Secure account takeover protection with real-time behavioral detection
Identify and stop suspicious users in milliseconds using behavioral risk scoring

Solution
ATO issues we resolve
CrossClassify detects and blocks the following attack vectors
Remote Access Fraud Detection
Stop unauthorized remote access fraud by detecting login attempts from suspicious IPs, virtual machines, or remote desktop tools that mimic legitimate users.
Credential Stuffing Attack Prevention
Block credential stuffing attacks by identifying bot patterns, repeated failed logins, and reused credentials with CrossClassify’s behavior-based scoring engine.
Phishing-Based Login Defense
Detect and mitigate phishing-based account takeovers by analyzing unusual access behavior, unfamiliar devices, and risky location changes during login.
DDoS-Driven ATO Diversion Blocking
Identify DDoS attacks used as ATO distractions by monitoring simultaneous high-traffic events and alerting against credential testing during diversion attempts.
SIM Swap & Device Takeover Defense
Prevent SIM swapping and device-based account fraud by scoring login attempts with telco metadata, device fingerprinting, and biometric inconsistencies.
Stolen Token & Malware Protection
Detect malware-based token theft and hijacked sessions by analyzing token anomalies, user behavior mismatches, and suspicious session refreshes.
Impersonation & Fake Identity Blocking
Stop impersonation attacks and fraudulent sessions by detecting behavioral deviations and session anomalies that reveal fake or cloned user identities.
Keylogging, Smishing, and Phishing Defense
CrossClassify identifies smishing and keylogging attempts by analyzing typing patterns, input behavior, and compromised device indicators in real-time.
Session Hijacking Threat Prevention
Prevent session hijacking attacks by continuously monitoring behavior, device shifts, and network anomalies throughout the user session lifecycle.
Our Approach to ATO Protection
We use the latest industry-level technologies to monitor and detect abnormal activities to prevent account takeover.
Continuous Monitoring for Account Takeover Risk
Detect and respond to account takeover fraud attempts in real-time with continuous monitoring of user behavior, device changes, and session anomalies. CrossClassify tracks every digital signal, before, during, and after login, to flag suspicious account activity that static rules might miss.
Stay ahead of evolving attack vectors like credential stuffing and session hijacking with proactive monitoring.
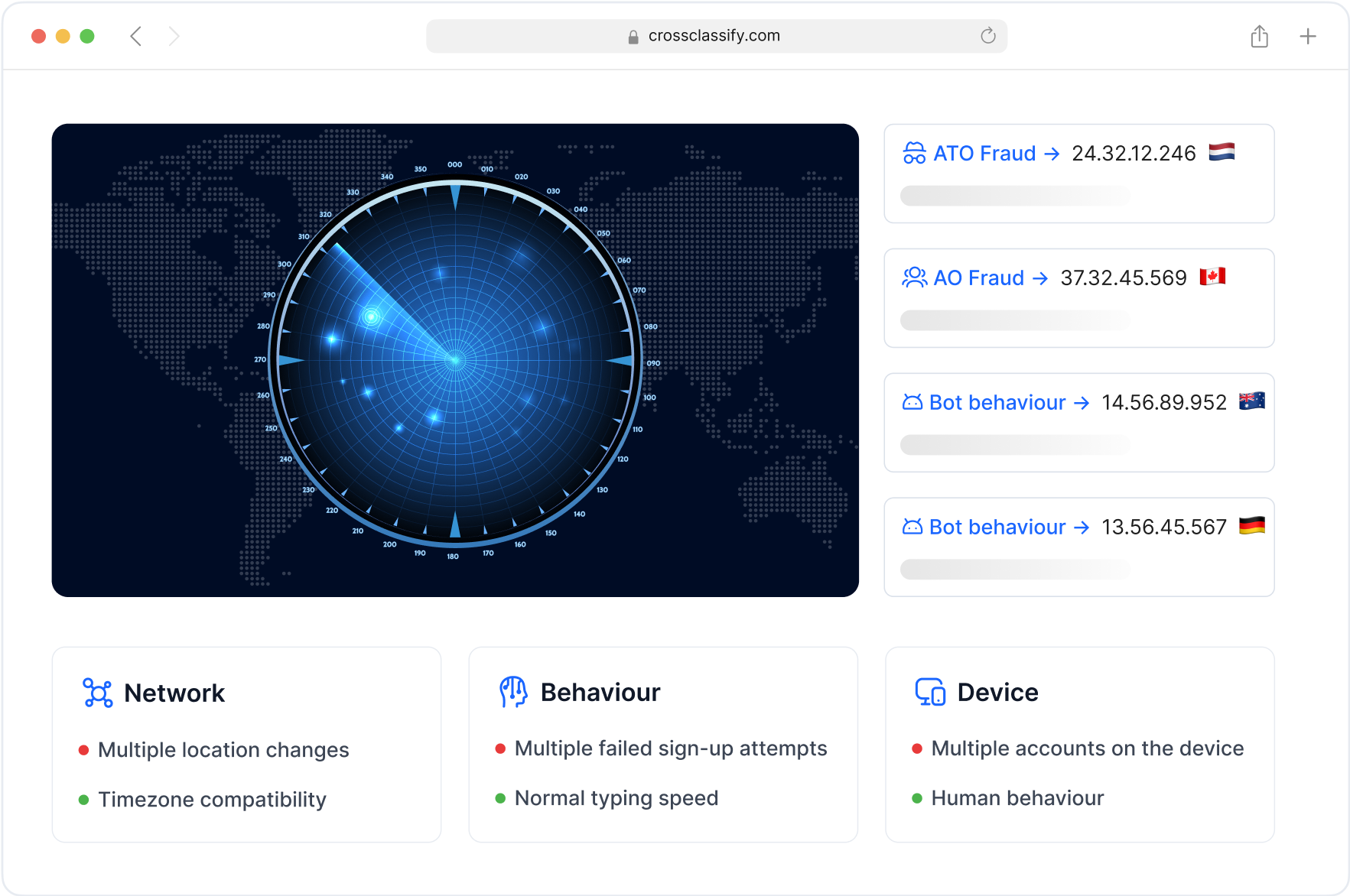
Behavior Analysis to Prevent Unauthorized Access
Stop unauthorized access with advanced behavior analysis that identifies abnormal login patterns, keystroke anomalies, and navigation behavior inconsistent with the user’s digital identity.
Our system detects impersonation attempts, even when fraudsters use valid credentials, by continuously comparing session behavior against historical patterns.
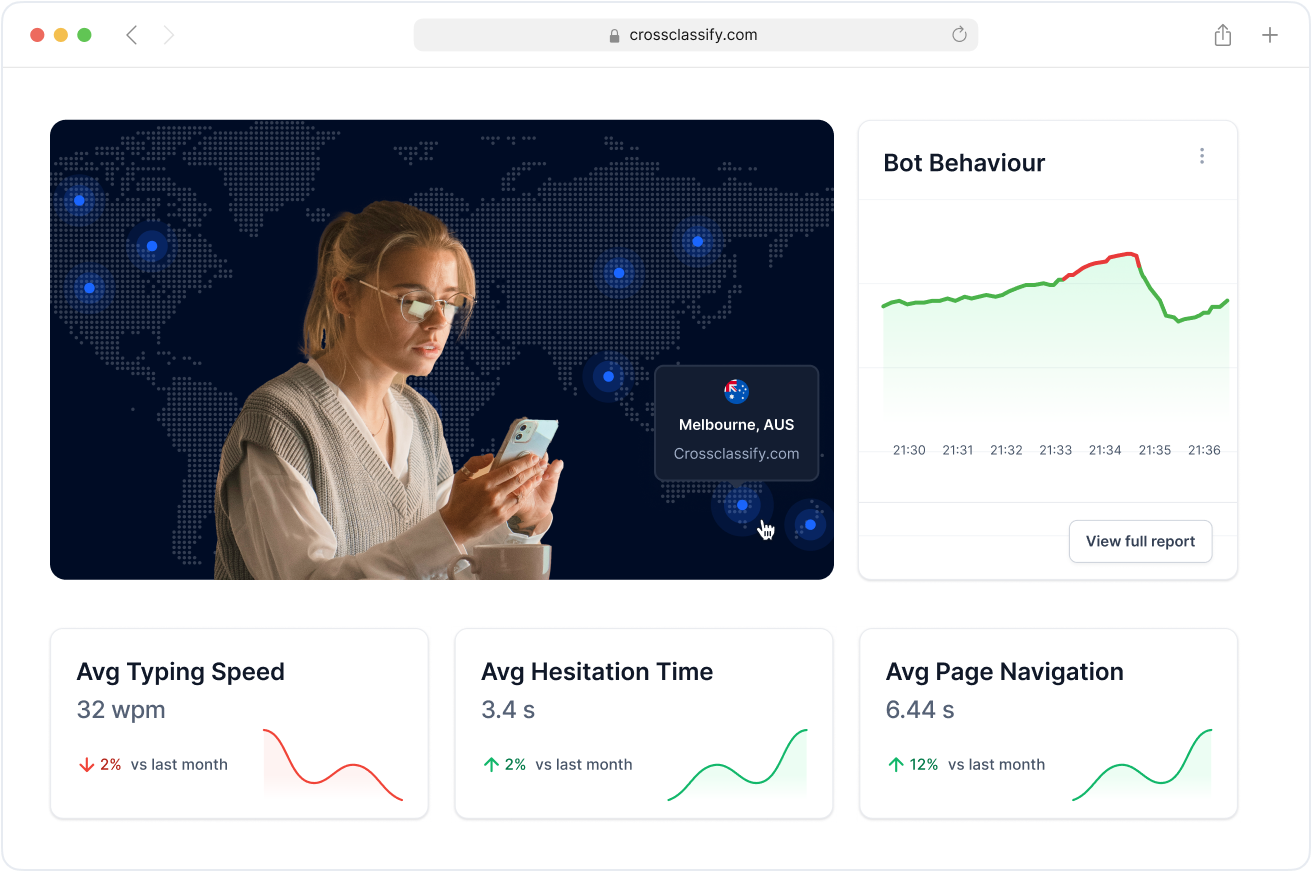
Geo Analysis to Detect Risky Logins
Flag geo-inconsistent logins and impossible travel scenarios, common indicators of account takeover attacks.
CrossClassify’s geo analysis uses IP, GPS, and device metadata to determine whether a session location aligns with the user’s normal behavior and risk profile.
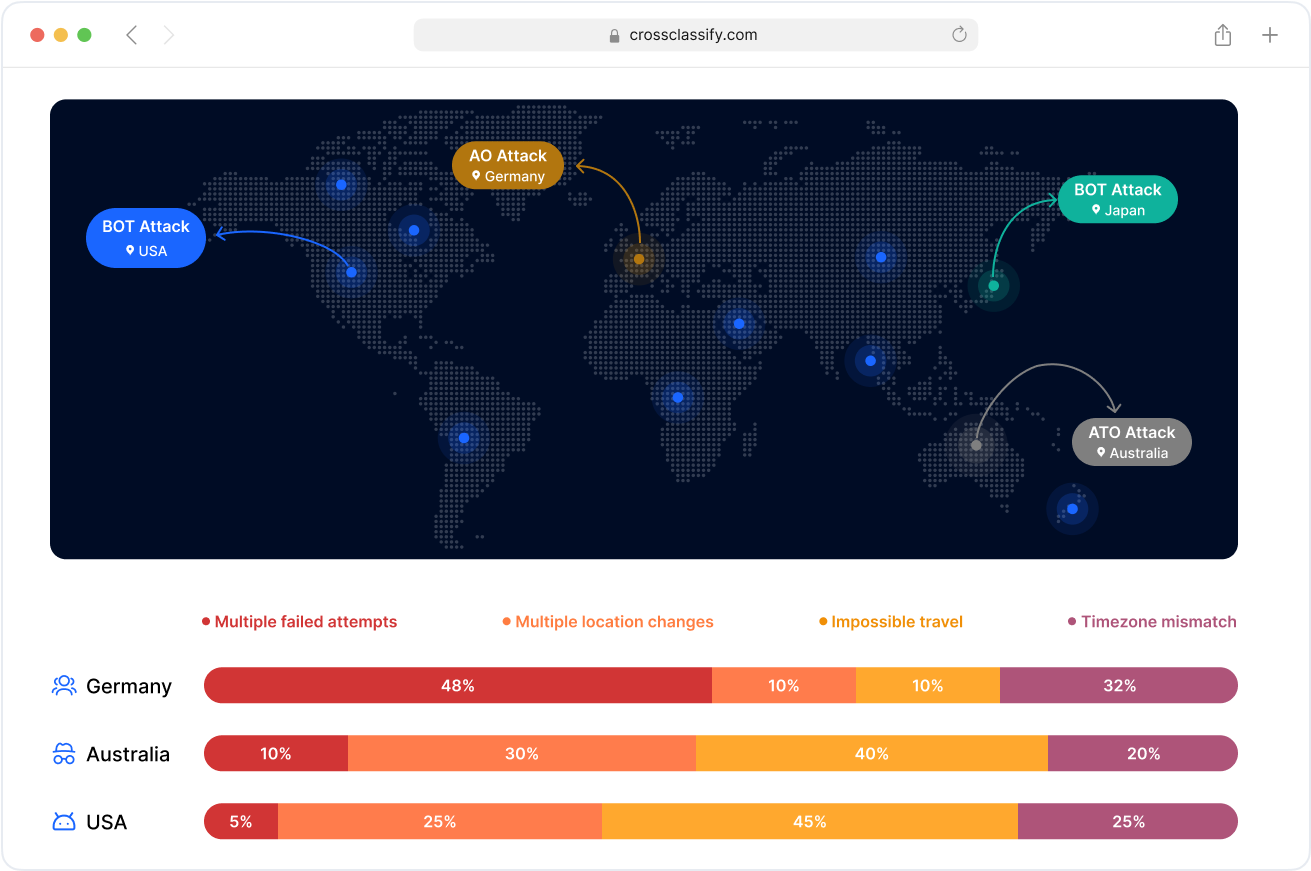
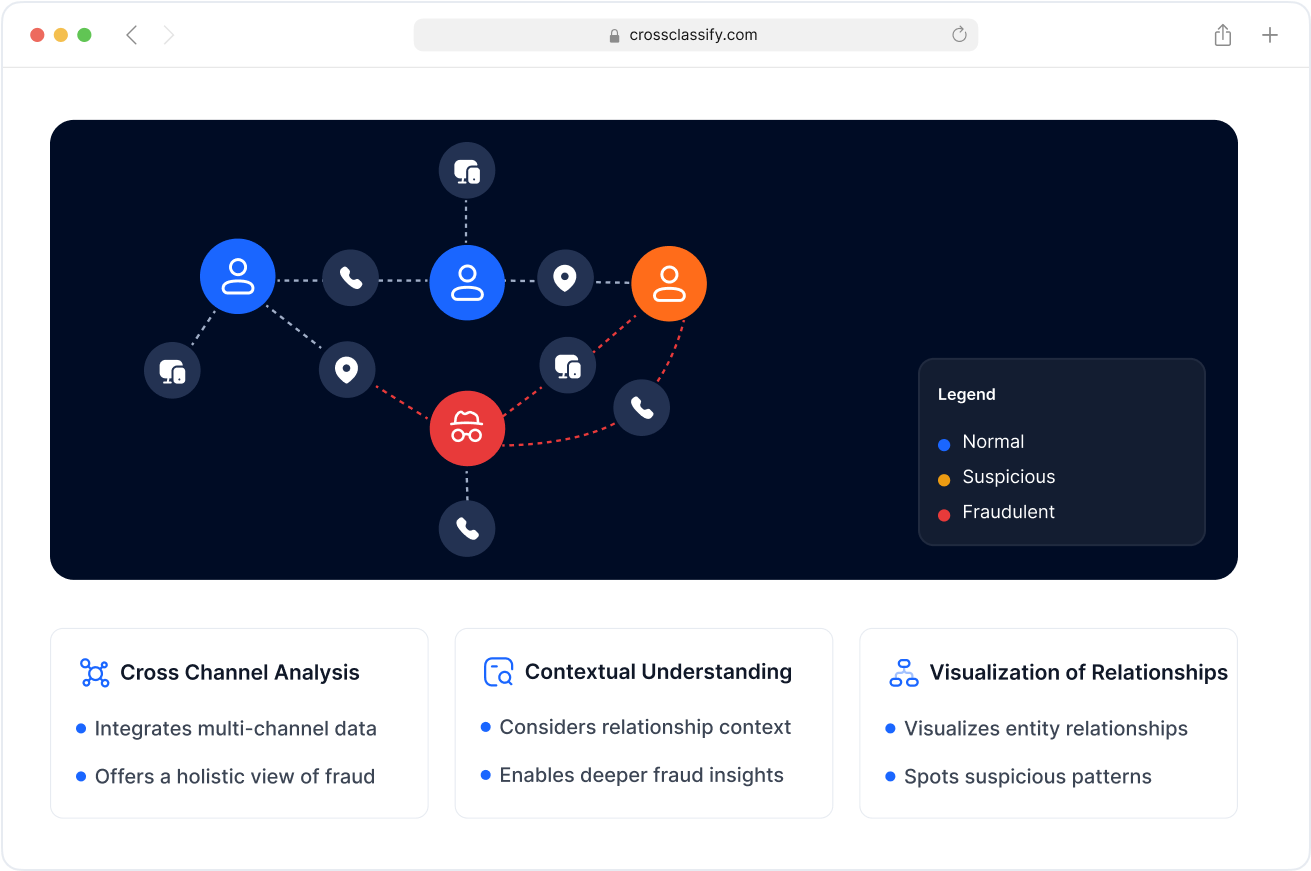
Link Analysis for Attack Pattern Detection
Visualize and analyze relationships between fraudulent login events, devices, and shared infrastructure used in coordinated account takeover campaigns.
Link analysis helps uncover fraud rings and repeat attack patterns, improving threat attribution and blocking at the network level.
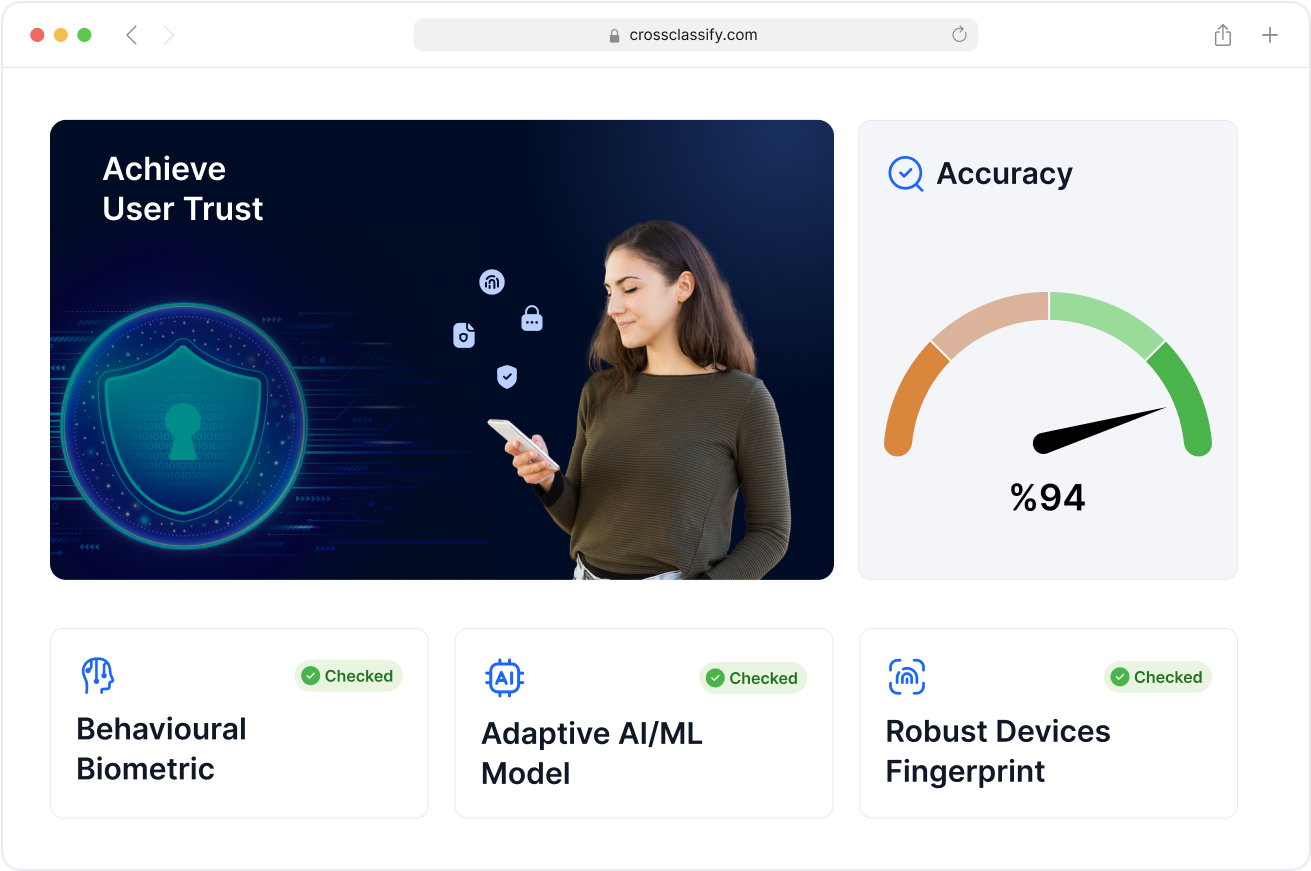
Enhanced Security and Accuracy in ATO Detection
Combine device fingerprinting, behavioral biometrics, and real-time risk scoring to deliver precise, low-friction protection against account takeover fraud.
CrossClassify enhances both security accuracy and user trust by reducing false positives and blocking only high-risk access attempts.
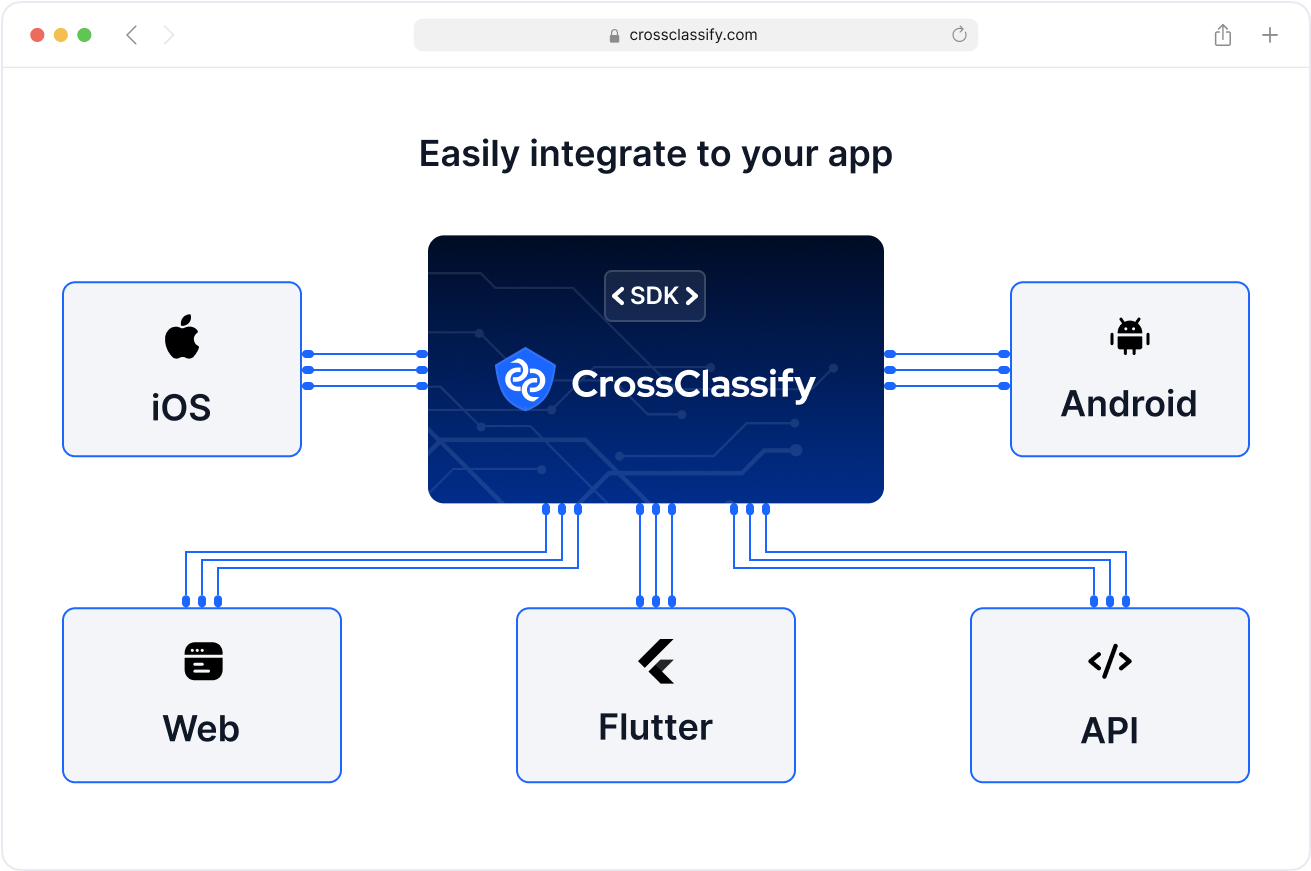
Seamless Integration with Existing Tech Stack
Integrate account takeover protection into your current login systems, identity providers, and fraud controls with minimal code changes.
CrossClassify offers flexible SDKs, APIs, and event-based webhooks to support enterprise-grade fraud defense without friction.
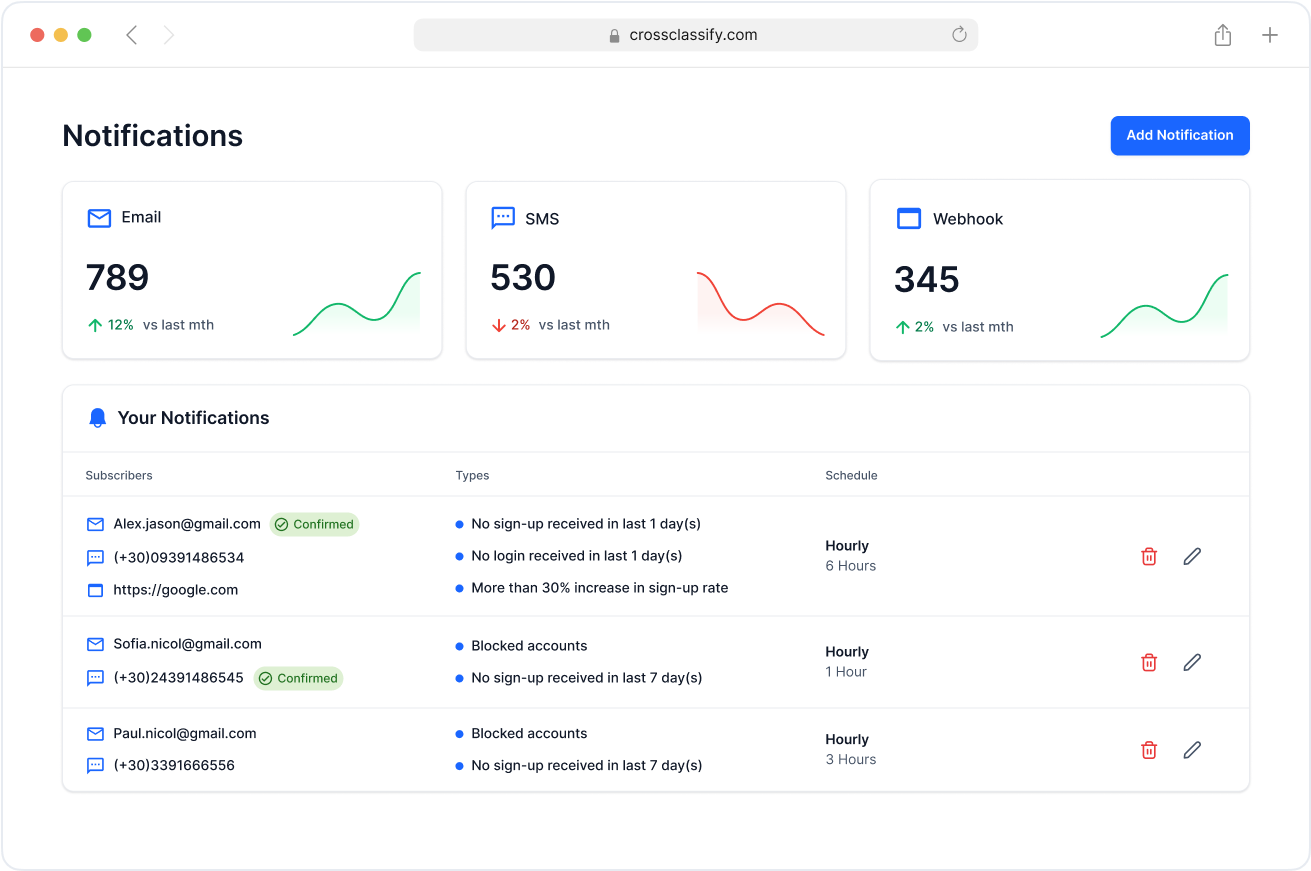
Alerting and Notification for Real-Time ATO Response
Receive real-time alerts for suspicious account behavior, credential stuffing, or session hijacking attempts.
CrossClassify ensures fraud and security teams are instantly informed about high-risk ATO events, enabling immediate investigation and action.
Blog
Latest from Cross Classify
Frequently asked questions
CrossClassify prevents this with real-time behavior detection , device fingerprinting, and adaptive risk tracking to catch anomalies before breach.
Read more
CrossClassify employs AI-driven behavioral models to detect subtle interaction anomalies that signal credential reuse or session hijacking.
Read more
CrossClassify watches for irregular login flows and device‑session anomalies to catch suspicious access even if valid credentials are used.
Read more
CrossClassify layers behavioral baselines and device signal analysis to flag risks that static systems overlook.
Read more
CrossClassify applies multi-layer device profiling to block high-risk login attempts and stop credential stuffing bots in real time.
Read more
CrossClassify integrates continuous risk scoring, session validation, and behavior monitoring to secure accounts across these environments.Read more in our articles on Fintech cybersecurity and cloud app security.
CrossClassify implements CARTA to allow frictionless access for trusted users while escalating checks for high-risk sessions.
Read more
CrossClassify deploys millisecond-level session analysis, stopping fraud early and ensuring real-time ATO protection.
Read more
CrossClassify links account takeover detection with identity fraud analytics to prevent escalations and reduce broader fraud risk.
Read more
CrossClassify identifies these through onboarding behavior analysis and flags unusual application patterns early.
Read more
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required