Last Updated on 19 Aug 2025
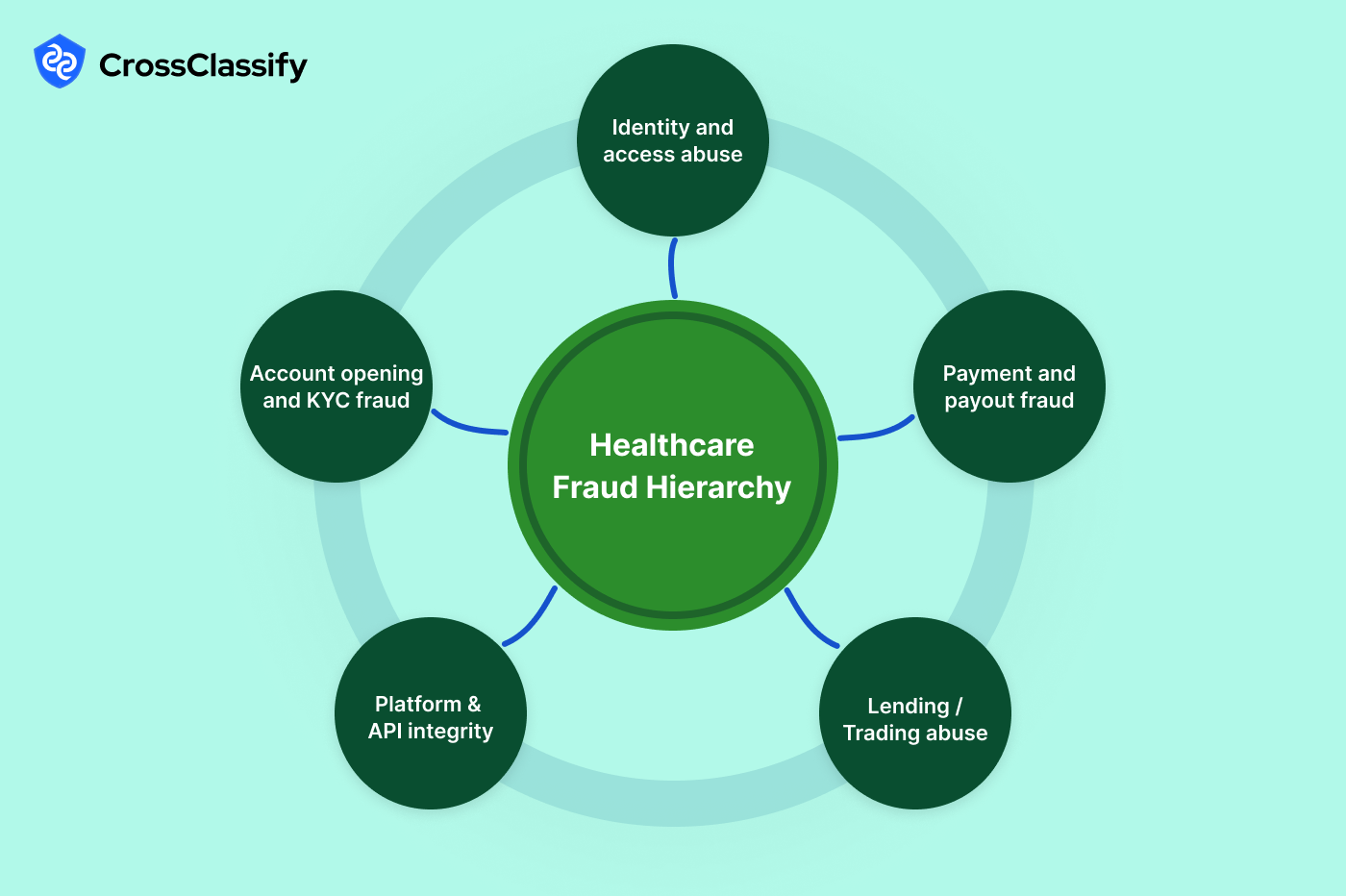
Healthcare Fraud Hierarchy: A Practical Guide For CISOs, CIOs, and Compliance Leaders
Share in
Introduction
Healthcare organizations operate at the intersection of clinical urgency, sensitive personal data, and complex payments. That mix attracts organized fraud and opportunistic abuse that target portals, telehealth endpoints, billing systems, and pharmacy flows. Below is a full hierarchy of how fraud and cybersecurity threats typically manifest in the healthcare ecosystem and where the most actionable signals can be found. For each concern, we break it into practical sub types, describe the patterns used by attackers, then list high value signals and the most convincing evidence you can present to business and audit stakeholders. Throughout, you will see how an AI powered healthcare fraud detection platform like CrossClassify operationalizes the controls needed to stop loss without harming clinical throughput.
Identity and Access Abuse in Patient and Provider Portals
Identity threat actors target patient and provider portals because these surfaces unlock PHI, prescription privileges, and payout controls. Account takeover can be launched with credential stuffing or social engineering of help desks, while shared identity abuse spreads one login across many users in a clinic or revenue cycle center. The goal is usually PHI theft, prescription fraud, or profile changes that enable payout diversion. History shows this risk is material. The Anthem breach exposed tens of millions of records and demonstrated how portal credentials and insurance identifiers can be monetized long after the intrusion.
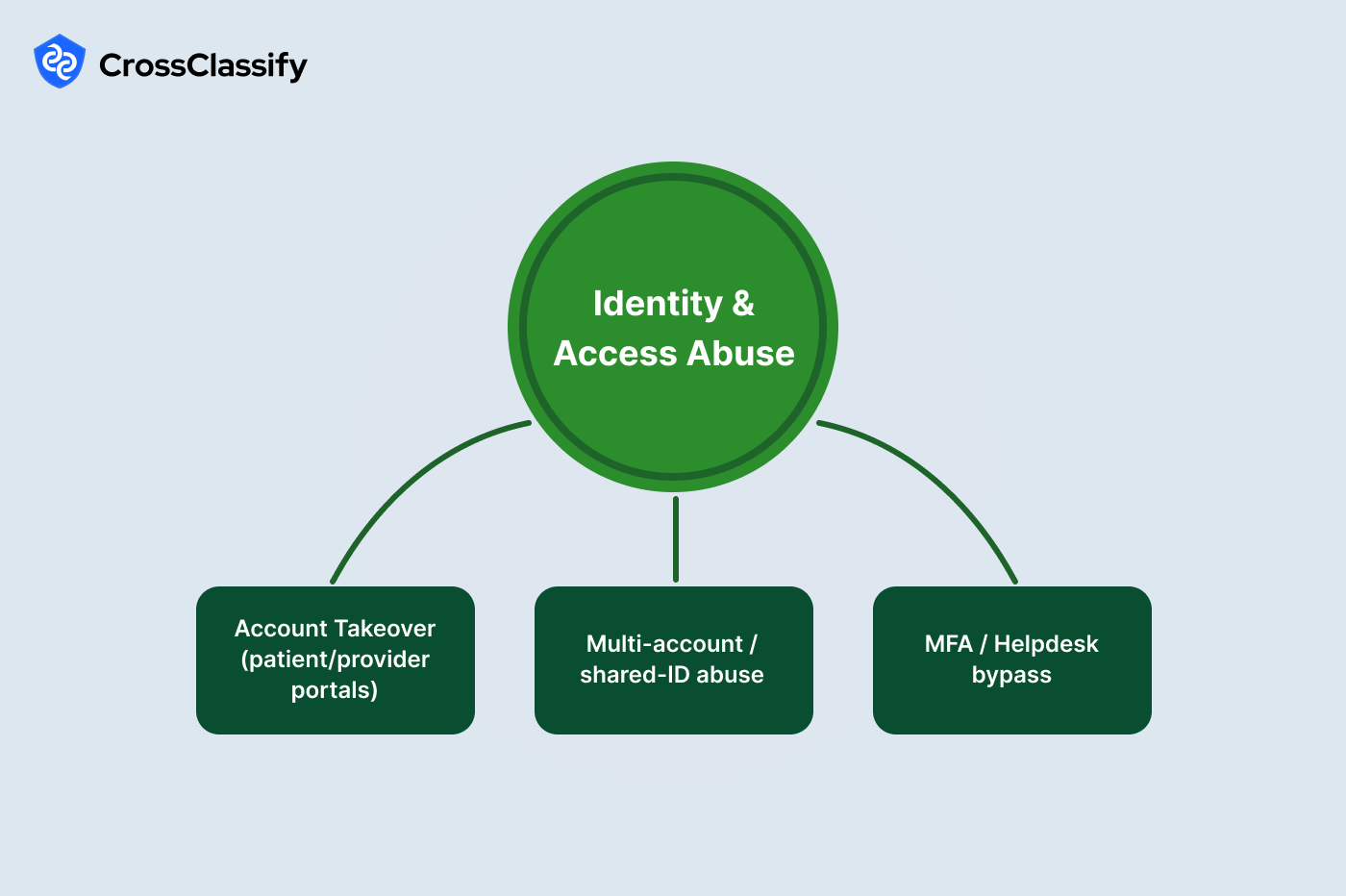

1. Account Takeover of patient and provider portals
- New logins from unfamiliar regions just before record downloads or prescription refills: attackers often stage access from distant cloud regions or unexpected countries minutes before exporting records or submitting refills. Evidence: a region by hour heat map shows clean clusters in expected cells for normal users and bright time boxed hotspots near the refill or export window for compromised accounts.
- Spike of failed logins followed by a successful one: credential stuffing causes bursts of failures that suddenly flip to success as one password hits. Evidence: a paired time series of failed and successful attempts makes the conversion obvious, especially when the success immediately precedes a sensitive action.
2. Multi account and shared ID abuse
- Many accounts tied to the same device or IP accessing different patients: shared desktops and intentionally pooled credentials create coordination hubs. Evidence: a devices to accounts network reveals hub and spoke structures that cannot be explained by shift work alone.
- Reused device fingerprints across distinct clinician NPI numbers: synthetic team structures rotate NPIs behind one workstation to mask behavior. Evidence: a fingerprint reuse table lists device identifiers that appear under several NPIs across days.
3. MFA and helpdesk bypass
- Contact change followed by password reset within ten minutes: social engineering often starts with a phone or email change, then a reset. Evidence: two hourly trend lines for profile changes and resets display synchronized peaks only when bypass playbooks succeed.
- Support tickets immediately preceding credential changes: when an attacker has a case number, resets happen quickly. Evidence: a ticket proximity table shows minute level gaps between tickets and credential change events.
Claims and Billing Fraud
Fraudulent billing ranges from aggressive upcoding to fully fabricated encounters. These patterns are amplified by automated submission tools and outsourced billing vendors who may be careless with security. Beyond revenue leakage, improper payments invite regulatory fines. Real world enforcement actions around unbundling and upcoding show that data driven audit signals catch abuse earlier than manual review.
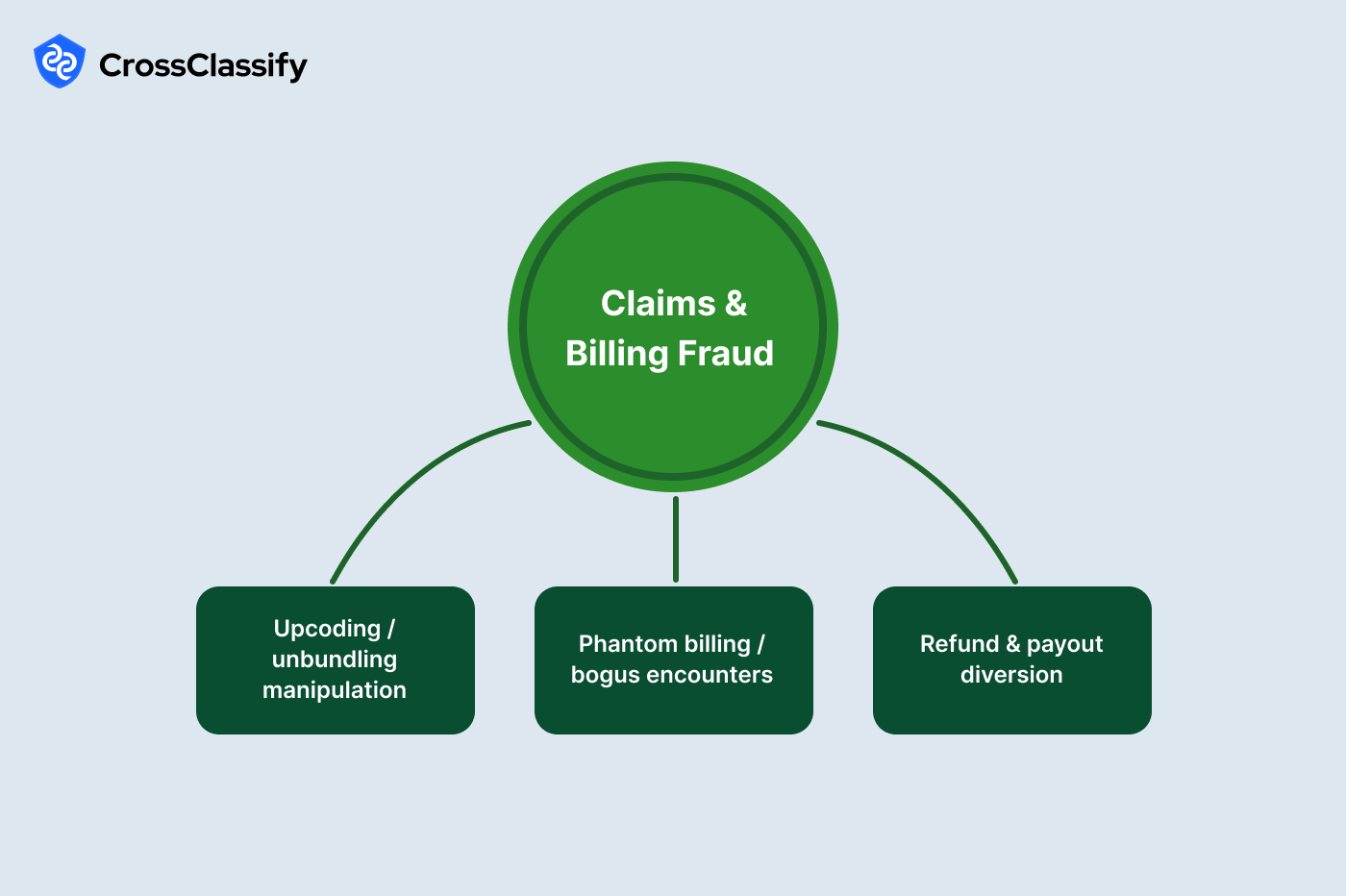

1. Upcoding and unbundling manipulation
- CPT level distribution drifts higher than peer mix: bad actors push level four and five far beyond specialty norms. Evidence: a bar dashboard by CPT level compares each site to peers and exposes uplift in the upper codes.
- Incompatible code pairs billed together: certain code combinations should not co appear. Evidence: an incompatible pair frequency table lists pairs and counts by provider, making concentration easy to see.
2. Phantom billing and bogus encounters
- Claims submitted outside facility geofence: services that supposedly occurred on site show off site coordinates. Evidence: a geofence table with Yes or No flags highlights fabricated encounters.
- Burst of claim submissions within a single minute: robotic upload activity generates claim storms. Evidence: a per minute bar chart displays the spikes clearly without deep analytics.
3. Refund and payout diversion
- Beneficiary bank change followed by a large payout within twenty four hours: this is the classic diversion play. Evidence: paired lines for bank changes and payouts show tight coupling only during abuse windows.
- Same bank account used by multiple providers: rings launder refunds to one target account. Evidence: a provider to bank network reveals multi provider hubs that require immediate review.
Prescription and Pharmacy Abuse
Prescriptions create high value privileges that can be monetized quickly. Rings pursue doctor shopping and forged scripts while automation targets refill endpoints at scale. The opioid crisis illustrated how identity sharing and recycled paperwork lead to dangerous diversion. Telemedicine growth increased the attack surface through purely digital flows.
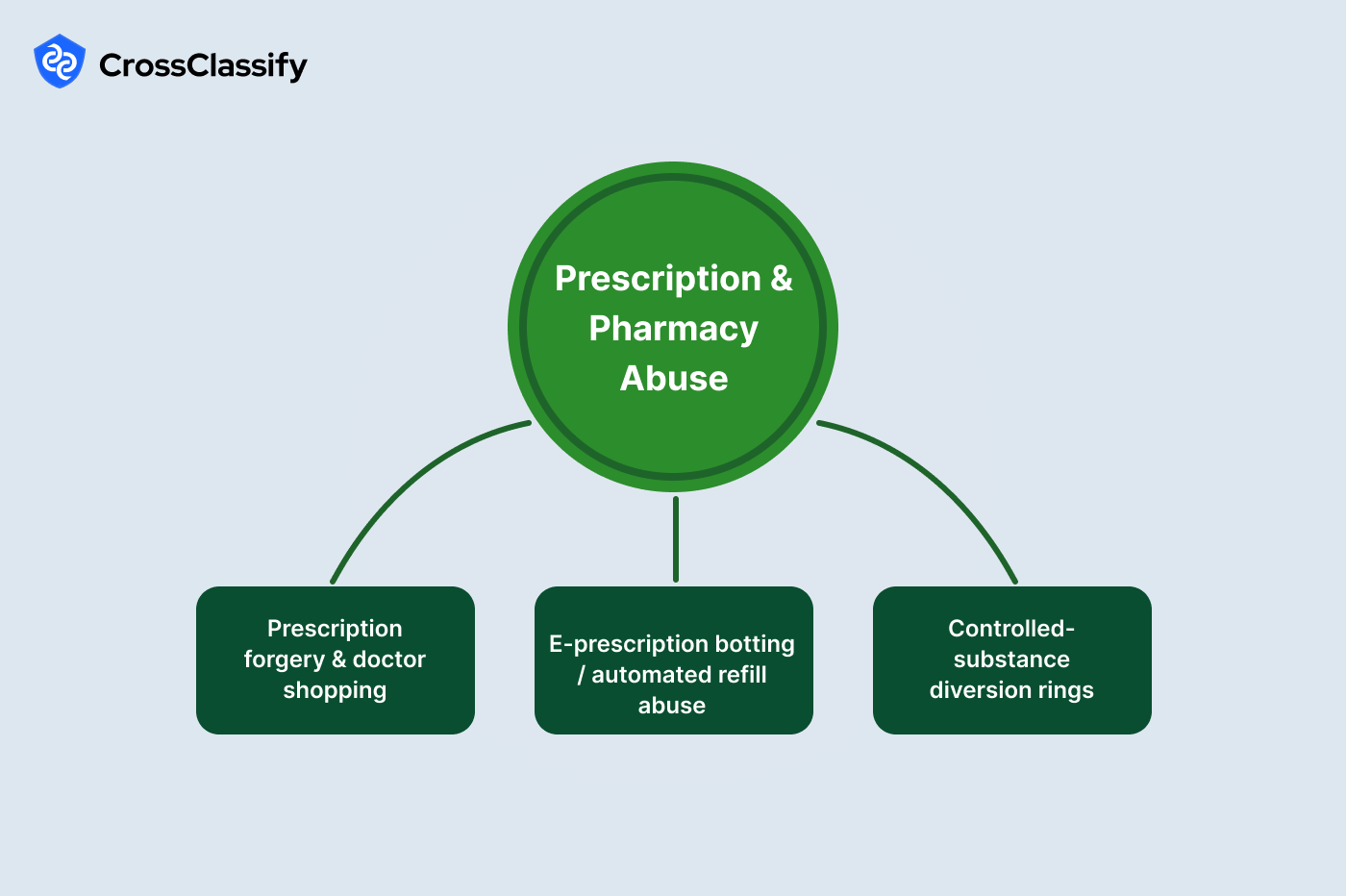

1. Prescription forgery and doctor shopping
- Many prescribers for the same patient in thirty days: genuine patients rarely change prescribers that fast, especially for controlled drugs. Evidence: a bar chart of prescribers per patient surfaces outliers by cohort.
- Prescription document hash reuse across patients: forged PDFs are recycled across identities. Evidence: a hash reuse table that shows the same file fingerprint appearing in multiple patient records.
2. E prescription botting and automated refill abuse
- Excessive requests from headless or scripted user agents to the refill endpoint: scraping and automation tools leave distinct user agent signatures. Evidence: a user agent bar chart that compares human browsers with headless or scripted agents.
- Sessions with zero depth before a refill request: bots hit the endpoint without browsing. Evidence: a sessions by depth bar proves the absence of normal navigation behavior.
3. Controlled substance diversion rings
- Multiple patients connected to the same pickup person or address: proxy pickup patterns reveal organized diversion. Evidence: a patients to pickup address network that exposes address hubs.
- Repeated co fill patterns across pharmacy pairs: colluding pharmacies rotate fills for the same group. Evidence: a co fill heat map where hot cells indicate repeated pair activity.
Marketplace and Content Integrity
Directory accuracy and telehealth quality drive patient trust. Attackers create fake provider profiles, stuff reviews, or scrape provider data at scale. Session manipulation in telehealth can also be used to collect fees without delivering care. Public cases of fake clinics and paid review farms show how these schemes harm both patients and brands.

1. Fake provider profiles and credential forgery
- Review bursts from newly created accounts on the same day: feedback stuffing inflates visibility quickly. Evidence: a cohort based review line showing a sudden step up by new cohorts.
- IP clusters posting across multiple provider profiles: coordination hubs push many profiles. Evidence: an IP to profile network where a single IP is tied to numerous review events.
2. Telehealth session manipulation
- Identical, very short session durations with minimal input activity: scripted sessions are nearly the same length and lack clicks or typing. Evidence: a session duration histogram with a tall narrow spike at a short duration.
- Cancellations clustering within five minutes of start: policy gaming avoids charges while collecting scheduling incentives. Evidence: a cancellation timing series that spikes immediately after start time.
3. Directory scraping and lead harvesting
- Excessive search requests from uncommon agents: headless browsers and libraries stand out. Evidence: a user agent request bar chart segmented by class of agent.
- High search to booking ratios from specific IP ranges: reconnaissance ranges search heavily but rarely convert. Evidence: an IP range ratio table that flags conversion outliers.
Compliance and Clinical Data Integrity
Regulators expect verifiable trails for every access, change, and clinical step. Attackers try to tamper with audit logs and provenance data or submit expired insurance and authorization documents. Change Healthcare ransomware events and other sector incidents showed how operational paralysis and financial fraud often travel together. Preventing tampering is as important as detecting external intrusion.

1. EMR audit log tampering
- Identical edit timestamps across users: batch edits outside the software flow create unnatural alignment. Evidence: a user by hour heat map where synchronized columns indicate manipulation.
- Missing audit log volume during certain hours: silent hours suggest disabled logging. Evidence: a missing log indicator line that rises above zero for precise time windows.
2. Lab result and provenance integrity
- Chain of custody timestamps out of order by process step: out of order steps imply backfilled data. Evidence: a violations bar chart per step within the chain.
- Unusual path anomalies in the provenance graph: shortcuts connect incompatible steps. Evidence: a lots to process network that exposes over connected nodes.
3. Insurance and document fraud
- Expired authorizations or COI used on active claims: stale coverage is frequently reused. Evidence: a days to expiry table where negative values identify violations.
- PDF fingerprint reuse across providers: recycled forms spread across many submitters. Evidence: a document hash reuse table with counts per provider.
How CrossClassify Maps To This Healthcare Hierarchy
Unified risk engine across the hierarchy. CrossClassify anchors the entire hierarchy with a single risk service that ingests identity, device, session behavior, EMR and pharmacy events, payments, and even IoT and location signals from kiosks or dispensing cabinets. The platform reconciles these streams to one entity graph of patients, clinicians, devices, banks, addresses, documents, and API clients. That graph is scored continuously so the risk for an account or session is not a one time check at login but a live value that changes as the workflow progresses. This approach lets security teams place the AI powered healthcare fraud detection platform directly in front of clinical and back office decisions such as portal downloads, e-prescribe submits, claim submissions, and treasury payouts. The result is targeted controls that protect PHI and revenue while keeping genuine clinicians and patients fast.
Device fingerprinting for patient portals and clinical endpoints. CrossClassify creates a privacy-preserving, persistent device identifier that survives private browsing, cookie clears, and most VPN usage. Each sensitive action in the hierarchy is bound to this fingerprint, including profile edits, prescription actions, bank detail changes, and EMR export attempts. When the same workstation appears behind many patient or provider accounts, the platform surfaces a coordination hub that maps to "multi-account or shared-ID abuse." If a device that normally operates inside the hospital's ASN suddenly appears from an unfamiliar cloud region minutes before a refill or record export, the risk engine raises the score and can require step-up verification. This device fingerprinting for patient portals also links to treasury systems so beneficiary edits and payout requests can be evaluated in context of the originating hardware and historical behavior.
Behavioral biometrics for healthcare staff and patients. The platform learns keystroke cadence, field-to-field dwell and flight times, mouse movements, and navigation paths that are characteristic of clinicians, help desk agents, revenue cycle staff, and patients. These features are collected with lightweight JavaScript and SDKs that do not capture content and are processed to templates that protect privacy. When an attacker socially engineers a help desk and gains a password, the keystroke timing and navigational rhythm often diverge from the enrolled template, which exposes "MFA and helpdesk bypass" as well as account sharing. The same applies to scripted telehealth or refill bots that show zero page depth and robotic timing. By combining these signals with device and identity, behavioral biometrics for healthcare lifts precision and keeps friction near zero for trusted users.
Real time risk scoring for healthcare decisions. Scoring is not a nightly batch. The engine recomputes risk during the exact step where harm can occur. It fuses portal geovelocity, AVS and CVV mismatch patterns, document hash reuse, beneficiary reuse across providers, API parameter anomalies, geofence mismatches, and audit log irregularities. Policies then attach precise actions to risk thresholds, such as step-up MFA during a refill session, a cool-off timer after a contact change, quarantine for a burst of claims, or a payout pause after a bank change that is tightly coupled to a large disbursement. This real time risk scoring for healthcare maps one to one to the hierarchy's control points and supplies investigators with evidence objects like heat maps, line graphs, tables, and networks that can be exported to case systems.
Mapping to each hierarchy pillar.
Operational fit for security, compliance, and clinical operations. CrossClassify is deployed as an SDK and API so teams can place checks at login, at prescription submit, at claim creation, at bank change, and at payout time. Risk decisions return in milliseconds and include a recommended action plus the visual evidence to back it up in hearings or audits. Privacy is preserved through hashing, tokenization, and configurable retention that aligns with HIPAA and organizational policy. Because the platform unifies identity, device, behavior, and payments, healthcare leaders replace many point tools with one AI powered healthcare fraud detection platform that continuously improves with feedback from investigations.
Explore the healthcare solution page for capabilities and integrations.
Read the in-depth article with examples and controls.
Device fingerprinting for patient portals and clinical endpoints. CrossClassify creates a privacy-preserving, persistent device identifier that survives private browsing, cookie clears, and most VPN usage. Each sensitive action in the hierarchy is bound to this fingerprint, including profile edits, prescription actions, bank detail changes, and EMR export attempts. When the same workstation appears behind many patient or provider accounts, the platform surfaces a coordination hub that maps to "multi-account or shared-ID abuse." If a device that normally operates inside the hospital's ASN suddenly appears from an unfamiliar cloud region minutes before a refill or record export, the risk engine raises the score and can require step-up verification. This device fingerprinting for patient portals also links to treasury systems so beneficiary edits and payout requests can be evaluated in context of the originating hardware and historical behavior.
Behavioral biometrics for healthcare staff and patients. The platform learns keystroke cadence, field-to-field dwell and flight times, mouse movements, and navigation paths that are characteristic of clinicians, help desk agents, revenue cycle staff, and patients. These features are collected with lightweight JavaScript and SDKs that do not capture content and are processed to templates that protect privacy. When an attacker socially engineers a help desk and gains a password, the keystroke timing and navigational rhythm often diverge from the enrolled template, which exposes "MFA and helpdesk bypass" as well as account sharing. The same applies to scripted telehealth or refill bots that show zero page depth and robotic timing. By combining these signals with device and identity, behavioral biometrics for healthcare lifts precision and keeps friction near zero for trusted users.
Real time risk scoring for healthcare decisions. Scoring is not a nightly batch. The engine recomputes risk during the exact step where harm can occur. It fuses portal geovelocity, AVS and CVV mismatch patterns, document hash reuse, beneficiary reuse across providers, API parameter anomalies, geofence mismatches, and audit log irregularities. Policies then attach precise actions to risk thresholds, such as step-up MFA during a refill session, a cool-off timer after a contact change, quarantine for a burst of claims, or a payout pause after a bank change that is tightly coupled to a large disbursement. This real time risk scoring for healthcare maps one to one to the hierarchy's control points and supplies investigators with evidence objects like heat maps, line graphs, tables, and networks that can be exported to case systems.
Mapping to each hierarchy pillar.
- Identity and access abuse: device hubs, geovelocity spikes, failed-then-success sequences, and contact-change-to-reset coupling are modeled as chained signals that automatically trigger session-level friction.
- Claims and billing fraud: CPT distribution drift, incompatible pairs, minute-level submission bursts, and facility geofence violations are aggregated per provider and per billing group to prioritize audits.
- Prescription and pharmacy abuse: doctor-shopping, hash-reused scripts, refill bot traffic, and address hubs are detected with cohort features, document fingerprints, user-agent analytics, and network link analysis.
- Marketplace and content integrity: fake profile creation, review stuffing, and telehealth manipulation are scored with account age, IP-to-profile graphs, and session-duration histograms.
- Compliance and clinical data integrity: audit-log synchronization, missing log bands, out-of-order chain-of-custody steps, and PDF hash reuse feed automated attestations and regulator-ready reports.
Operational fit for security, compliance, and clinical operations. CrossClassify is deployed as an SDK and API so teams can place checks at login, at prescription submit, at claim creation, at bank change, and at payout time. Risk decisions return in milliseconds and include a recommended action plus the visual evidence to back it up in hearings or audits. Privacy is preserved through hashing, tokenization, and configurable retention that aligns with HIPAA and organizational policy. Because the platform unifies identity, device, behavior, and payments, healthcare leaders replace many point tools with one AI powered healthcare fraud detection platform that continuously improves with feedback from investigations.
Explore the healthcare solution page for capabilities and integrations.
Read the in-depth article with examples and controls.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Most takeovers follow a repeatable pre action sequence, including unfamiliar regions and failed to success bursts. CrossClassify watches identity, device, and behavior together to score risk in the moment and challenges only the suspicious session. Learn how these signals work together in healthcare cybersecurity and fraud.
See how staged ATOs slip past static MFA and how to break the kill chain in the anatomy of account takeover. For a blueprint on continuous, step-up-only-when-needed controls, review the CARTA model overview at continuous adaptive risk and trust assessment.
See how staged ATOs slip past static MFA and how to break the kill chain in the anatomy of account takeover. For a blueprint on continuous, step-up-only-when-needed controls, review the CARTA model overview at continuous adaptive risk and trust assessment.
Shared IDs create device hubs that connect many accounts. CrossClassify uses device fingerprinting for patient portals and provider workstations to expose hubs in network views and to throttle risky nodes immediately. Details and examples appear in healthcare cybersecurity and fraud.
A practical primer on persistent device identity is at device fingerprinting and a deeper technical explainer on how fingerprinting works is at how does fingerprinting work.
A practical primer on persistent device identity is at device fingerprinting and a deeper technical explainer on how fingerprinting works is at how does fingerprinting work.
Yes, the risky pattern is a contact change quickly followed by a reset. CrossClassify correlates support ticket proximity with credential events and can apply cool off timers or step up MFA when the coupling appears. See the approach in healthcare cybersecurity and fraud.
Why attackers bypass MFA and how layered analytics closes the gap is covered in uncover the threats WAF and MFA miss and the ATO playbook itself is broken down at the anatomy of account takeover.
Why attackers bypass MFA and how layered analytics closes the gap is covered in uncover the threats WAF and MFA miss and the ATO playbook itself is broken down at the anatomy of account takeover.
Distribution drift at CPT level is the first filter. CrossClassify's healthcare claims fraud analytics ranks providers by deviation from peer mix and links each spike to supporting encounters for targeted audit. Methodology is outlined in healthcare cybersecurity and fraud.
Context on system level risks and why proactive analytics matter for clinical operations is discussed in cybersecurity threats in healthcare and in the shift to digital records at paper-free medicine transforming care.
Context on system level risks and why proactive analytics matter for clinical operations is discussed in cybersecurity threats in healthcare and in the shift to digital records at paper-free medicine transforming care.
Geofence mismatches and submission bursts are highly predictive. CrossClassify blends geospatial checks with per minute volume analytics and can quarantine claim batches when the pattern hits. Learn more at healthcare cybersecurity and fraud.
Why delayed detection raises patient risk and operational impact is outlined in when patient data breaches turn deadly and broader sector exposure is summarized in cybersecurity threats in healthcare.
Why delayed detection raises patient risk and operational impact is outlined in when patient data breaches turn deadly and broader sector exposure is summarized in cybersecurity threats in healthcare.
Diversion usually follows a bank change that is tightly coupled to a large payout. CrossClassify's real time risk scoring for healthcare pauses payouts when coupling is detected and surfaces provider to bank networks that reveal hubs. Framework described in healthcare cybersecurity and fraud.
See how device based binding reduces false positives on payment edits in device fingerprinting and how continuous risk helps time holds precisely in continuous adaptive risk and trust assessment.
See how device based binding reduces false positives on payment edits in device fingerprinting and how continuous risk helps time holds precisely in continuous adaptive risk and trust assessment.
Bots leave user agent fingerprints and do not browse provider pages. CrossClassify scores session integrity and sets targeted friction for zero depth sessions while letting normal navigation pass without friction. See examples in healthcare cybersecurity and fraud.
The shift to digital prescriptions and bot pressure points are discussed in the shift to digital prescriptions are we secure and operational considerations for paper free medicine are at paper-free medicine transforming care.
The shift to digital prescriptions and bot pressure points are discussed in the shift to digital prescriptions are we secure and operational considerations for paper free medicine are at paper-free medicine transforming care.
Diversion shows up as address hubs and repeated pharmacy pair co fills. CrossClassify builds patient to address networks and co fill heat maps, then alerts on emerging hubs before losses scale. Read more at healthcare cybersecurity and fraud.
Tactics that exploit vulnerable patients are summarized at how scammers exploit vulnerable patients and adaptive scoring principles that help isolate rings are at continuous adaptive risk and trust assessment.
Tactics that exploit vulnerable patients are summarized at how scammers exploit vulnerable patients and adaptive scoring principles that help isolate rings are at continuous adaptive risk and trust assessment.
Look for review bursts from new accounts and IPs that post across many profiles. CrossClassify correlates creation cohort signals with IP to profile networks and throttles postings when patterns spike. Guidance is in healthcare cybersecurity and fraud.
Patterns that separate real users from fake account factories are covered in avoid fake accounts and the broader new account threat is detailed at new account fraud.
Patterns that separate real users from fake account factories are covered in avoid fake accounts and the broader new account threat is detailed at new account fraud.
Scripted sessions have identical short durations and early cancellations. CrossClassify monitors behavioral biometrics and timing features to flag or block payments for obviously scripted sessions. Approach summarized at healthcare cybersecurity and fraud.
How timing and interaction rhythms distinguish humans from bots is explained in behavioral biometrics and sector level risks to tele-digital care are outlined in cybersecurity threats in healthcare.
How timing and interaction rhythms distinguish humans from bots is explained in behavioral biometrics and sector level risks to tele-digital care are outlined in cybersecurity threats in healthcare.
Synchronized timestamps and missing hour bands are persuasive evidence. CrossClassify produces user by hour heat maps and missing log indicators that are easy to export for investigations. Evidence practices are discussed in healthcare cybersecurity and fraud.
Why WAF or MFA alone do not catch post-login tampering is examined at uncover the threats WAF and MFA miss.
Why WAF or MFA alone do not catch post-login tampering is examined at uncover the threats WAF and MFA miss.
Expired authorizations and recycled PDF fingerprints are common. CrossClassify computes document hashes, validates expiry windows, and stops submissions that match known bad hashes. Implementation notes appear in healthcare cybersecurity and fraud.
See how device and document fingerprinting reinforce each other to reduce fraud at intake in device fingerprinting and a plain-language walkthrough of fingerprinting mechanics at how does fingerprinting work.
See how device and document fingerprinting reinforce each other to reduce fraud at intake in device fingerprinting and a plain-language walkthrough of fingerprinting mechanics at how does fingerprinting work.
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
