Last Updated on 07 Sept 2025
Fraud and Cybersecurity Risks in the Accounting Industry: A Complete Guide for Prevention and Protection
Share in
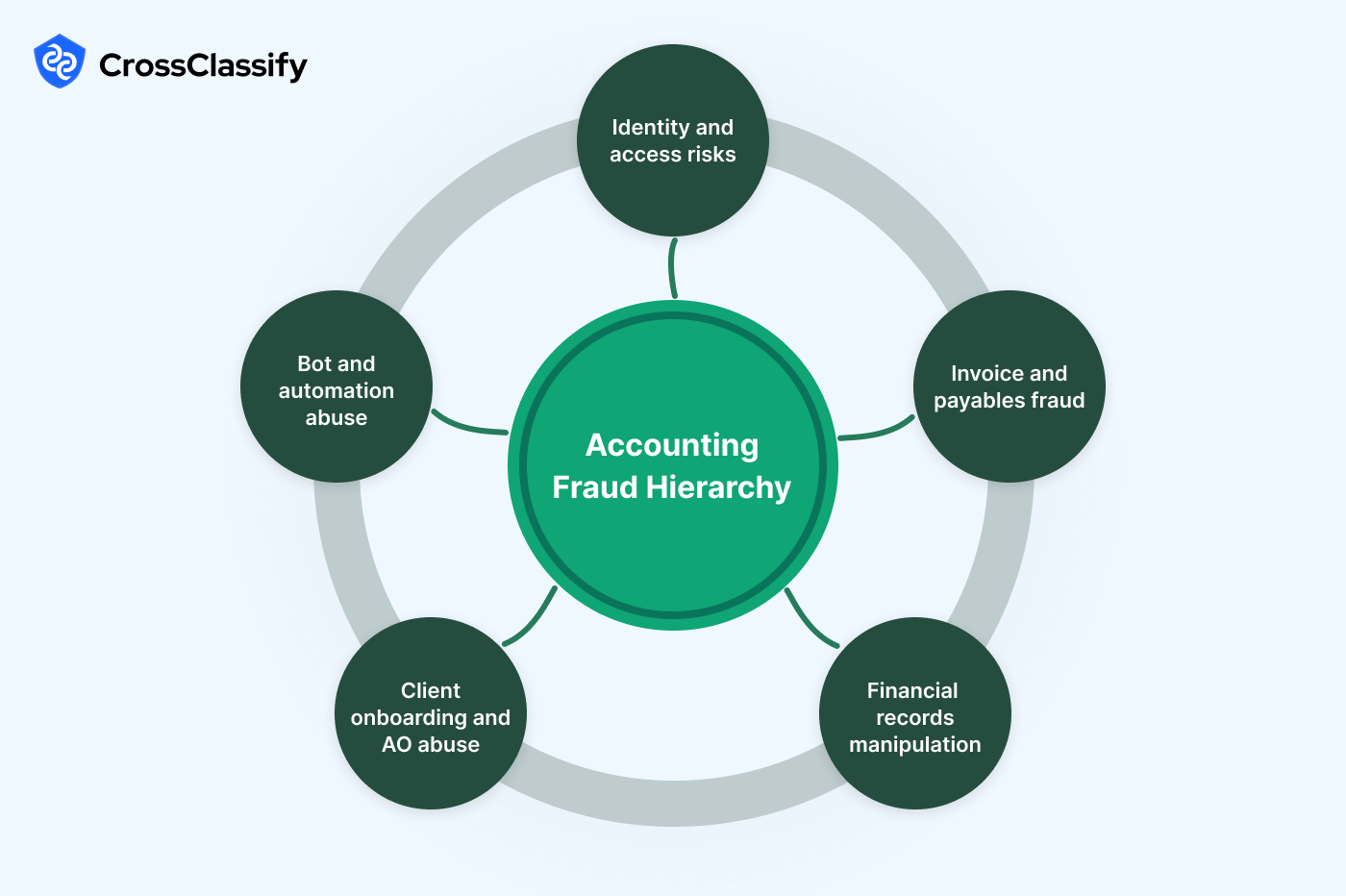
Introduction
The accounting industry is the backbone of financial integrity, regulatory compliance, and global trust. With rapid digital transformation, the sector faces increasing risks of accounting fraud, cybersecurity threats in accounting software, and financial statement manipulation in accounting firms. Fraudsters exploit weaknesses in account takeover protection for accounting systems, account opening fraud detection for accounting firms, and bot attack prevention for financial platforms. Without effective protection, accounting firms risk financial losses, reputational damage, and regulatory fines. This article presents a comprehensive fraud hierarchy for the accounting industry, detailing fraudulent patterns, real-world signals, and how CrossClassify delivers advanced fraud detection and prevention.
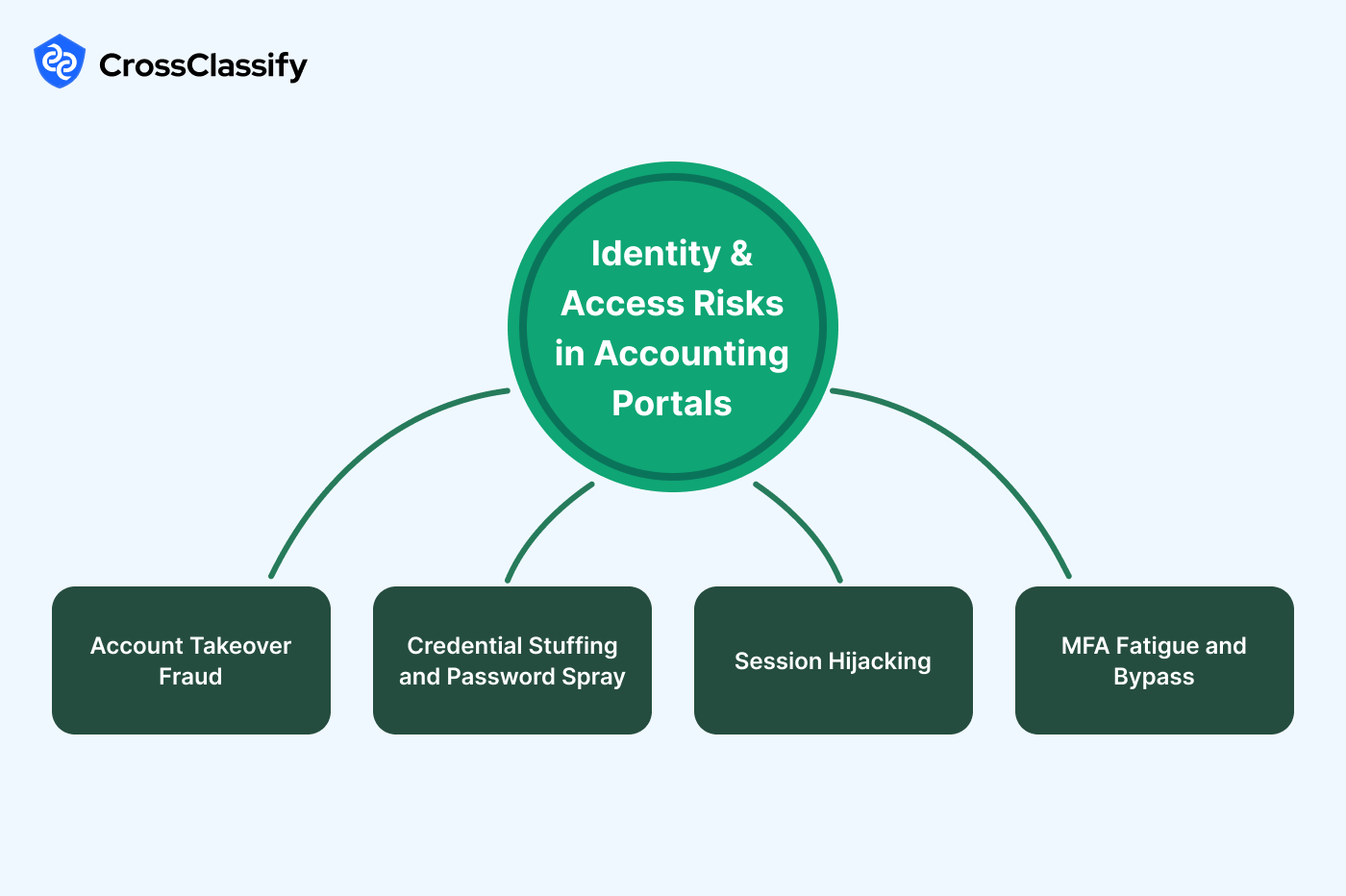
Identity and Access Risks in Accounting Portals
Identity and access risks in accounting systems expose sensitive data such as ledgers, payroll, and tax filings to cybercriminals. Unauthorized access can result in stolen financial data, fraudulent approvals, or the manipulation of accounting records. The most pressing categories include account takeover fraud in accounting platforms, credential stuffing attacks on accounting portals, session hijacking in accounting applications, and multi-factor authentication fatigue attacks in financial systems.

1. Account Takeover Fraud in Accounting Applications
Account takeover fraud in accounting platforms is one of the fastest growing cyber threats. Attackers use stolen or brute-forced credentials to access legitimate accounts. Once inside, they can alter financial statements, authorize payments, or extract sensitive information. In 2021, a U.S. tax preparation firm experienced widespread breaches caused by credential stuffing, which compromised thousands of accounts.
- New login from unfamiliar device and geolocation mismatch: A Geo-Device Login Map highlights login origins. Passing results show consistent trusted devices. Failing results reveal red markers from distant regions or unknown devices, which indicate account takeover attempts.
- Surge of failed logins followed by a success: A Failed vs Success Login Timeline visualizes login activity. Passing firms show stable trends. Failing firms show spikes of failures followed by a successful attempt, which is a typical brute-force pattern.
2. Credential Stuffing and Password Spray in Accounting
Credential stuffing attacks in accounting systems rely on stolen username and password combinations. Password spray attacks in accounting portals involve trying a few common passwords across many accounts. Both exploit weak authentication and can lead to unauthorized access. Successful attacks can compromise payroll systems, tax records, and client data.
- High login attempts per IP or user agent burst: An IP Attempt Distribution Graph highlights abnormal activity. Passing systems show even distribution. Failing systems reveal extreme attempts from a few IPs, pointing to automated bots.
- Password spray across many accounts: A Username Spray Matrix detects broad attempts. Passing matrices show no patterns. Failing matrices reveal horizontal rows that expose password spraying.
3. Session Hijacking in Accounting Platforms
Session hijacking in accounting applications occurs when attackers steal or reuse active session tokens. Hijacking allows access without entering credentials, bypassing MFA and login systems. This type of fraud can expose sensitive financial records and tax data.
- Session token reused from different IPs: A Token Reuse Timeline tracks token usage. Passing timelines show consistent activity from one IP. Failing timelines reveal sudden IP switches, which is a hijacking signal.
- Concurrent sessions from distant geolocations: A Concurrent Session Count Dashboard reveals abnormal logins. Passing dashboards show low concurrency. Failing dashboards display multiple sessions from different regions, confirming hijacked accounts.
4. MFA Fatigue and Bypass in Accounting Systems
MFA fatigue attacks in accounting portals exploit human error by overwhelming users with repeated MFA prompts. Once users approve a fraudulent request, attackers gain full access. Accounting firms using weak MFA implementations are especially vulnerable.
- Multiple MFA prompts declined then one approval: An MFA Prompt Outcome Timeline shows approval behavior. Passing systems display smooth activity. Failing systems show repeated declines followed by a single suspicious approval.
- Users switching from app-based MFA to SMS: A MFA Method Change Table shows risky downgrades. Passing systems remain on app-based MFA. Failing systems show spikes in SMS usage, which is easier to intercept.
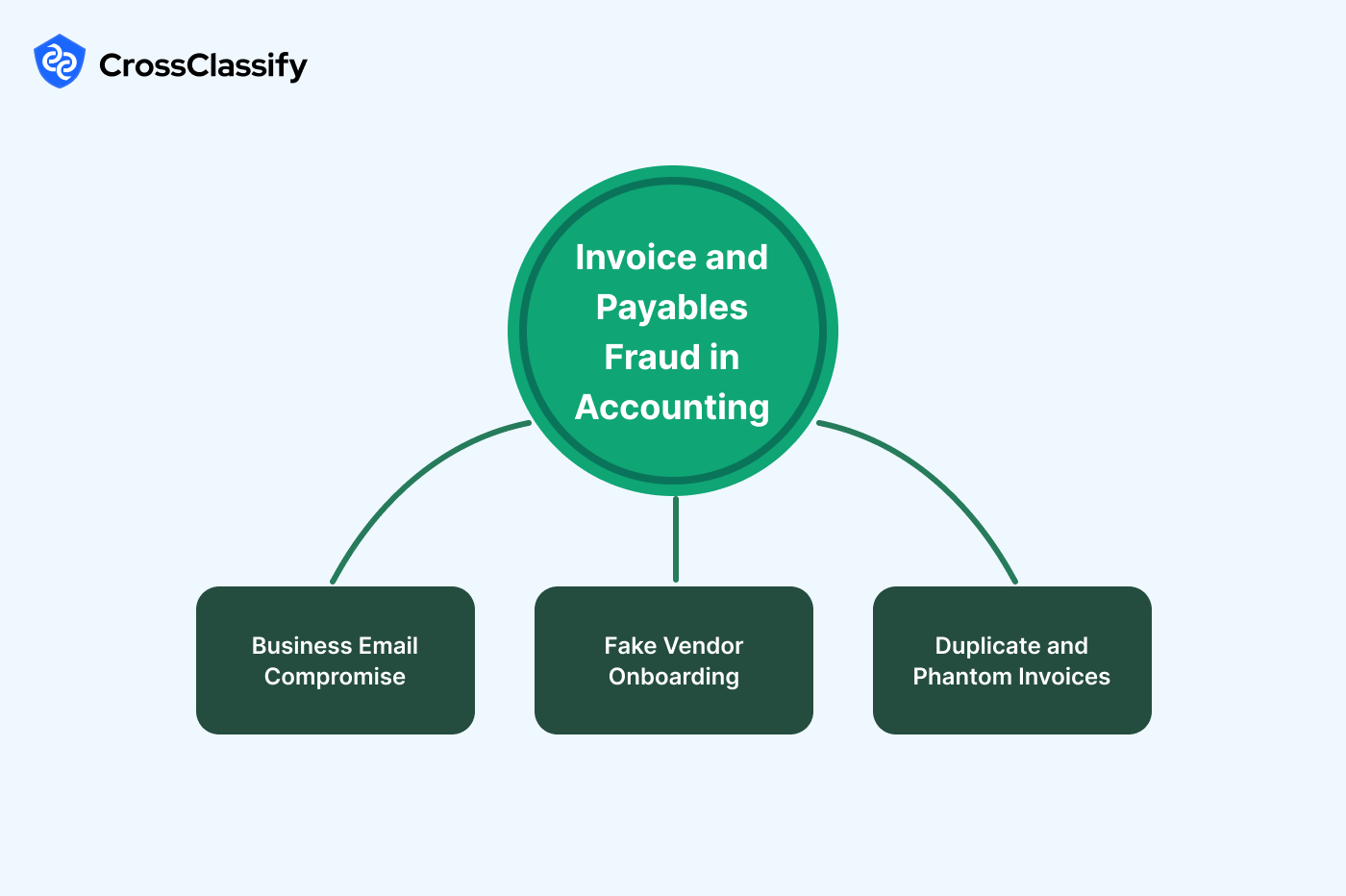
Invoice and Payables Fraud in Accounting
Invoice fraud in accounting firms and accounts payable fraud in financial systems remain serious threats. These include business email compromise in accounting, fake vendor onboarding in accounting systems, and phantom invoice fraud detection in accounts payable departments. According to the FBI, Business Email Compromise caused over 1.7 billion dollars in global losses in 2019.

1. Business Email Compromise in Accounting Payments
BEC in accounting systems occurs when criminals impersonate vendors or executives to redirect legitimate payments. Attackers often spoof domains or compromise email accounts.
- Vendor bank details changed shortly before a payment: A Payment After Bank Change Chart reveals timing. Passing results show stable data. Failing results highlight large payments made soon after bank detail changes.
- Payer email domain resembles vendor domain: A Domain Similarity Score Bar shows spoofing attempts. Passing bars remain low. Failing bars spike above thresholds, revealing impersonation.
2. Fake Vendor Onboarding in Accounting
Fake vendor onboarding fraud in accounting software involves criminals creating false vendor accounts to siphon payments. Internal collusion can also contribute.
- Same employee creates many vendors rapidly: A Creator-to-Vendor Dashboard highlights unusual behavior. Passing dashboards show balanced vendor creation. Failing dashboards show one employee responsible for many vendors.
- Duplicate IBAN or Tax ID across vendors: A Duplicate IBAN Table reveals reuse. Passing tables show unique identifiers. Failing tables expose duplicates that indicate fraudulent vendors.
3. Duplicate and Phantom Invoices in Accounting
Duplicate invoices in accounting platforms and phantom invoices in accounts payable exploit weaknesses in validation processes. Fraudsters may reuse purchase order numbers or create invoices outside contract periods.
- Same PO, amount, and date repeats: A Duplicate Invoice Heatmap reveals clusters. Passing systems show no concentration. Failing systems highlight repeated values, signaling fraud.
- Invoices dated outside contract period: An Out-of-Period Invoice Timeline shows anomalies. Passing systems align with contracts. Failing systems show irregularities beyond valid dates.
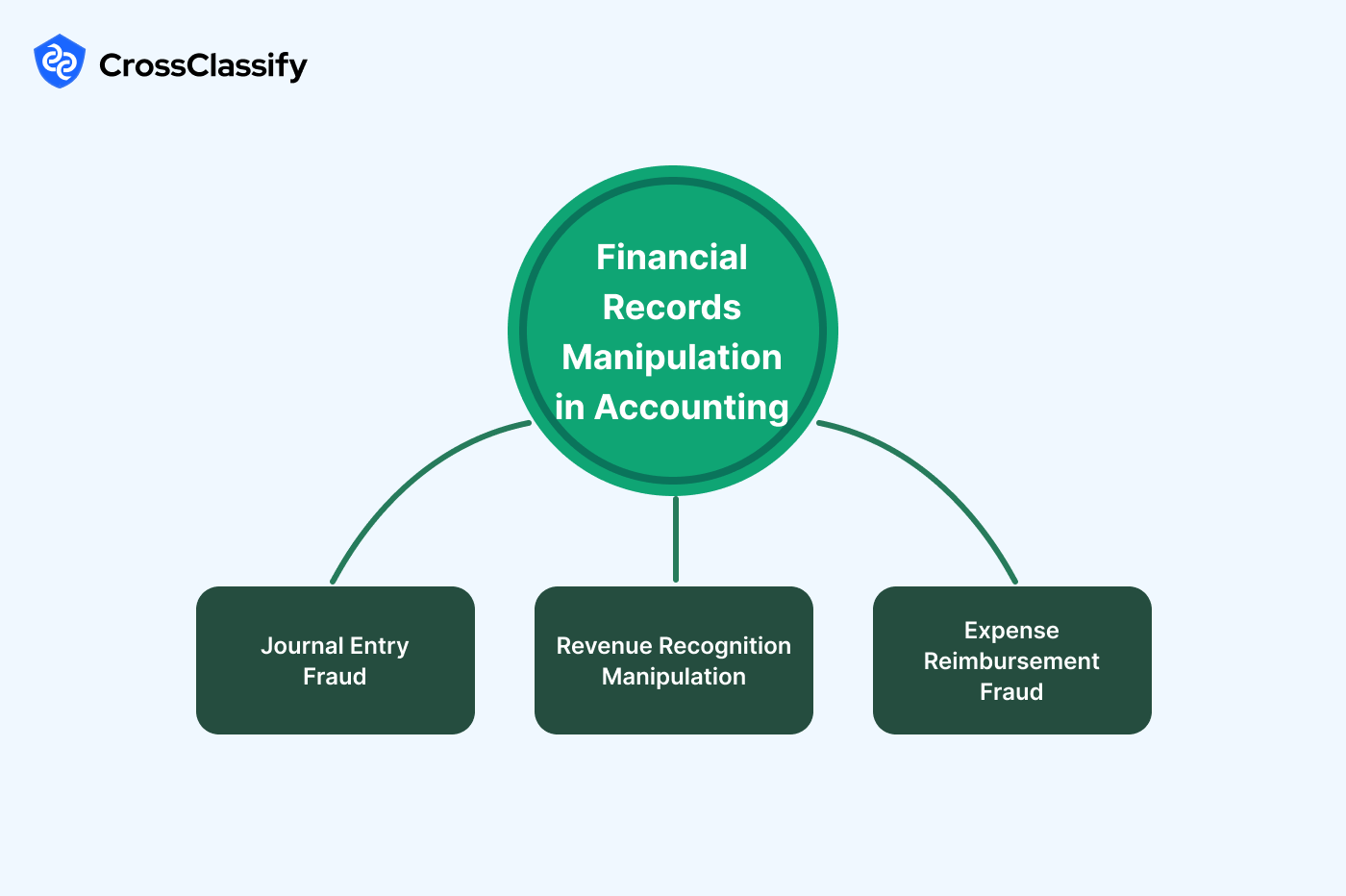
Financial Records Manipulation in Accounting
Financial manipulation in accounting systems is one of the most dangerous fraud types. It involves altering journal entries, manipulating revenue recognition, or inflating expenses. Such practices undermine trust in financial reports and can lead to corporate scandals. Firms must apply strict internal controls and automated fraud detection to prevent manipulation.

1. Journal Entry Fraud in Accounting
Journal entry fraud in accounting platforms happens when unauthorized or false entries are posted. Fraudulent entries are often inserted at odd hours or without approvals. This type of fraud can create inflated profits or hidden liabilities.
- After-hours manual entries above threshold: An After-hours Journal Entries Histogram reveals patterns. Passing firms show few late entries. Failing firms display spikes during nights and weekends, suggesting manipulation.
- Missing secondary approval on large entries: An Approval Gap Table highlights approval chain issues. Passing results show complete approvals. Failing results show repeated missing reviews for large transactions.
2. Revenue Recognition Manipulation
Revenue recognition fraud in accounting systems is a classic manipulation technique. Firms may record revenue earlier than allowed or without matching cash flow. Such manipulation can inflate financial performance reports.
- End-of-period revenue spikes: A Revenue Spike Chart highlights abnormalities. Passing data shows smooth transitions. Failing data reveals sharp increases at reporting deadlines.
- Revenue recorded without matching cash flow: An AR Aging vs Revenue Scatter detects imbalances. Passing systems align revenue with cash receipts. Failing systems reveal receivables without actual payments.
3. Expense Reimbursement Fraud
Expense fraud in accounting departments involves employees inflating or falsifying expense claims. It is one of the most common fraud risks in corporate accounting.
- Rounded amounts at thresholds: A Rounded Expense Distribution Graph highlights unusual patterns. Passing firms show smooth distributions. Failing firms show sharp spikes at exact thresholds.
- Weekend or holiday claims: A Claims by Day-of-Week Bar shows submission dates. Passing results remain low on weekends. Failing results spike outside normal workdays.
Client Onboarding and Account Opening Abuse in Accounting
Account opening fraud in accounting applications introduces fake clients, stolen identities, and mule accounts into financial systems. Fraudsters use synthetic profiles, reused identity documents, and manipulated KYC processes to gain access.

1. Synthetic Client Profiles
Synthetic client fraud in accounting firms happens when criminals create fake accounts using fabricated or mismatched data.
- ID or DOB checksum inconsistency: An Error Rate Graph shows mismatches. Passing graphs stay flat. Failing graphs spike, showing identity manipulation.
- Shared device across many new clients: A Device-to-New-Client Table exposes account farming. Passing results show few overlaps. Failing results show repeated device use.
2. Stolen Identity Enrollment
Stolen identity fraud in accounting portals involves criminals reusing stolen documents or personal data.
- Document image reuse across applicants: A Document Hash Reuse Graph highlights repeated images. Passing graphs show unique files. Failing graphs show spikes of reuse.
- IP geolocation far from claimed address: A Geo Distance Histogram shows distance mismatches. Passing firms show short distances. Failing ones reveal long anomalies.
3. Mule Accounts
Mule accounts in accounting systems are used to launder money by quickly moving funds in and out.
- Many payees added soon after onboarding: A New Payees Timeline highlights risky behavior. Passing systems show low activity. Failing systems show spikes immediately after onboarding.
- Rapid pass-through of funds: An In-Out Flow Ratio Graph identifies laundering. Passing graphs show varied ratios. Failing graphs hug a 1.0 ratio, showing in equals out.
Bot and Automation Abuse in Accounting Portals
Bot abuse in accounting systems is one of the most common attack vectors. Bots attempt credential stuffing, data scraping, and denial of service attacks against accounting applications.

1. Credential Stuffing Bots
Automated bots launch large-scale login attempts against accounting systems.
- RPS bursts against login endpoints: A Requests per Second Timeline identifies spikes. Passing timelines remain flat. Failing timelines show surges of activity.
- Headless automation user agents: A User-Agent Distribution Bar highlights automated browsers. Passing bars show legitimate browsers. Failing bars show abnormal automation tools.
2. Data Scraping in Accounting Applications
Scraping threatens the confidentiality of financial statements and tax records.
- Sequential page walks: An Endpoint Pattern Chart shows usage patterns. Passing charts show random navigation. Failing charts reveal strict sequences typical of bots.
- High statement download volume per IP: A Downloads per IP Bar reveals abnormal scraping. Passing bars are balanced. Failing bars spike on a few IPs.
3. Denial of Service During Tax Deadlines
DoS attacks in accounting portals aim to disrupt services during peak tax filing periods.
- Elevated 429 or 503 error rates: An HTTP Error Timeline shows errors. Passing systems stay stable. Failing systems spike during deadlines.
- Regional traffic surges: A Traffic Heatmap reveals overloads. Passing heatmaps are balanced. Failing heatmaps highlight regional hotspots.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Account takeover in accounting occurs when criminals hijack accounts with stolen credentials. CrossClassify prevents this with device fingerprinting and adaptive MFA. Learn more
Invoice fraud drains funds through duplicate or fake invoices. CrossClassify detects anomalies with behavioral analytics. Learn more
Credential stuffing uses stolen passwords to infiltrate systems. CrossClassify blocks this with bot detection. Learn more
Fake vendors are uncovered through duplicate IBAN detection and employee activity monitoring. CrossClassify stops this with AI onboarding analysis. Learn more
Mule accounts launder money through rapid transfers. CrossClassify applies behavioral analysis and transaction monitoring. Learn more
Revenue fraud misleads investors and regulators. CrossClassify prevents this with reconciliation and anomaly detection. Learn more
KYC bypass happens through repeated retries and weak checks. CrossClassify enforces retry limits and liveness scoring. Learn more
Bots execute stuffing, scraping, and overload attacks. CrossClassify blocks bots with automation fingerprinting. Learn more
Behavioral biometrics detect unusual typing and navigation patterns. CrossClassify applies these in real time to secure portals. Learn more
Continuous monitoring is essential for early fraud detection. CrossClassify applies adaptive risk assessment and ongoing monitoring. Learn more
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
