Last Updated on 17 Aug 2025
Cybersecurity and Fraud Prevention in the Mining Industry
Share in

Key Notes
•
Over $4 billion in cyber fraud losses hit the mining industry in recent years, with 35% linked to insider threats and credential abuse.•
Only 38% of mining companies claim to be fully compliant with cybersecurity regulations.•
Traditional security like MFA and WAF are bypassed in 67% of targeted attacks.
Introduction to the Mining Industry
The mining industry plays a critical role in the global economy, supplying the raw materials essential for infrastructure, energy, and technological advancement. As operations digitalize, the industry has become increasingly vulnerable to fraud and cyberattacks. From industrial control systems to remote exploration data, the attack surface continues to grow. Adversaries ranging from organized criminals to state-sponsored groups now see mining as a high-value, under-protected target. Whether it is intellectual property theft or manipulation of production metrics, the consequences can be severe.
Market Size of the Mining Industry
The global mining industry is projected to reach a value of $2.5 trillion by 2030, according to Statista. It employs over 10 million people across more than 100 countries. Major sectors include coal, metals, rare earths, and precious minerals. With over 50,000 operational mines and thousands of subcontractors, the digital interconnectivity and global scale of the sector open it up to significant cybersecurity risks. Key partners include equipment vendors, logistics providers, and exploration firms, creating a complex and often vulnerable value chain.
Fraud Size in the Mining Industry
Cyber-enabled fraud in the mining sector has exceeded $4 billion globally in recent years. According to PwC, fraud and economic crime are reported by 47% of mining firms surveyed. These include both external cyberattacks and internal collusion. Credential theft, insider manipulation, and vendor abuse are common. The Australian Cyber Security Centre warns that ransomware targeting critical mining infrastructure has increased by 40% in the past three years (ACSC).
Real-World Cases of Fraud in the Mining Industry
Fraud in mining is not a theoretical risk, it's a growing reality. Real-world incidents demonstrate how devastating these attacks can be:
•
FBI Case – Arizona Mining Scam: A fake mining operation convinced dozens of investors to commit over $10 million. It used doctored images, falsified geological surveys, and fake staff identities. The FBI discovered there was no mining site, leading to a federal investigation and multiple arrests.•
Insider Data Leak – Reddit Case: A disgruntled former employee leaked confidential exploration data for a lithium project, which caused a 12% drop in the stock value of the parent company. The leaked documents revealed projected yields and operational delays, causing investor panic.•
Zambia Procurement Fraud: Fake vendor profiles were inserted into a mining firm's procurement system. Over 15 invoices were paid out to shell companies before the fraud was caught during an external audit, costing the company nearly $750,000.•
Cryptojacking in Kazakhstan: Attackers infected geological analysis servers with cryptomining malware. The malware consumed significant processing power, delayed exploration timelines, and cost the firm over $150,000 in wasted electricity and IT response efforts.•
Fake Gold Mine Syndicate: A fraud ring in South Africa sold non-existent gold mine shares to foreign investors, leading to $22 million in international losses before it was dismantled by Interpol.

Main Consequences of Not Being Protected Against Fraud and Data Breaches
Failing to implement proactive fraud prevention measures leads to significant short- and long-term consequences across multiple dimensions:
•
Operational Disruption: A single ransomware or insider sabotage event can halt mining equipment, production lines, and logistics for days. Downtime in a medium-sized mine can cost $1–3 million per day.•
Financial Loss: Fraud-related losses can include fake supplier payouts, lost investments, penalties, or ransom demands. Fraudulent reporting can also mislead shareholders and tank stock performance.•
Reputational Damage: Publicly reported breaches can cause investor exodus, loss of business partners, and reputational stigma in the global commodity markets.•
Legal and Compliance Risks: Mining companies are increasingly bound by KYC, AML, ESG, and critical infrastructure regulations. A data breach or compliance failure could lead to heavy regulatory fines and even operational license revocation.•
Environmental and Safety Hazards: Manipulated data can result in inaccurate reporting on tailing dams, ventilation, or toxic exposure levels, posing severe threats to worker safety and environmental integrity.
Compliance & Regulatory Pressures in the Mining Sector
Mining companies operate under stringent regulations due to their economic significance and environmental impact. In recent years, cybersecurity and financial crime compliance have become top priorities:
•
Anti-Money Laundering (AML) and Know Your Customer (KYC): Required in countries where mined commodities are traded or exported. Failure to detect suspicious transactions can lead to blacklisting or asset freezes.•
Environmental, Social, and Governance (ESG) Compliance: Falsifying ESG metrics, either internally or by third-party auditors, has become a form of fraud. Regulators now inspect these metrics more rigorously.•
Data Privacy and Cybersecurity Policies: Mining firms must comply with GDPR, POPIA, and Australia's Critical Infrastructure Bill, mandating the protection of sensitive personnel, investor, and operational data.•
SEC Reporting and Stock Exchange Oversight: For publicly traded mining companies, fraudulent misrepresentation of production, earnings, or ESG scores can result in delisting and class-action lawsuits.

Fraud Types in the Mining Industry: Stats and Case Studies
Mining fraud manifests in various ways, targeting digital systems, physical operations, and financial frameworks:
•
Investment Fraud: Fraudulent mining ventures, non-existent exploration sites, and falsified claims are sold to investors. According to FINRA, resource scams rank in the top 5 for investor complaints in 2023.•
Account Takeover: Criminals use phishing, malware, or brute-force to gain access to mining dashboards, SCADA systems, and ERP tools. These takeovers can redirect production flows or siphon off funds. More•
Internal Abuse: Employees abuse their position to manipulate production logs, redirect shipments, or approve fraudulent payments. One case in Australia involved an engineer logging nonexistent ore extraction for bonus incentives.•
Vendor & Multi-Account Abuse: Fraudsters register fake vendor accounts using shell companies to repeatedly bill the mining company with varied invoice patterns.•
Cryptojacking & Malware: Hackers exploit under-monitored servers or geological simulators for illegal crypto mining, causing overheating, reduced performance, and massive electric costs.•
Smurfing & AML Violations: Criminal groups use shell firms and microtransactions to launder illegal gains through mining equipment purchases or licensing deals.
Insider Threats in Mining: The Hidden Danger
Insiders continue to be one of the most underestimated sources of fraud and risk in the mining sector. Their access to sensitive data, control systems, and high-trust environments makes them particularly dangerous. According to CrossClassify, there are four types of insider threats:
•
Negligent Insiders: These users cause harm through careless behavior, like reusing passwords, clicking on malicious links, or storing credentials in shared documents.•
Compromised Insiders: These accounts are taken over by external actors. Because access seems legitimate, these intrusions often go undetected for long periods.•
Malicious Insiders: These actors intentionally sabotage systems, leak proprietary information, or manipulate processes to benefit themselves or competitors.•
Collusive Insiders: Employees who work with external fraudsters to abuse procurement, tamper with exploration data, or enable unauthorized transactions.
Mining environments need behavioral monitoring and zero-trust access models to detect these nuanced threats.
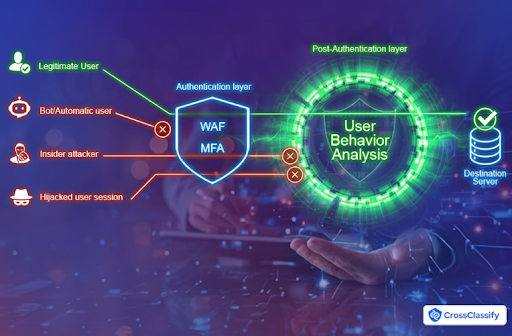
Why MFA and WAF Are Not Enough for the Mining Sector
Traditional security solutions like MFA (multi-factor authentication) and WAF (web application firewall) are no longer sufficient on their own. As demonstrated in this article, modern attackers can easily bypass these defenses:
•
SIM Swap and MFA Fatigue: Criminals intercept MFA codes or trigger repeated login attempts until users accept them by mistake.•
Device Spoofing and IP Manipulation: Tools replicate device fingerprints and locations, making them appear trustworthy to perimeter systems.•
Fileless Malware: These scripts operate in-memory and can bypass WAFs by abusing trusted applications.•
Phishing with Credential Replay: Once MFA is intercepted, credentials can be reused across multiple mining services or portals.
Mining companies must adopt continuous, AI-powered behavioral analytics and real-time risk scoring to supplement traditional methods.

Emerging Threats and Mining-Specific Use Cases
The landscape of fraud and cyber threats in mining is evolving. Emerging threats now focus on automation, identity fraud, and data manipulation:
•
AI-Driven Anomaly Detection: Detects fraudulent changes in geological modeling, predictive maintenance data, and control system outputs using machine learning.•
Continuous Behavioral Analytics: Monitors normal vs. abnormal interaction with mine control platforms to flag potential fraud.•
Device Fingerprinting for Mining Infrastructure: Ensures only approved devices are used to access high-risk systems like SCADA or ERP tools.•
Multi-Account and Vendor Fraud Detection: Uses pattern matching and link analysis to detect similar fraud techniques across different user or vendor profiles.•
AML Risk Scoring and Smurfing Detection: Scores users based on transaction frequency, value, and counterparties to reveal money laundering in commodity sales.•
Cryptojacking Detection: Spots unauthorized crypto mining scripts in servers meant for simulation, exploration, or production modeling.•
Insider Access Risk Analytics: Scores insiders based on behavioral deviation from role expectations and historical norms.
How CrossClassify Helps Protect Mining Organizations from Fraud
CrossClassify delivers a mining-focused fraud prevention platform built for modern, digitized operations. Its features include:
•
Continuous Monitoring: Detect and respond to real-time anomalies across mining platforms, dashboards, and IoT endpoints. See more•
Behavior Analysis: Profiles miners, engineers, vendors, and contractors based on access and activity patterns. Explore•
Geo Analysis: Flags logins from unexpected countries or devices accessing centralized mining software. See how•
Link Analysis: Connects the dots between vendors, insiders, and suspicious transactions across time. Details•
Enhanced Security and Accuracy: Uses layered scoring models to reduce false positives and ensure only real threats are flagged. More here•
Seamless Integration: Easily plugs into mining ERP, HR, vendor, and production systems. How it works•
Alerting and Notification: Sends immediate alerts to cyber teams, shift supervisors, or security leads when threat indicators arise. Reduces mean time to detect and mitigate.
Conclusion
As the mining sector continues its digital transformation, the risks associated with fraud, insider threats, and cyber vulnerabilities grow in scale and complexity. The financial, reputational, legal, and environmental costs of not taking action are staggering, and rising. Traditional security tools like MFA and WAF, while important, are simply not enough to tackle the sophisticated fraud patterns seen today.
CrossClassify empowers mining organizations with an intelligent, mining-specific defense system. From continuous behavioral monitoring to advanced fraud detection through device fingerprinting, it offers comprehensive protection against both known and emerging threats. By integrating seamlessly into existing infrastructure, CrossClassify equips mining companies with the agility and precision needed to stay ahead of fraud in a high-stakes industry.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Mining account takeover prevention is critical as attackers exploit weak credentials or phishing to infiltrate SCADA dashboards and production controls. CrossClassify stops this by combining real-time behavioral profiling and device fingerprinting to flag anomalies before damage occurs. Read more
Mining insider threat detection software must monitor internal user behavior, not just access logs. CrossClassify tracks deviations from expected behavior, flags suspicious access, and uses risk scoring to detect negligent or malicious insiders. Explore the types
Mining cybersecurity platforms beyond MFA and WAF are now essential, as attackers use phishing kits, SIM swaps, and fileless malware to bypass these controls. CrossClassify adds behavioral intelligence and continuous monitoring to detect sophisticated fraud patterns. Full analysis
Vendor fraud detection in mining procurement systems helps uncover fake invoices, multi-account abuse, and shell company setups. CrossClassify connects the dots through link analysis and behavioral scoring to reveal hidden fraud rings. Learn more
Device fingerprinting for mining cybersecurity ensures only trusted devices access critical systems like ERP, SCADA, or geological databases. CrossClassify identifies spoofed or risky devices, blocking unauthorized access and detecting early-stage compromise. See more
Behavioral analytics for mining fraud prevention helps distinguish normal user behavior from fraud attempts, such as fake ore logs, off-hour access, or privilege abuse. CrossClassify analyzes click paths, timing, and role-based expectations to catch threats early. Explore the tech
Mining compliance monitoring tools should detect fraud across financial transactions, KYC processes, and environmental metrics. CrossClassify supports regulatory compliance by scoring anomalies and ensuring data integrity across endpoints. Learn how
Cryptojacking detection in mining IT infrastructure is vital as hackers hijack underutilized systems for illegal crypto mining. CrossClassify detects hidden resource drain and unauthorized execution patterns through continuous monitoring. See article
Geo analysis in mining cybersecurity platforms reveals suspicious login origins, such as sudden access from unexpected countries or time zones. CrossClassify flags geo inconsistencies and correlates them with account behavior for faster threat detection. Learn how
Link analysis in mining fraud prevention tools maps relationships between insiders, vendors, and access patterns to detect collusion. CrossClassify uses link correlation to reveal shared infrastructure or behavioral similarities across users. See how it works
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required