Last Updated on 19 May 2025
Odoo Security Best Practices: How CrossClassify Enhances Protection
Share in

Key Notes
•
85%of data breaches involve human elements, including phishing and credential abuse (Verizon DBIR 2023). CrossClassify prevents such risks via behavioral analytics.•
66% of organizations deploying ERP face insider threats (Cybersecurity Insiders). CrossClassify addresses this using UBA and device intelligence.•
WAF and MFA alone miss 40% of fraud attempts (CrossClassify article). CrossClassify adds intelligent, frictionless defense layers to Odoo.
What is Odoo?
•
Over 7 million users worldwide•
44,000+ apps in its marketplace•
Active in 120+ countries•
Backed by 3,000+ implementation partners

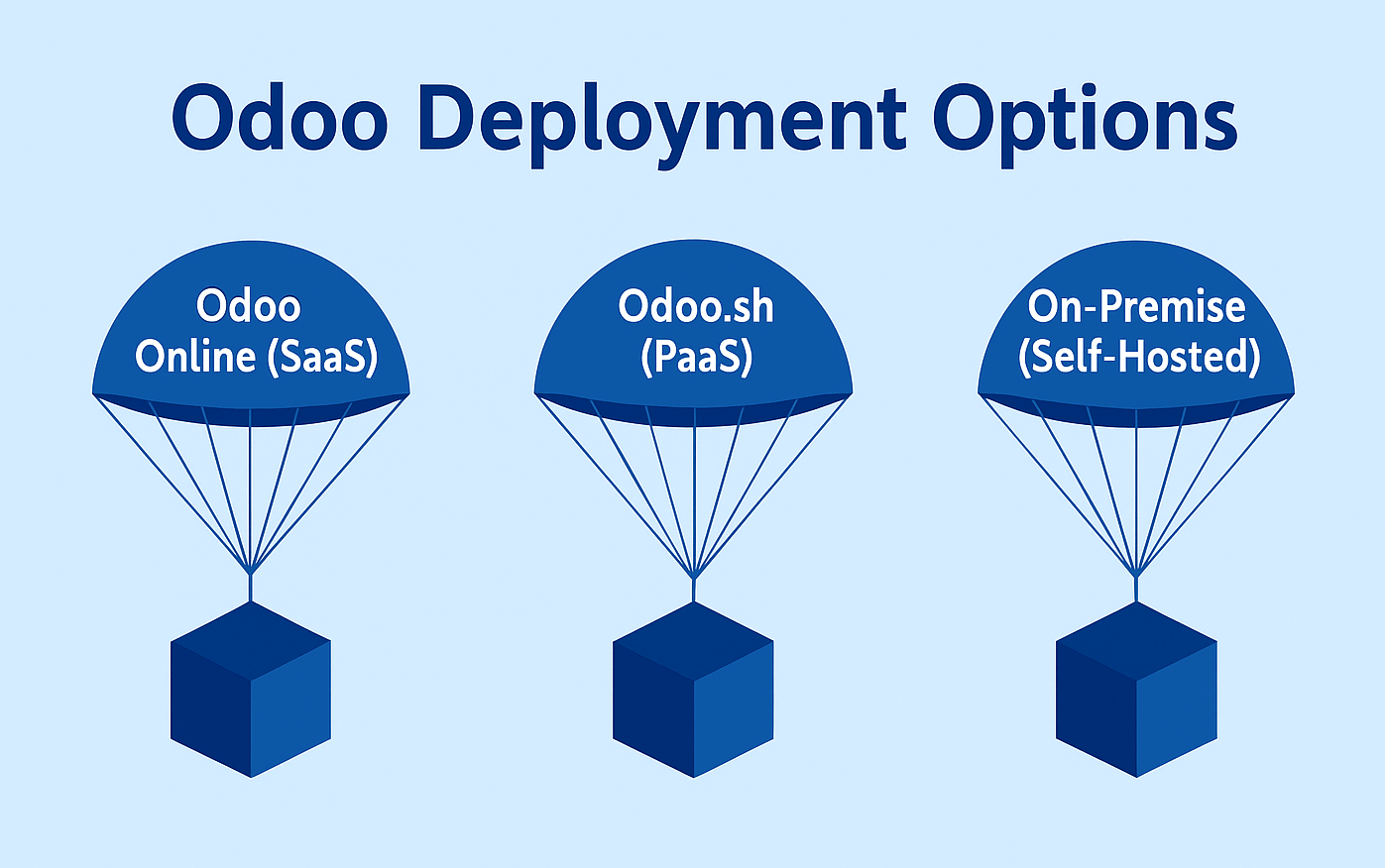
Odoo Deployment Options
1.
Odoo Online (SaaS):•
Managed by Odoo with automated updates and patches•
Limited customization•
Ideal for small businesses with standard requirements
2.
Odoo.sh (PaaS):•
Hosted by Odoo, more customizable•
Includes staging branches and CI/CD•
Good balance of flexibility and support
3.
On-Premise (Self-Hosted):•
Fully customizable and controlled•
Requires strong internal IT and security team•
Higher risk if security misconfigured
Odoo’s Strengths in Security
•
Role-Based Access Control (RBAC):Allows fine-grained permission settings based on user roles. This limits access to sensitive data and reduces the risk of privilege misuse.•
SSL/TLS Support:Supports encrypted communication between the client and server. This protects data from being intercepted during transmission.•
Database Segregation:Separates customer data across instances in multi-tenant environments. This helps maintain strong data isolation and reduces the impact of breaches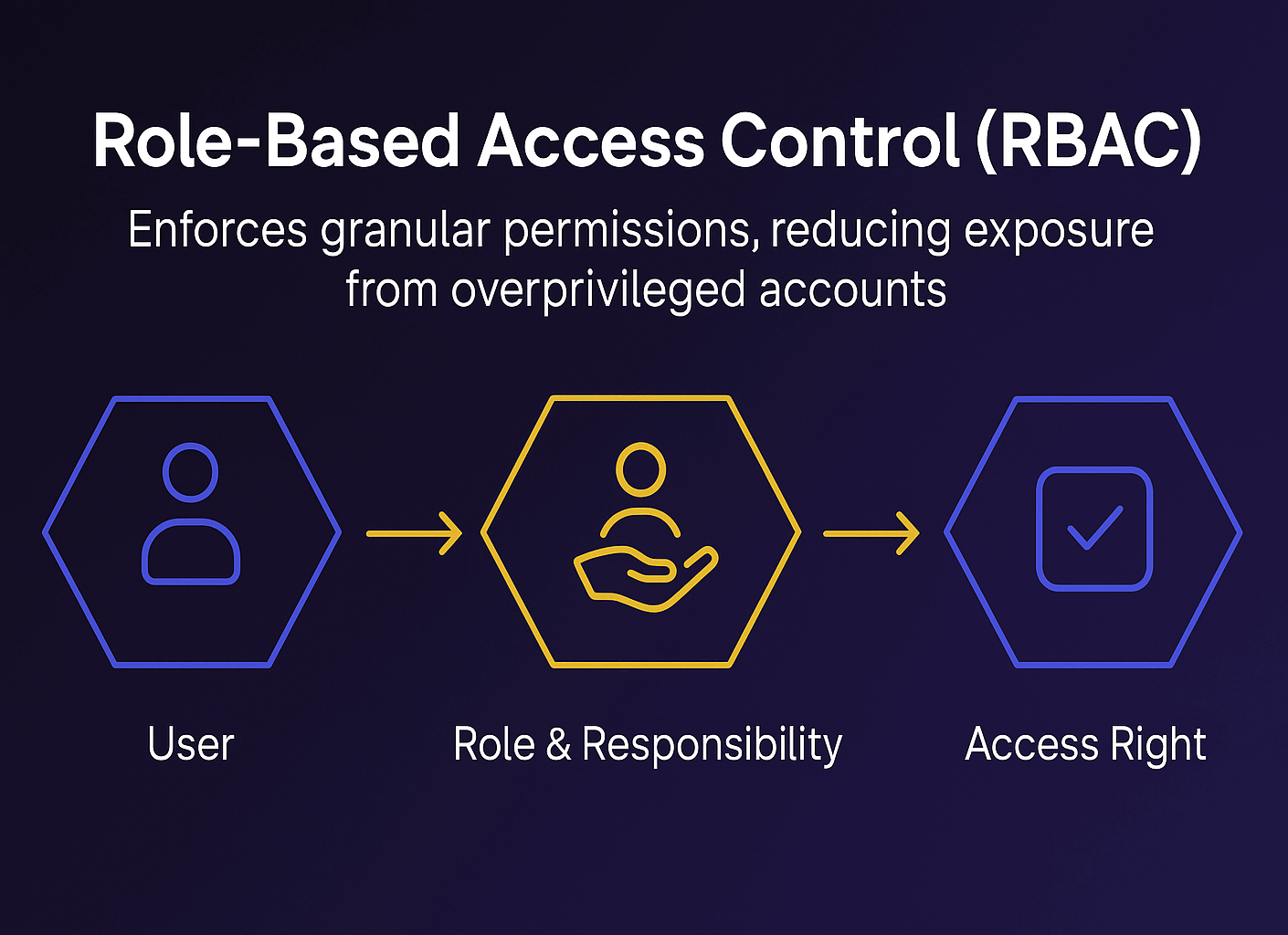
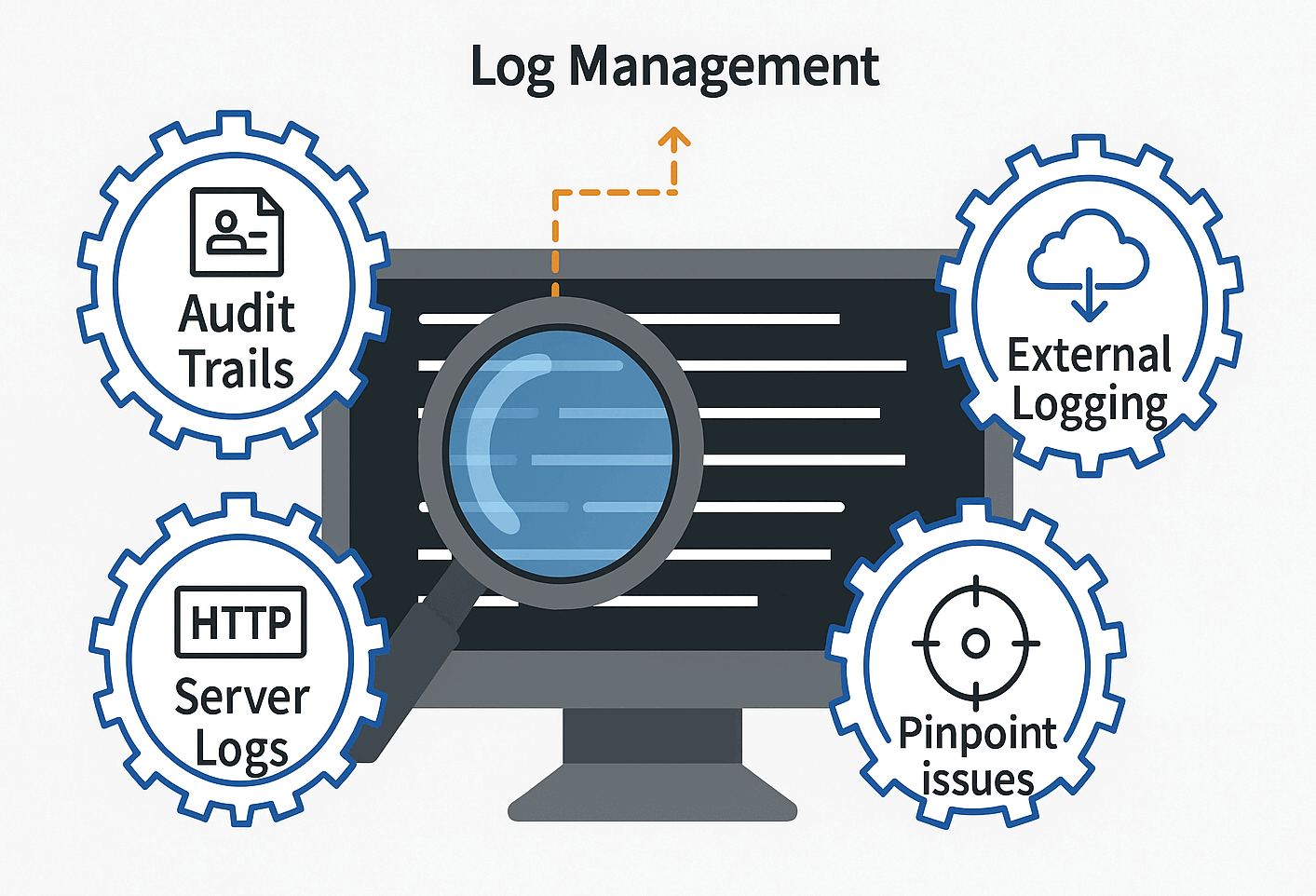
Log and Event Monitoring in Odoo
•
Audit Trails:Logs user actions on records such as create, update, and delete events. This helps trace changes and identify suspicious behavior.•
Server Logs:Records technical details like HTTP requests, login attempts, and system errors. Useful for debugging and spotting unusual access patterns.•
External Logging:Can be integrated with ELK stack or SIEM tools for centralized monitoring. This enables advanced analytics and real-time alerting.
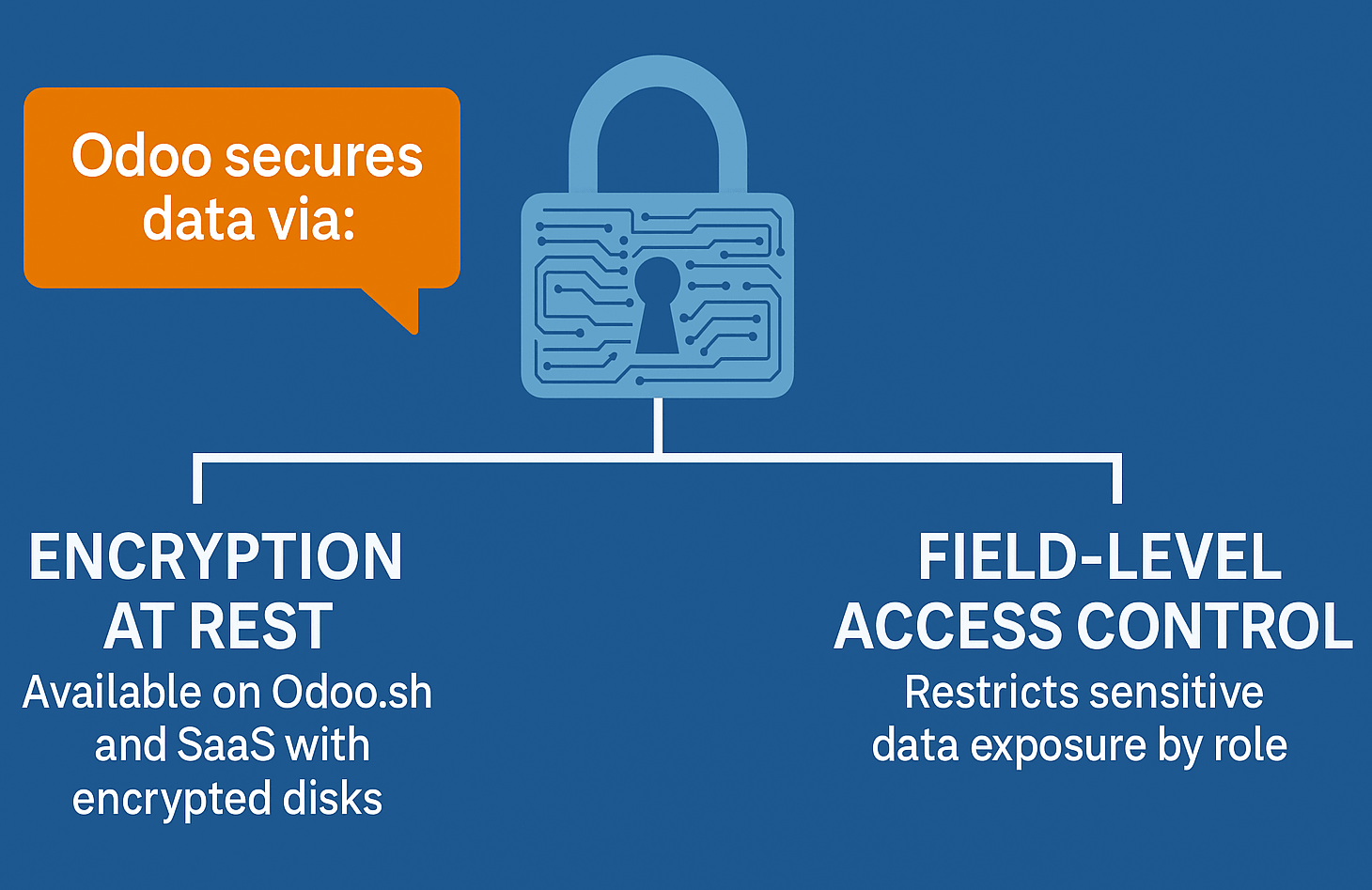
Database Security & Data Encryption
•
Encryption at rest: Available on Odoo.sh and SaaS with encrypted disks.•
Field-level access control: Restricts sensitive data exposure by role.•
GDPR-compliant data management tools: Eases right-to-erasure and consent tracking
These features help protect data integrity but don’t guard against exfiltration via compromised users or devices.
Session Authentication & Expiry Strategy
•
Token-Based Authentication:Users are authenticated through secure tokens that validate their identity with each request. This enables stateless and scalable session management.•
Configurable Session Timeouts:Sessions automatically expire after a set period of inactivity or a maximum duration. This reduces the risk of unauthorized access from abandoned sessions.•
Logout on Browser Close:Sessions can be configured to end when the browser is closed. This helps prevent session reuse on shared or public devices.
Odoo API Security
•
Key-Based Authentication:Access to the API requires an API key or user credentials, ensuring only authorized clients can interact with the system. These keys act as secure tokens to validate identity.•
Permission Checks on Method Calls:Each API method enforces user-level permissions, restricting access based on roles and access rights. This prevents unauthorized actions or data exposure.•
Limited Rate Limiting by Default:Odoo includes basic rate limiting to prevent abuse, though it may require custom configuration for stronger protection. This helps reduce the risk of brute-force or denial-of-service attacks
Lack of dynamic API usage profiling makes it vulnerable to token abuse or bot-driven attacks. CrossClassify enriches this with behavior-based API monitoring.
Common Vulnerability Protections in Odoo
•
SQL Injection:Odoo uses an Object-Relational Mapping (ORM) system and parameterized queries to prevent direct SQL injection attacks. This ensures that user input is not directly executed as SQL code.•
XSS Protection:The templating engine automatically escapes user-generated content. This helps prevent malicious scripts from being injected into web pages.•
CSRF Protection:Cross-Site Request Forgery protection is enabled by default on form submissions. It uses secure tokens to verify the legitimacy of user actions.
Compliance & Certifications
•
GDPR:Odoo includes built-in features to manage user consent, data access, and the right to be forgotten through its GDPR module. These tools help support compliance with European data protection laws.•
HIPAA / SOC 2 / ISO 27001:Odoo is not officially certified for HIPAA, SOC 2, or ISO 27001. Organizations must implement their own controls to meet these standards
MFA Alone Is Not Enough
•
Phishing-Resistant? Not Always:MFA can be bypassed through social engineering or phishing attacks. Users may still unknowingly share their codes with attackers.•
Adds Cognitive Load:MFA introduces extra steps that some users find inconvenient. As a result, they may reuse codes or disable MFA when given the option, weakening its effectiveness.
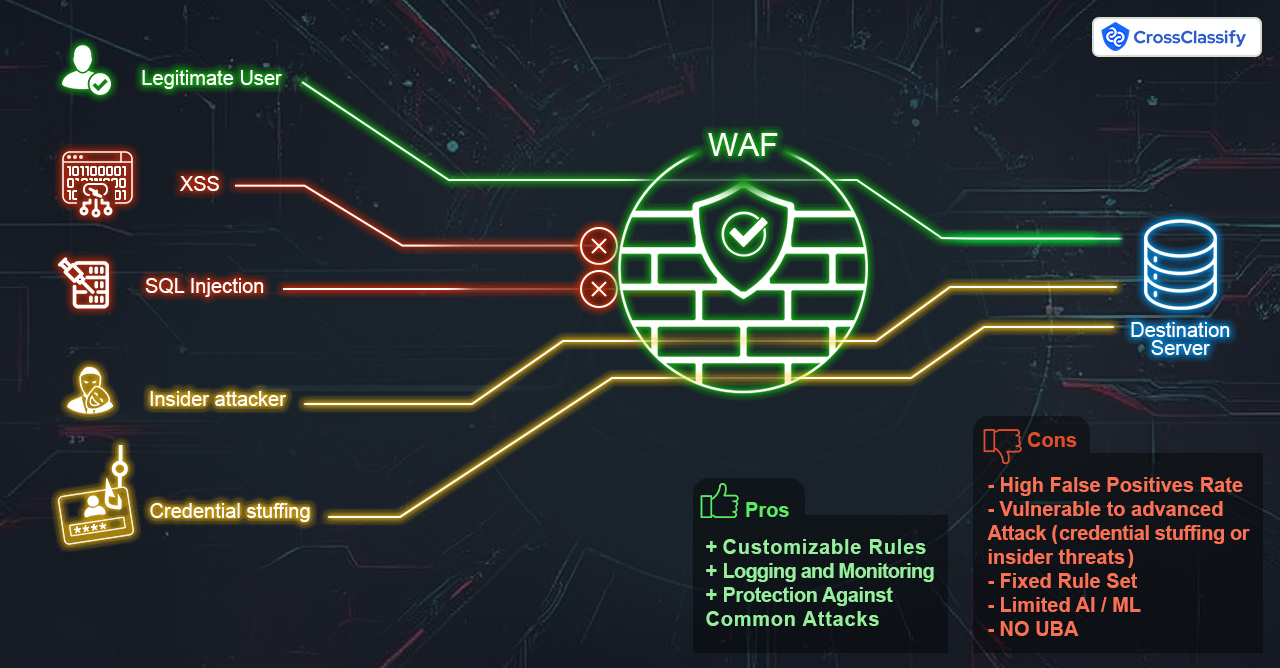
WAF & Reverse Proxy Limitations
•
- Pros:
- Prevent basic injection patterns
- Block known malicious IPs
•
- Cons:
- Blind to authenticated user behavior
- Can’t detect insider threats or credential stuffing
Odoo's Limitations Against Advanced Attacks
•
Credential Stuffing:Odoo accepts valid credentials without flagging repeated login attempts from different sources. There are no built-in alerts or protections against automated attacks using leaked credentials.•
Insider Threats:The platform does not monitor user behavior patterns. Without behavioral analysis, it cannot detect suspicious actions from legitimate users.•
Session Hijacking:Odoo does not score session risk or detect anomalies like sudden location changes. This makes it vulnerable to stolen session tokens or unauthorized session reuse.
Power of Device Intelligence
•
Identifies New, Untrusted Devices:Detects when a user logs in from a previously unseen or risky device. This helps flag potential account compromise early.•
Flags Device Spoofing and Emulator Usage:Recognizes attempts to mask real device identity or use emulators. These techniques are often linked to fraud or automated attacks.•
Links User Behavior to Verified Hardware Fingerprints:Associates actions with unique, persistent device signatures. This makes it harder for attackers to impersonate legitimate users.

Insider Threats Need Behavior Analytics
•
Insider Attacks Are a Major Risk:Around 22% of data breaches are caused by insider threats (IBM, 2023). These threats often go undetected because they involve valid credentials.•
UBA Detects Suspicious Behavior:User Behavior Analytics (UBA) monitors how users interact with the system. It helps identify intent and unusual activity patterns that static rules can't catch.•
CrossClassify Enhances Detection:CrossClassify analyzes factors like time-of-day access, irregular navigation, and behavioral anomalies. This enables early detection of potentially malicious insiders.

How CrossClassify Secures Odoo
•
User Behavior Analytics (UBA):Monitors user actions such as click patterns, navigation paths, and usage habits. Identifies abnormal behavior that may signal compromised or malicious users.•
Behavioral Biometrics:Analyzes subtle traits like typing rhythm and mouse movement. These human patterns help detect imposters even when credentials are valid.•
Device Intelligence:Fingerprints devices and monitors for session irregularities. Flags suspicious activity like device spoofing or access from unrecognized hardware.
Security Gaps CrossClassify Closes
| Security Gap | Native Odoo Coverage | CrossClassify Contribution |
|---|---|---|
| Credential Stuffing | ❌ | ✅ Behavior-based login risk detection |
| Insider Threats | ❌ | ✅ Anomaly detection via UBA |
| Session Hijack | ⚠️ Partial | ✅ Device-based session validation |
| Advanced Bot Attacks | ❌ | ✅ Behavioral fingerprinting and scoring |
| API Abuse | ⚠️ Rate limits only | ✅ Adaptive API behavior profiling |
| Compliance-Driven Anomaly Logging | ❌ | ✅ Audit-focused behavior and device reports |
| Frictionless MFA | ❌ | ✅ Smart, invisible MFA with device and context |
Why This Matters for the Odoo Community
•
Odoo is secure in principle — if configured well and patched regularly. But misconfigurations, user behavior, and real-time threat detection remain gaps.•
CrossClassify adds intelligent, behavioral fraud detection, which Odoo lacks natively.
As more sensitive workflows (e.g., financials, HR, CRM) move to Odoo, these adaptive, context-aware protections become critical.
Conclusions
Final Takeaway
Together, they create a defense-in-depth model for ERP environments — combining technical hardening with AI-driven fraud protection.
The future of Odoo security isn’t static—it’s smart, adaptive, and behavioral.
See How Protecting Customers from the Growing Threat of Account Takeover
Ensure Continuous Security with Real-Time Account Monitoring

See How Protect Your Platform from Account Opening Fraud
CrossClassify uses AI and continuous behavior monitoring to detect and prevent Fake accounts, protecting your business processes

Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Related articles
Frequently asked questions
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required



