Last Updated on 17 Aug 2025
Navigating Fraud and Cybersecurity Risks in the Crypto Industry
Share in

Key Notes
•
In 2022, crypto scams caused over $3.8 billion in losses, demanding robust fraud prevention.•
34% of crypto-related fraud cases involve insider negligence or compromised internal access.•
Over 70% of modern attacks in DeFi platforms bypass MFA and WAF protections.
1. Introduction to the Crypto Industry
The crypto industry encompasses blockchain-based systems, decentralized finance (DeFi), cryptocurrency exchanges, NFT platforms, and wallets. At its core, it promises transparency, immutability, and decentralization. While this digital revolution has opened up a borderless financial ecosystem, its open and anonymous nature also makes it a lucrative target for fraudsters.
Key players in this industry include centralized exchanges (like Binance and Coinbase), DeFi protocols (like Uniswap and Aave), NFT platforms (like OpenSea), and custodial and non-custodial wallet providers. Despite its benefits, the lack of regulation, irreversible transactions, and pseudonymous identities expose the crypto ecosystem to unique and evolving security threats.
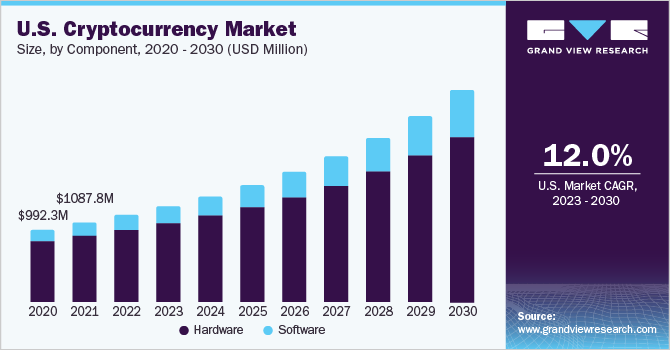
2. Market Size of the Crypto Industry
The global cryptocurrency market was valued at over $1.49 trillion as of 2024. According to Statista, more than 420 million people worldwide have used crypto services, with adoption seen in over 100 countries. The DeFi sector alone locked over $80 billion in total value in 2023, and the NFT market had sales exceeding $24 billion.With institutional players such as BlackRock and Fidelity entering the market, crypto is evolving beyond retail speculation into a recognized asset class and financial infrastructure.
3. Fraud Size in the Crypto Industry
The anonymous nature of crypto has given rise to a wide range of scams and attacks. In recent years, cryptocurrency-related scams cost users over $3.8 billion according to the Federal Trade Commission (FTC). Decentralized apps and exchanges are particularly vulnerable to bot-based manipulation, transaction laundering, and synthetic identities.
Fraud-as-a-service platforms allow bad actors to automate bonus abuse, credential stuffing, and account takeover. Meanwhile, social engineering, phishing, and impersonation scams continue to exploit gaps in user security awareness.
4. Real-World Cases of Fraud in the Crypto Industry
Numerous high-profile cases illustrate the scale and diversity of crypto fraud:
•
OneCoin: Marketed as a legitimate cryptocurrency, it was in fact a Ponzi scheme that defrauded investors of over $4.4 billion globally.•
BitConnect: Promised guaranteed returns using a trading bot, but collapsed as a classic pyramid scheme, costing investors billions.•
Rug Pulls: In DeFi, many tokens are launched only for developers to disappear with investor funds, such as the Squid Token scam.•
Pig Butchering: Scammers form emotional or financial relationships online, tricking victims into fake investments that seem profitable until the money disappears.•
Deepfake Investment Scams: Fraudsters use AI-generated videos of celebrities endorsing fake crypto investments, targeting social media users.

5. Main Consequences of Not Being Protected Against Fraud and Data Breach
Failing to protect against fraud in the crypto space can be devastating, not just for platforms but also for users and investors. The consequences include direct financial loss, regulatory penalties, user attrition, and long-term damage to brand reputation.
•
Monetary Losses: Fraud can drain liquidity from exchanges and wallets instantly. For DeFi platforms, a single exploit can result in millions lost within minutes.•
Reputational Damage: Crypto communities move fast. News of breaches or scams spreads quickly, eroding trust and user retention.•
Regulatory Sanctions: Without proper fraud prevention and identity verification, crypto businesses risk violating AML/KYC regulations and face legal action.•
VC & Institutional Hesitation: Investors hesitate to back platforms with unresolved security vulnerabilities, affecting growth and fundraising potential.•
Operational Disruption: Fraud incidents often require immediate halts in trading or user activity, disrupting business continuity.
6. Compliance Issues in the Crypto Industry
Compliance continues to be a major pain point for crypto exchanges and service providers. AML (Anti-Money Laundering) and KYC (Know Your Customer) requirements vary globally, making it difficult for decentralized platforms to align.
Governments and watchdogs are enforcing cross-border rules such as the FATF Travel Rule, which mandates crypto firms to track and share transaction data. Inadequate fraud detection or failure to verify identities can lead to fines, bans, and loss of operating licenses. Implementing tools like AML risk scoring for crypto sign-ups, real-time identity validation, and suspicious wallet activity monitoring are now necessary to maintain compliance and market presence.


7. Fraud Types in the Crypto Industry: Stats and Case Studies
•
Account Takeover: Attackers gain unauthorized access to user wallets or exchange accounts, often via phishing, credential reuse, or malware. These breaches often go unnoticed until assets are drained. (Read more)•
Synthetic Identity Fraud: Cybercriminals use a mix of real and fake data to create entirely new identities. These are then used to pass weak KYC systems and exploit sign-up rewards. (Read more)•
Multi-Account Fraud: One user controls multiple identities to game a system, from airdrops to staking rewards. This is often facilitated by bot networks.•
Bonus Abuse: Incentive programs attract fraudsters. They automate the abuse of referral or deposit bonuses, leading to massive financial leakage for platforms.•
Rug Pulls: Developers intentionally abandon or sabotage projects after collecting funds, leaving investors with worthless tokens.•
Deepfake & Impersonation Scams: Scammers create fake personas or deepfaked video messages, luring users to phishing sites or fraudulent tokens.•
Wallet Anomalies: Repeated patterns like rapid fund withdrawal, access from geographically distant IPs, or simultaneous login attempts signal abuse.•
Transaction Laundering: Illicit actors obfuscate the source of stolen funds using mixing tools or cross-chain bridges to avoid detection.
8. Insider Threat in the Crypto Domain
Insider threats are often overlooked in cybersecurity strategies. They go beyond malicious intent and include human error, lack of awareness, and negligent access sharing. In the crypto domain, even a single employee mistake, such as exposing a private key or misconfiguring access controls, can lead to irreparable damage.
As detailed in this article, insider threats come in four categories: malicious insiders, negligent users, compromised credentials, and shadow IT. Real-world examples include leaked smart contract source code or admins mistakenly granting backdoor access. Visibility and internal monitoring are as vital as external threat detection.
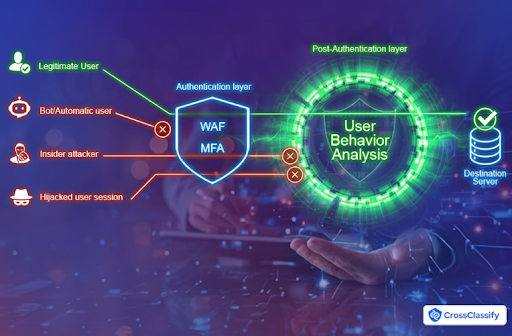
9. Why MFA and WAF Are Not Enough in Crypto
Traditional safeguards like MFA (Multi-Factor Authentication) and WAF (Web Application Firewall) are no longer sufficient. Attackers have evolved, and so must the defenses.
MFA can be bypassed using phishing kits, social engineering, and OTP-stealing bots. Attackers also exploit human error, like approving a malicious transaction prompt, to breach wallets. Similarly, WAFs only detect known threat signatures and struggle with behavioral anomalies or bot-generated traffic mimicking legitimate users.
As emphasized in this analysis, behavior-based, context-aware protection is the next step forward. Crypto businesses need real-time threat intelligence combined with user profiling to catch what static rules cannot.

10. Emerging Trends and Use-Case-Based Innovations
•
Pig Butchering Scam Detection Tools: By monitoring relationship-building behaviors and unusually high transaction encouragement patterns, platforms can identify romance or friendship scams early.•
Deepfake Defense Systems for Crypto Exchanges:AI-generated video detection paired with identity verification workflows can prevent users from falling victim to impersonated endorsements.•
Cross-Wallet Behavior Anomaly Detection:Evaluating how wallets interact across DeFi platforms, including gas usage and contract interactions, allows better fraud profiling.•
Crypto Transaction Pattern Risk Scoring: Machine learning models can score transactions based on historical behavior, peer-to-peer activity, and engagement with suspicious wallets.•
Multi-Account Farm Prevention SDK: By fingerprinting devices and behavioral traits, platforms can block users from registering dozens of fake accounts using automation.
11. How CrossClassify Helps Protect Crypto Organizations from Fraud
CrossClassify delivers specialized protection tailored to the crypto domain, offering deep insight into fraud vectors and user behavior. Its features are mapped directly to crypto risks:
•
Continuous Monitoring for Crypto Activities:Ongoing analysis of user interactions uncovers hidden attack patterns over time. Read more•
Behavior Analysis for Web3 Users: Identifies how legitimate users navigate and use the platform, helping detect bots, farms, and manipulated flows. Read more•
Geo Analysis for Wallet Access: Flags anomalies in login geolocations and access velocity that indicate shared or compromised credentials. Read more•
Link Analysis of Blockchain Interactions:Correlates blockchain wallet activities with known fraud rings or bots operating across multiple exchanges. Read more•
Enhanced Security and Accuracy for Crypto Platforms:Filters false positives while strengthening fraud defenses through combined behavioral, device, and identity signals. Read more•
Seamless Integration for Crypto Exchanges: SDKs and APIs allow fast and robust deployment across DeFi apps, custodial wallets, and on-chain interfaces. Read more•
Alerting and Notification System: Timely detection and instant alerts help security teams act before the fraud escalates. This real-time response system significantly reduces fraud dwell time.
12. Conclusion
The crypto landscape is rich with opportunity but riddled with threats. From insider negligence to cross-chain laundering, the methods of fraud continue to outpace static security tools. Advanced actors now use AI, social engineering, and multi-vector attacks to target platforms and users alike. Fraud impacts not just user funds but platform survival, regulatory standing, and investor confidence.
CrossClassify empowers crypto organizations to build with confidence. Through its AI-powered fraud detection, device fingerprinting, continuous monitoring, and behavioral analytics, CrossClassify offers a multi-layered shield tailored to the decentralized world. Whether you're a DeFi innovator, exchange operator, or NFT marketplace, CrossClassify provides the visibility, context, and real-time intelligence needed to stop fraud before it starts.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Account takeover protection in crypto exchanges is crucial as attackers use phishing and malware to hijack user credentials or wallets. CrossClassify protects against this threat through device fingerprinting, behavioral session tracking, and anomaly detection across login flows. Learn more
Crypto onboarding fraud detection software must identify bots, fake identities, and multi-account farms exploiting promos or airdrops. CrossClassify detects automation and synthetic IDs through behavioral analytics and real-time device intelligence. Read more
MFA bypass protection for crypto platforms is essential, as phishing kits and OTP interception tools render MFA alone ineffective. CrossClassify enhances security using behavior-based profiling and post-authentication activity monitoring to catch anomalies that MFA misses. See full analysis
Synthetic ID detection for DeFi onboarding is key to prevent fraud rings from exploiting KYC loopholes. CrossClassify's behavioral biometrics and identity trust scoring flags inconsistent or mismatched identity signals in real time. Learn more
Multi-account fraud detection for crypto platforms requires continuous monitoring of device IDs, behavioral traits, and linkages. CrossClassify uses link analysis to expose shared infrastructure and flag account collusion. Details here
Insider threat detection for crypto companies is critical, especially when private keys or admin access is mishandled. CrossClassify detects suspicious internal behavior, privilege misuse, and session anomalies to identify negligence or compromise. Explore types of insider risk
Bot protection for decentralized crypto apps must include behavior analytics and device fingerprinting to detect non-human patterns in trading, staking, or signup flows. CrossClassify's solution detects real-time automated behavior, even across distributed interfaces. See techniques
Referral abuse fraud prevention in crypto apps protects platforms from promo-driven exploitation. CrossClassify combines behavioral analysis and link mapping to detect incentive abuse from shared or spoofed devices. Learn more
AML and KYC risk scoring in crypto platforms requires real-time fraud detection and user validation. CrossClassify enriches compliance workflows with identity analysis, continuous session scoring, and behavioral baselines. Read about risk management
AI-powered fraud detection for crypto exchanges combines behavioral, device, and geo-contextual insights. CrossClassify filters noise and delivers high-confidence alerts with low false positives, enabling teams to act faster. See full capabilities
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required