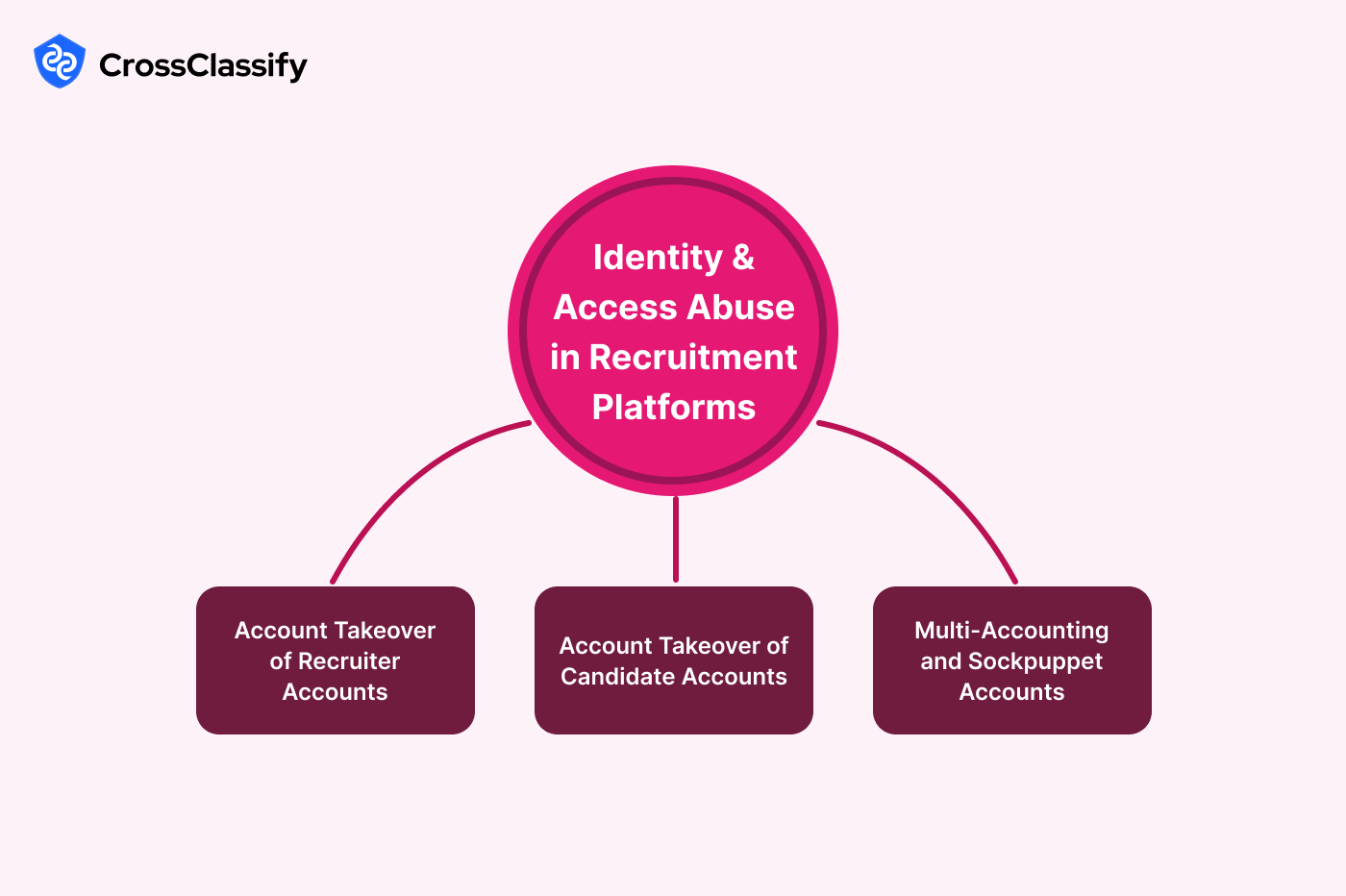

1. Account Takeover of Recruiter Accounts
Fraudsters compromise legitimate recruiter accounts to post fake job listings or access candidate databases.
Signals and Evidence:
- New login from unseen device fingerprint: If a recruiter account suddenly shows login attempts from an unrecognized device, it indicates possible compromise. Evidence appears in device fingerprinting dashboards highlighting device novelty.
- Multiple failed logins followed by a successful login from distant geolocation: Attackers often use brute force or credential stuffing before finally gaining access. Evidence is captured in geo-based login reports.
2. Account Takeover of Candidate Accounts
Fraudsters hijack candidate accounts to spam employers or redirect communication to scam channels.
Signals and Evidence:
- Sudden changes to profile information followed by mass job applications: A compromised candidate account often changes email or phone details before spamming applications. Evidence shows up in application activity graphs.
- Login attempts from anonymizing networks (VPN, TOR): Malicious actors hide behind anonymizers. Evidence is visualized in network-type login charts.
3. Multi-Accounting and Sockpuppet Accounts
Some fraudsters create multiple candidate or recruiter accounts to manipulate rankings, bypass limits, or perpetrate scams.
Signals and Evidence:
- Shared device fingerprints across multiple accounts: When several accounts originate from the same device, it indicates multi-accounting. Evidence emerges in network visualizations linking accounts to devices.
- Reused payout methods across recruiter entities: Fraudsters funnel money to the same bank account through multiple fake recruiter accounts. Evidence is captured in financial mapping dashboards.
Fake Candidate and Employer Account Opening Fraud
Fake accounts in recruitment platforms are one of the fastest-growing fraud vectors. Fraudsters use synthetic identities, disposable emails, and fabricated resumes to infiltrate systems. In 2023, Indeed and LinkedIn reported large waves of fake employer accounts that tricked candidates into sharing personal and banking information.
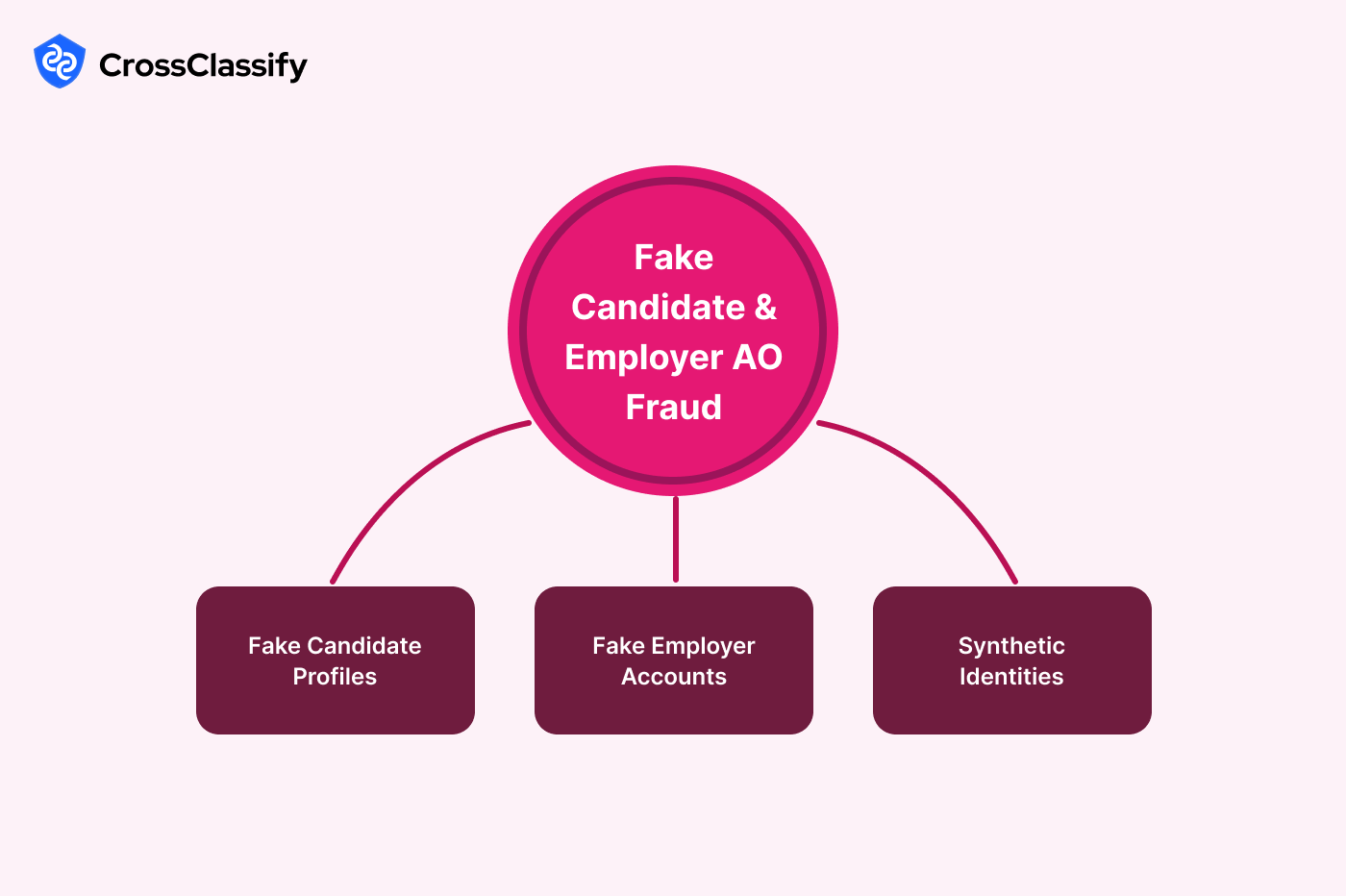

1. Fake Candidate Profiles
Fraudsters use stolen or fabricated CVs to create fake candidates.
Signals and Evidence:
- Mass sign-ups from a few IP addresses: Automated fake candidate creation often stems from the same subnet. Evidence shows up in sign-up distribution graphs.
- Inconsistent work history compared to external data: Gaps in timelines or inflated titles highlight fraudulent patterns. Evidence is displayed in resume integrity tables.
2. Fake Employer Accounts
Scammers create fake recruiter profiles to harvest candidate information.
Signals and Evidence:
- Non-deliverable corporate email domains: Many fake employers use disposable or unverifiable email domains. Evidence appears in domain verification failure dashboards.
- Reused company registration numbers across multiple accounts: Duplicate registration IDs point to fraudulent employer entities. Evidence is presented in duplicate registration tables.
3. Synthetic Identities in Recruitment
Fraudsters combine stolen details with fabricated data to bypass traditional checks.
Signals and Evidence:
- High ratio of disposable emails and virtual phone numbers: A surge of temporary contact methods is a red flag. Evidence appears in contact metadata tables.
- Device cookie churn with nearly identical hardware prints: Bots reset cookies to mimic new users. Evidence is captured in device hash stability graphs.
Automated Bots and Resume Scraping Attacks
The recruitment industry faces increasing bot attacks targeting application forms, resume scraping, and credential stuffing. In 2022, CareerBuilder reported scraping attacks that harvested millions of resumes to resell on black markets.
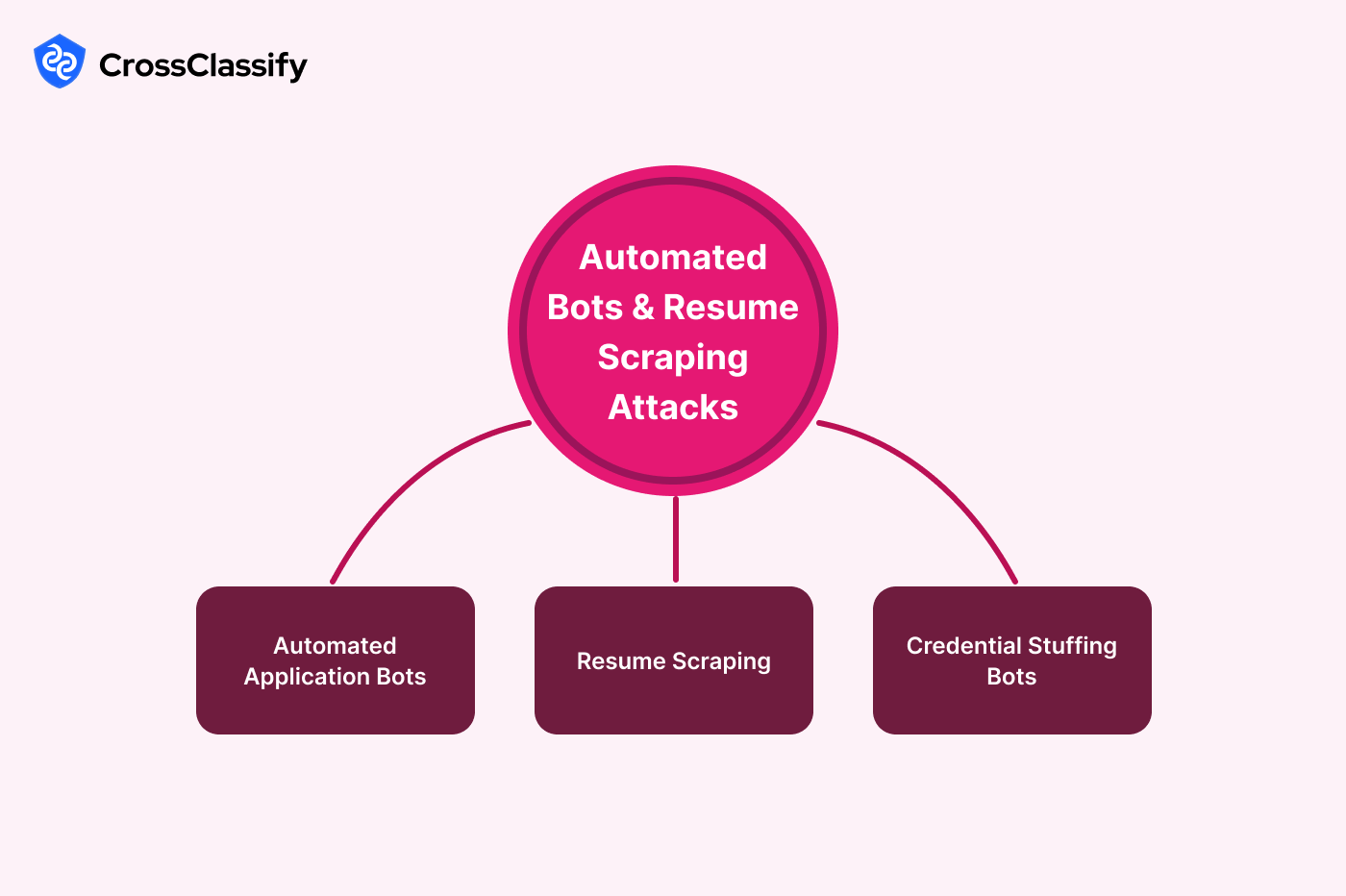

1. Automated Application Bots
Fraudsters use bots to apply to hundreds of jobs instantly.
Signals and Evidence:
- Applications per minute forming sharp bursts: Bots submit applications at machine speed. Evidence shows in time-series application graphs.
- Zero cursor activity and uniform keystroke latency: Human typing is variable; bots show uniform patterns. Evidence appears in keystroke latency histograms.
2. Resume Scraping
Unauthorized bots harvest resume databases for resale.
Signals and Evidence:
- Unusual volume of resume exports per recruiter account: Abnormal activity points to scraping. Evidence is captured in resume export dashboards.
- Sequential page hits at machine speed: Bots crawl profiles faster than humans can. Evidence is seen in page access rate graphs.
3. Credential Stuffing Bots
Fraudsters use breached credentials to log into recruitment accounts.
Signals and Evidence:
- High login failure rate from specific IP ranges: Credential stuffing creates clustered failures. Evidence appears in CIDR fail rate charts.
- Sudden spikes in username hit-rate: A sign of valid credential lists being tested. Evidence is displayed in success/failure ratio graphs.
Job Posting and Communication Scams
Fake job postings and fraudulent communications are the most visible type of recruitment fraud. These scams mislead candidates with promises of jobs, only to steal money or personal data. In 2021, the FBI reported more than $62 million in losses due to recruitment-related scams.
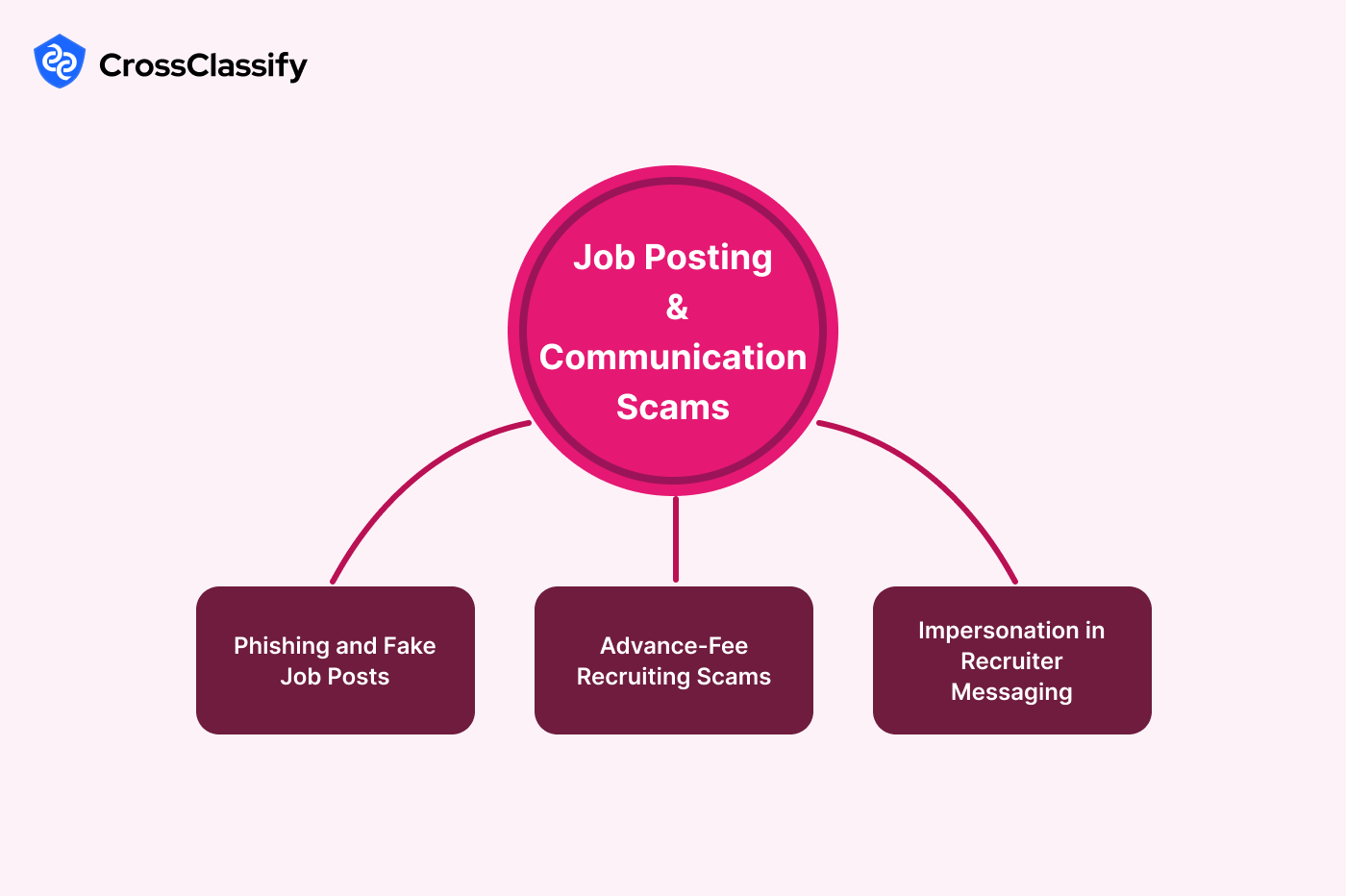

1. Phishing and Fake Job Posts
Fraudsters publish listings demanding payments or redirecting candidates to malicious sites.
Signals and Evidence:
- User reports of scam job categories: Spike in upfront fee or crypto-payment job posts. Evidence is captured in category report graphs.
- Redirects leading to credential-harvest websites: Fake jobs redirect to phishing portals. Evidence is displayed in redirect reputation tables.
2. Advance-Fee Recruiting Scams
Scammers request candidates to pay upfront fees for fake opportunities.
Signals and Evidence:
- Requests for payment before interviews: Payment-demanding language in job descriptions. Evidence appears in message NLP dashboards.
- Off-platform communication using throwaway accounts: Fraudsters move candidates off safe channels. Evidence is seen in network contact graphs.
3. Impersonation in Recruiter Messaging
Fraudsters spoof legitimate company names in direct messages.
Signals and Evidence:
- Brand-name spoofing in recruiter chat: Duplicate brand names in recruiter display. Evidence captured in collision dashboards.
- Sudden increase in DMs from new recruiters: New accounts spamming candidates at scale. Evidence is shown in DM volume graphs.
Payments, Credits, and Marketplace Abuse
Recruitment platforms often monetize with premium job postings, resume unlocks, or candidate credits. These features are attractive targets for payment fraud.

1. Stolen Card Fraud
Fraudsters use stolen credit cards to purchase premium access.
Signals and Evidence:
- Elevated chargeback rates on premium features: Sudden rise indicates fraud. Evidence is captured in chargeback trend graphs.
- Mismatch between card country and account location: Fraudsters often use mismatched regions. Evidence appears in transaction mismatch tables.
2. Refund and Chargeback Abuse
Bad actors exploit refund policiesfor free access.
Signals and Evidence:
- Used-then-refund patterns: Fraudsters unlock resumes and immediately request refunds. Evidence is in unlock vs refund graphs.
- Excessive disputes from a few recruiter accounts: Repeated disputes signal abuse. Evidence appears in dispute per account dashboards.
3. Promotional Abuse
Fraudsters exploit promo codes or referral schemes.
Signals and Evidence:
- Multiple redemptions from shared devices: Indicates promo abuse networks. Evidence is shown in device-promo network graphs.
- Sign-up-only activity followed by promo redemption: No real engagement besides promo usage. Evidence appears in retention vs promo usage graphs.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Recruitment fraud happens when scammers impersonate recruiters or create fake job postings to steal money or data. CrossClassify prevents this by combining device fingerprinting and behavioral monitoring. Learn more
Fake candidates use fabricated resumes or stolen identities to infiltrate platforms. CrossClassify uses AI-driven analytics and device fingerprinting to flag inconsistencies in resumes and signup patterns. Read more
Fake recruiters lure candidates into scams, data theft, and financial fraud. CrossClassify applies account opening fraud detection and continuous trust scoring to stop them. Details
Bots can flood job applications or scrape resumes for resale. CrossClassify detects bot attacks using behavioral biometrics and device fingerprints. Read more
Account takeover exposes both recruiters and candidates to fraud. CrossClassify monitors logins for anomalies and blocks suspicious access attempts. Learn more
Device fingerprinting uniquely identifies user devices to prevent multi-accounting and spoofing. CrossClassify integrates this into its recruitment fraud solution. More
Behavioral biometrics identifies bots and impersonators by analyzing typing patterns and mouse movements. CrossClassify applies these models to secure applications. Learn more
Phishing job posts trick candidates into sharing sensitive data. CrossClassify scans job descriptions and detects risky patterns using AI-driven fraud detection. See
Fraudsters exploit promos or referral credits to gain free access. CrossClassify applies device fingerprinting and anomaly detection to prevent promo abuse. Read
Continuous monitoring ensures fraud is detected in real-time, not just at signup. CrossClassify uses adaptive risk and trust assessment for ongoing protection. Details
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
