Last Updated on 24 May 2025
Cybersecurity in Mining: Securing Digital Transformation with CrossClassify
Share in
Key Notes
•
68% of mining CEOs believe cybersecurity risks threaten growth — digital trust is vital.•
$4.45M is the average global cost of a data breach in 2023.•
75% of mining firms cite third-party access as a top cybersecurity concern.
Mining Industry: Complex, Critical, and Connected
•
Over 14,000 active mines operate globally across 100+ countries (World Mining Data, 2024).•
Mining collaborates with an average of 200 third-party contractors per site.•
Global mining tech spending is projected to exceed $20 billion by 2026.
Necessity of Digital Transformation
•
Traditional method: Manual Excel files lead to inconsistent data and untraceable changes.•
Modern requirement: Data must flow seamlessly into dashboards to guide operational and financial decisions.•
Outcome: Mines that fail to digitalize risk obsolescence as regulatory, environmental, and market demands grow.

The Hidden Hesitation in CEOs' Minds
•
Digital fear factor: CEOs fear exposing sensitive mine data to cyber threats.•
Trust gap: Unclear visibility into the security posture of modern digital systems prevents confident decision-making.•
CrossClassify’s role: Offers explainable AI decisions and real-time threat insights that build executive trust.

Cybersecurity Exposure in Mining: Deep and Wide
•
Multiple vectors: From site access to API calls, entry points are many.•
Human element: Operators, vendors, and field staff increase identity and access risk.•
Contractual spread: Numerous third parties mean varied security practices.
Recent Industry Stats
•
87% of mining companies report increased cybersecurity incidents since 2023.•
$5.1 million is the average breach cost for mining firms in 2024 (IBM Report).•
52% of attacks target user credentials and session hijacking (Cybersecurity Ventures, 2024).•
43% of post-login fraud goes undetected in mining ERPs.•
63% of mining IT leaders cite poor identity verification as a top concern (Gartner 2024).•
29% of breaches come from third-party exposure.•
92% of mines are now connected via public or hybrid cloud infrastructure (McKinsey Mining Digital Transformation Report).•
81% of surveyed mining execs demand more advanced fraud analytics.

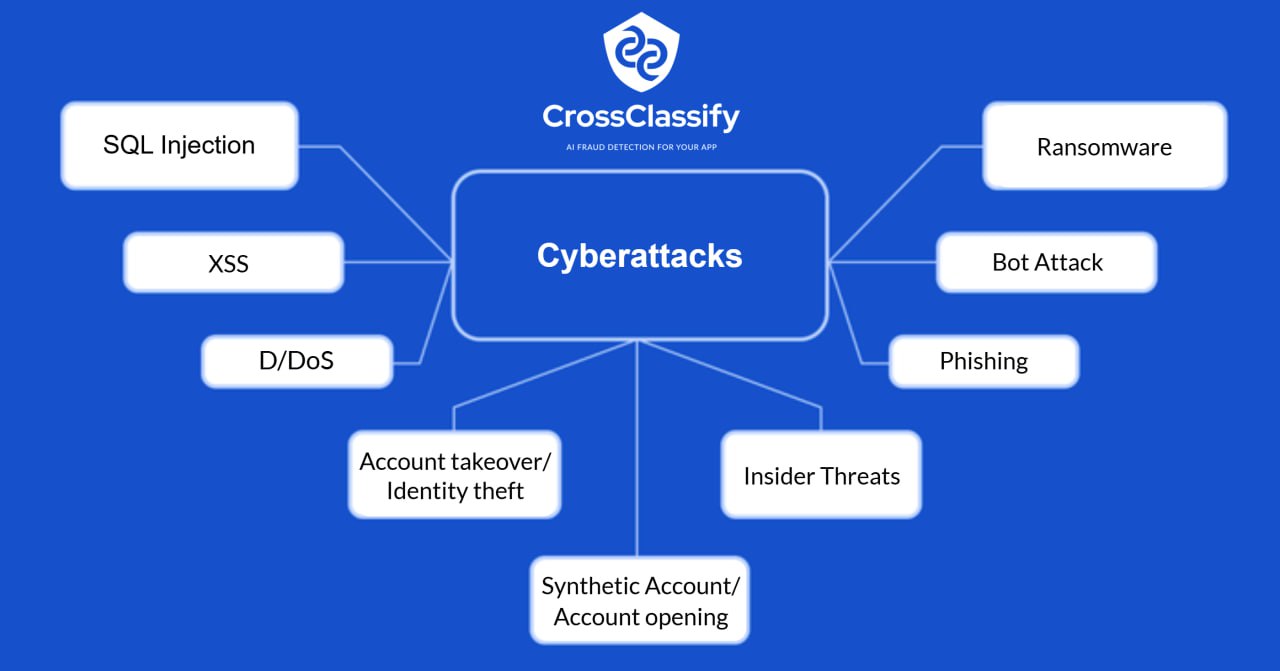
Varied Cyber Threats in Mining
•
Account Takeover: Attackers hijack user sessions to alter records, siphon resources, or gain persistent access. (ATO article)•
Bot and Abuse Fraud: Bots can spam portals, exploit APIs, and overload logistics systems.•
Fake Account Creation: Contractors or external parties may register unauthorized accounts for manipulation.•
Insider Threats: Disgruntled or compromised insiders are harder to detect with traditional methods.
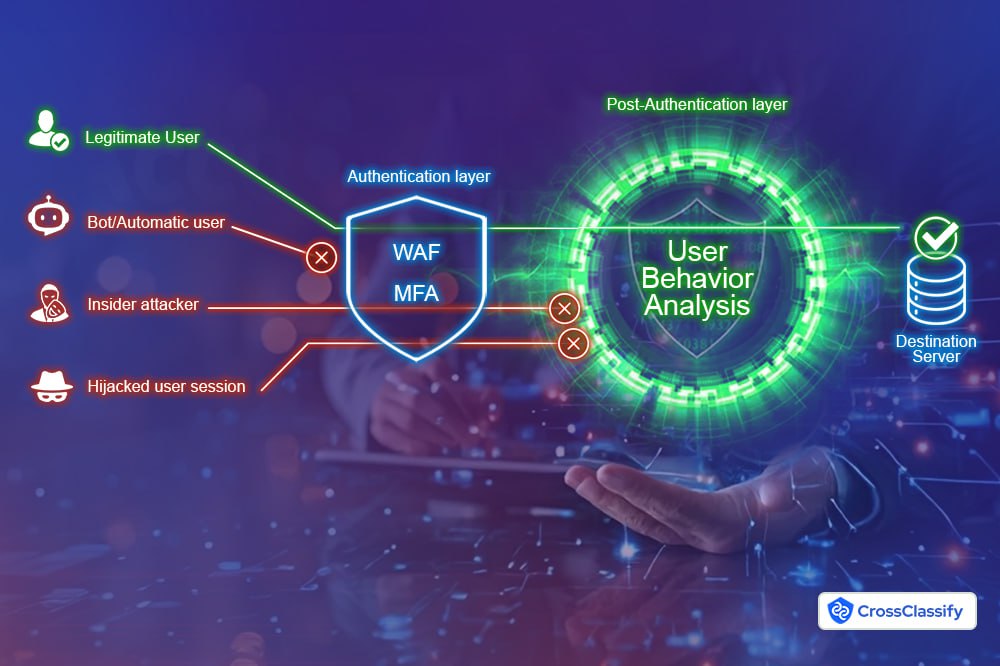
Beyond WAF and MFA: Why Legacy Protections Are Not Enough
•
Limitations of WAF:Cannot analyze post-login behavior or detect insider misuse.•
MFA loopholes:MFA fatigue and session persistence can be exploited.•
CrossClassify Advantage:Our AI layer catches sophisticated threats by analyzing patterns, devices, and behaviors post-authentication.
The Insider Threat: Detecting the Invisible
•
Varied insiders: From equipment operators to backend admins.•
Behavioral deviation tracking: CrossClassify uses session rhythm, navigation flow, and input dynamics.•
Real-world impact: Prevent data leaks, sabotage, or unauthorized downloads.
Need for Continuous Monitoring and Adaptive Risk Assessment
•
Dynamic user roles: Users shift roles throughout shifts and tasks.•
AI advantage: CrossClassify adapts its models in real time using behavioral context.•
Zero-latency protection: Mining operations can’t afford delayed alerts or periodic scans.

Securing Mining Databases and Encrypting Data Pipelines
•
Data Encryption: AES-256 encryption for all data pipelines.•
Integrity checks: Automatic hashing and comparison to prevent tampering.•
Database activity monitoring: Identify abnormal query patterns.
API Security: The Lifeline of Third-Party Integration
•
Rate limiting: Prevent API overload and DoS.•
Access controls: Ensure only validated third parties access specific endpoints.•
CrossClassify role: Detects anomalies in API usage patterns and enforces adaptive throttling.
Device Intelligence: Mining’s Silent Security Partner
•
Device fingerprinting: Unique ID based on hardware and software.•
Session correlation: Links user actions across devices.•
Anomaly detection: Flags unknown or tampered devices.
Compliance and Certification Landscape for Mining
•
Data sovereignty: Mines in multiple countries must handle user data per local laws.•
Investor expectations: Compliance is tied to ESG and governance ratings.•
CrossClassify support: Helps align security posture with major standards.
Insider Attacks: Only User Behavior Analytics Can Stop Them
How Behavioral Biometrics Detects Sophisticated Threats
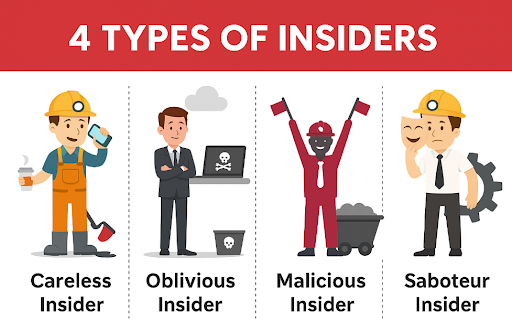
The 4 Types of Insider Threats in Mining
1.
Malicious Insiders – Employees who intentionally abuse access for sabotage or personal gain.
Example: Leaking geological data to competitors or manipulating production schedules.2.
Negligent Insiders – Well-meaning staff who accidentally expose data due to poor cybersecurity hygiene.
Example: A mine supervisor using a weak password shared across systems.3.
Compromised Insiders – Users whose credentials are hijacked by external attackers.
Example: A contractor’s VPN credentials get phished and used to access financial records.4.
Third-party Insiders – Vendors or service providers with inside access but minimal oversight.
Example: A maintenance firm with remote system access introduces malware unknowingly.
How CrossClassify Defends Against Them
| Insider Type | Detection via Behavioral Biometrics |
|---|---|
| Malicious | Deviations from baseline behavior trigger alerts |
| Negligent | Unusual navigation or speed indicates risk |
| Compromised | Login behavior differs from usual patterns |
| Third-party | Continuous monitoring prevents lateral movement |
Conclusion: Digging Deep, Securing Wide
See How Protecting Customers from the Growing Threat of Account Takeover
Ensure Continuous Security with Real-Time Account Monitoring

Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Related articles
Frequently asked questions
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required