Cybersecurity for Mining
Spot Mining Fraud Before it Disrupts Operations
Track user behavior and device fingerprints beyond login screens

Stats on Mining Breaches
$0.5T
Global Cybercrime Cost
The annual global cost of cybercrime is projected to reach $10.5 trillion, with digital transformation increasing exposure.
$0.0M
Mining Breach Cost
The average cost of a data breach for mining firms is $5.1 million, highlighting the high financial impact on operators.
53%
Identity Verification Concerns
Poor identity verification is a top concern for mining IT leaders, reflecting authentication challenges in the field.
Why Mining Data Security Matters
Account Takeover Threats Target Remote Mine Access Points
Mining companies rely heavily on remote access tools, exposing them to account takeover attacks that compromise operations. CrossClassify detects and blocks unauthorized access attempts across distributed environments.
Bot Attacks Exploit Mining Portals and Dashboards
Automated bots can overload mining management systems, simulate fake access requests, and steal sensitive data. Our real-time bot fraud detection for mining software neutralizes these threats at the source
Complex Supply Chains Attract Fake Contractor Accounts
The mining industry’s extensive contractor and vendor networks are vulnerable to fake account creation and abuse. Our solution ensures secure user onboarding for mining contractors, blocking synthetic identities and fraud rings.
High-Value Operations Make Mines Prime Cyber Targets
With billions in equipment and mineral assets, mining is a high-reward target for cybercriminals. CrossClassify protects against fraud in smart mining operations through advanced identity profiling and risk scoring.
Blog
Latest from Cross Classify
Solution
Issues We Resolve
We protect your app from the most prevalent cyber attacks
Stop Account Takeover in Remote Mine Operations
Protects mining dashboards and ERP from credential abuse.
71%
Of mining companies reported disruptive cyberattacks recently.
+55%
Of mining executives lack confidence in their current cyber defenses.
How We Prevent Account Takeover
Prevent identity theft and data breaches caused by unauthorized access to user accounts. Account Takeover (ATO) attacks exploit vulnerabilities using tactics like impersonation, keylogging, smishing and phishing, and session hijacking, putting sensitive information and trust at risk.
Learn More ❯Continuous Monitoring in Mining Environments
Real-time fraud detection is essential in modern mining operations, where remote access to SCADA, fleet management, and drilling control systems is common. CrossClassify enables continuous fraud monitoring for mining infrastructure, proactively identifying suspicious activity across user sessions. Whether it’s unauthorized access to geological models or unusual login behavior from control room terminals, mining operations stay protected 24/7.
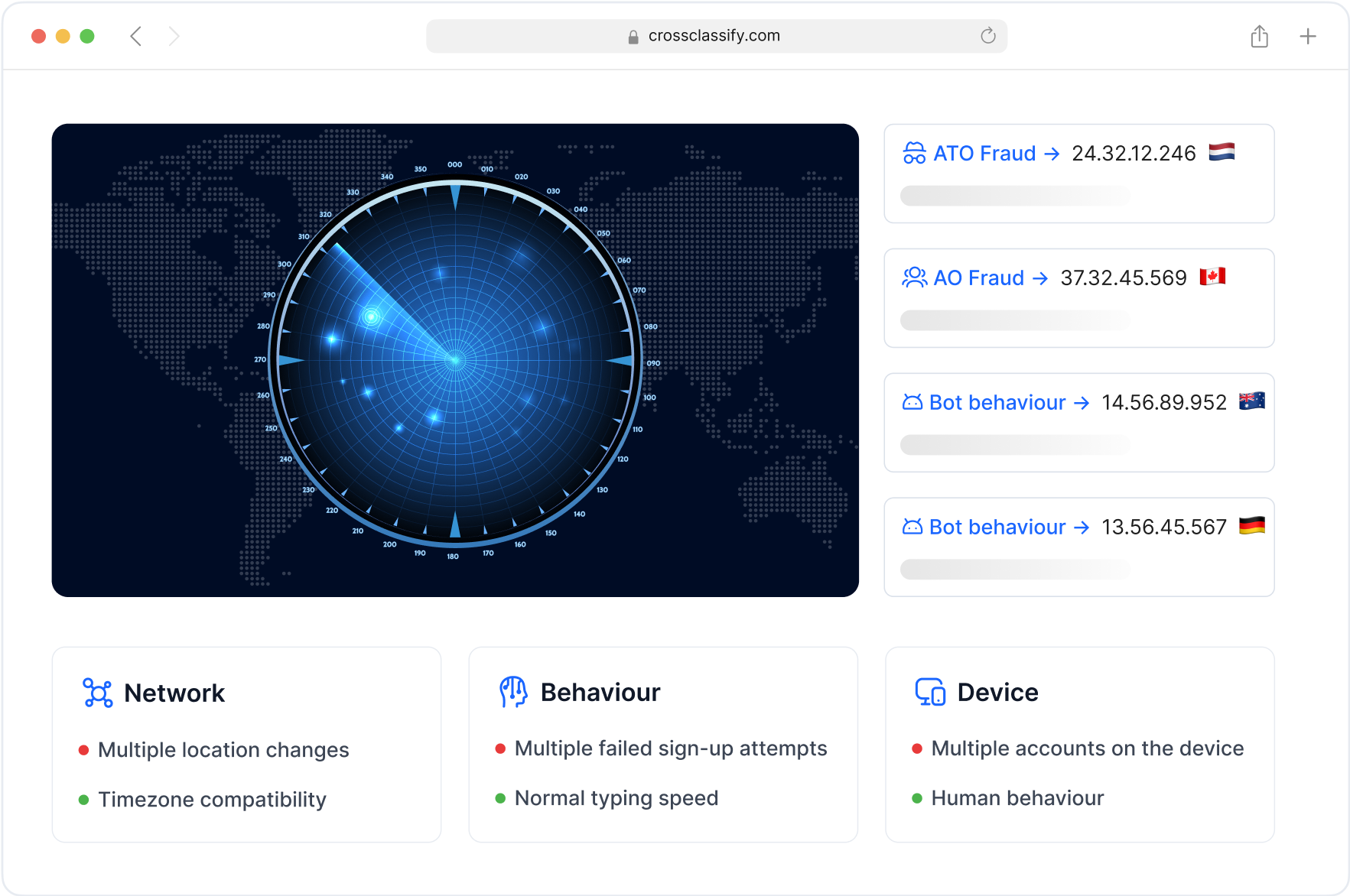
Behavior Analysis for Mining Access Control
Operators, engineers, and contractors often use shared devices or log in from rugged field environments. CrossClassify's behavioral analysis for mining personnel access detects anomalies based on how users interact with critical mining systems, such as time anomalies in blasting schedules or abnormal navigation through pit monitoring dashboards. It helps distinguish legitimate usage from potential fraud, even post-login.
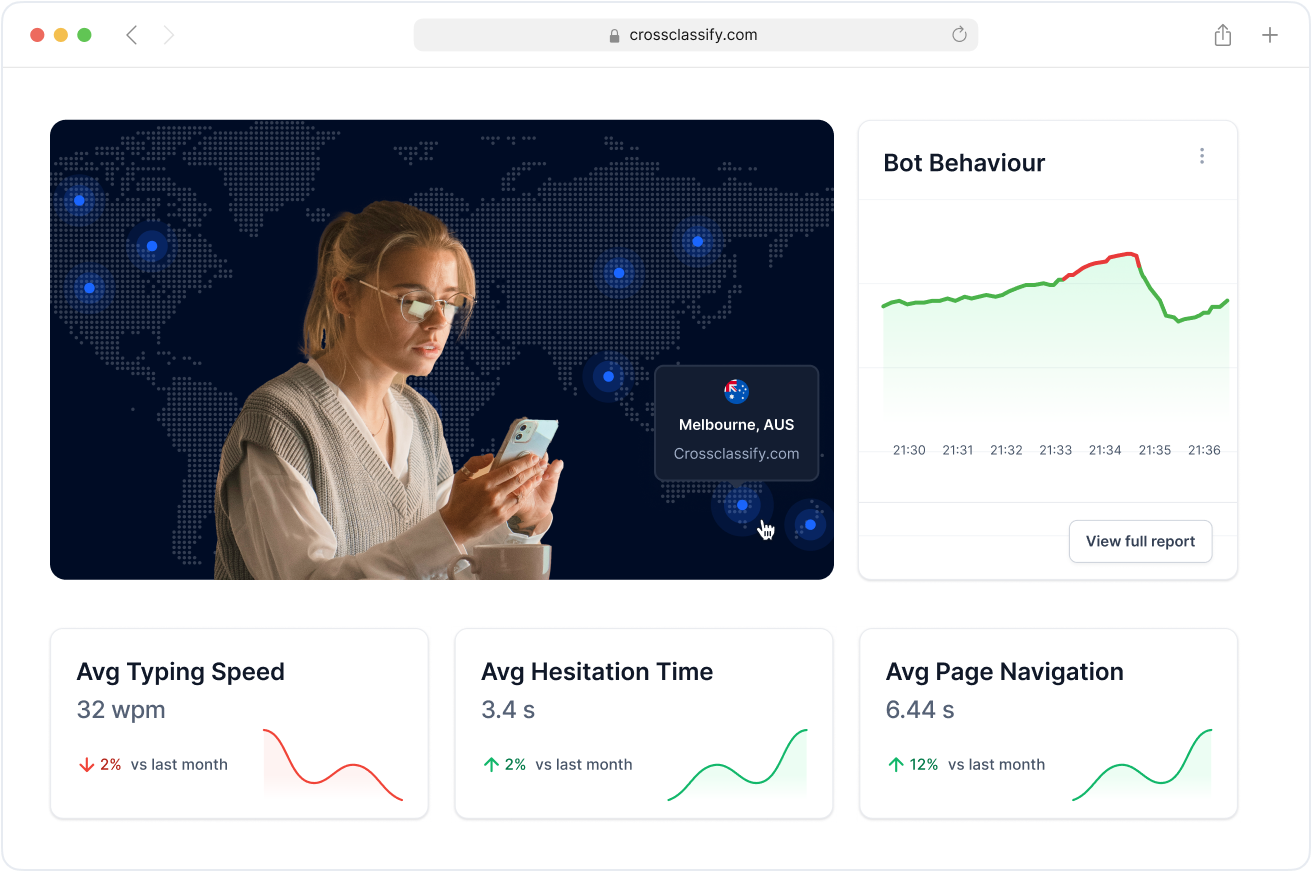
Geo Analysis Across Mining Zones
Mining operations often span across large geographical areas, including open-pit zones, underground shafts, and remote exploration camps. CrossClassify applies geo analysis for mining access control, flagging inconsistent geolocations like sudden logins from unauthorized regions or shifts in contractor device behavior between zones.
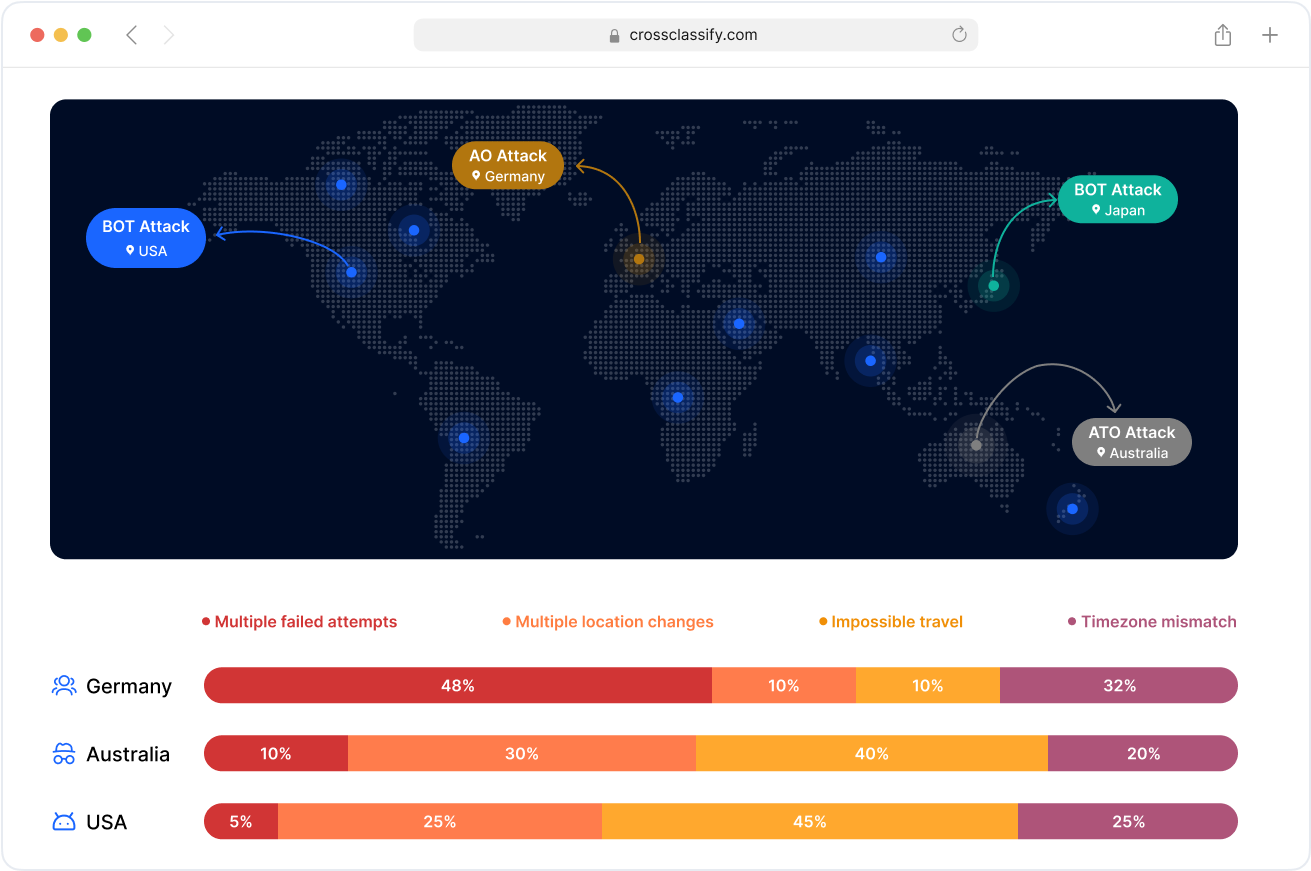
Link Analysis of Mining User Accounts
CrossClassify uses link analysis for mining account fraud detection to uncover connections between fraudulent user accounts, shared IPs, and compromised contractor credentials. This is vital in mining sites where user credentials are frequently shared among shifts, making traditional login security insufficient.
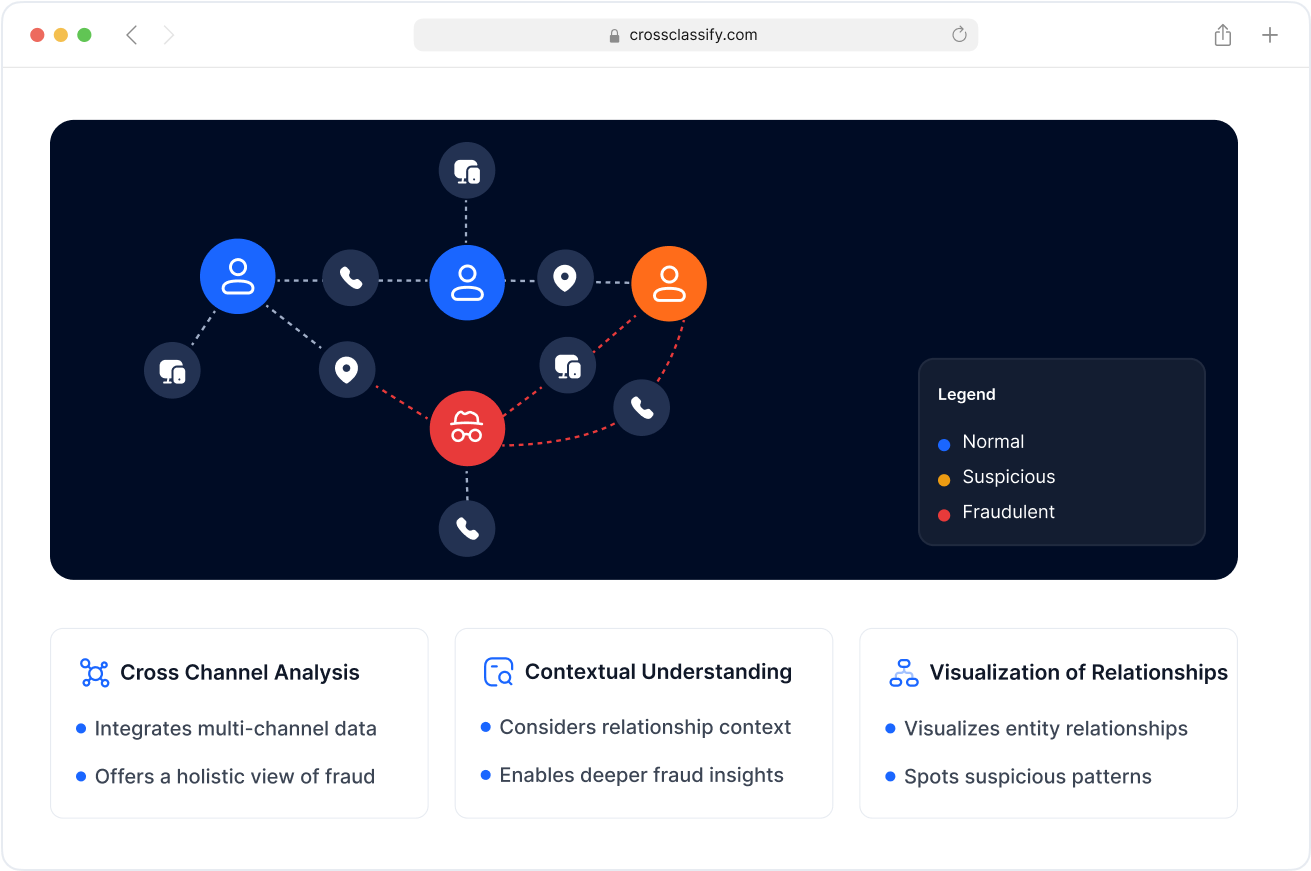
Enhanced Security and Accuracy in Mining Operations
Our intelligent models provide accurate fraud detection in mining platforms by combining device profiling, risk scoring, and contextual behavior. This ensures your mine’s SCADA systems, contractor portals, and fleet scheduling tools remain secure from credential stuffing, session hijacking, and post-login threats.
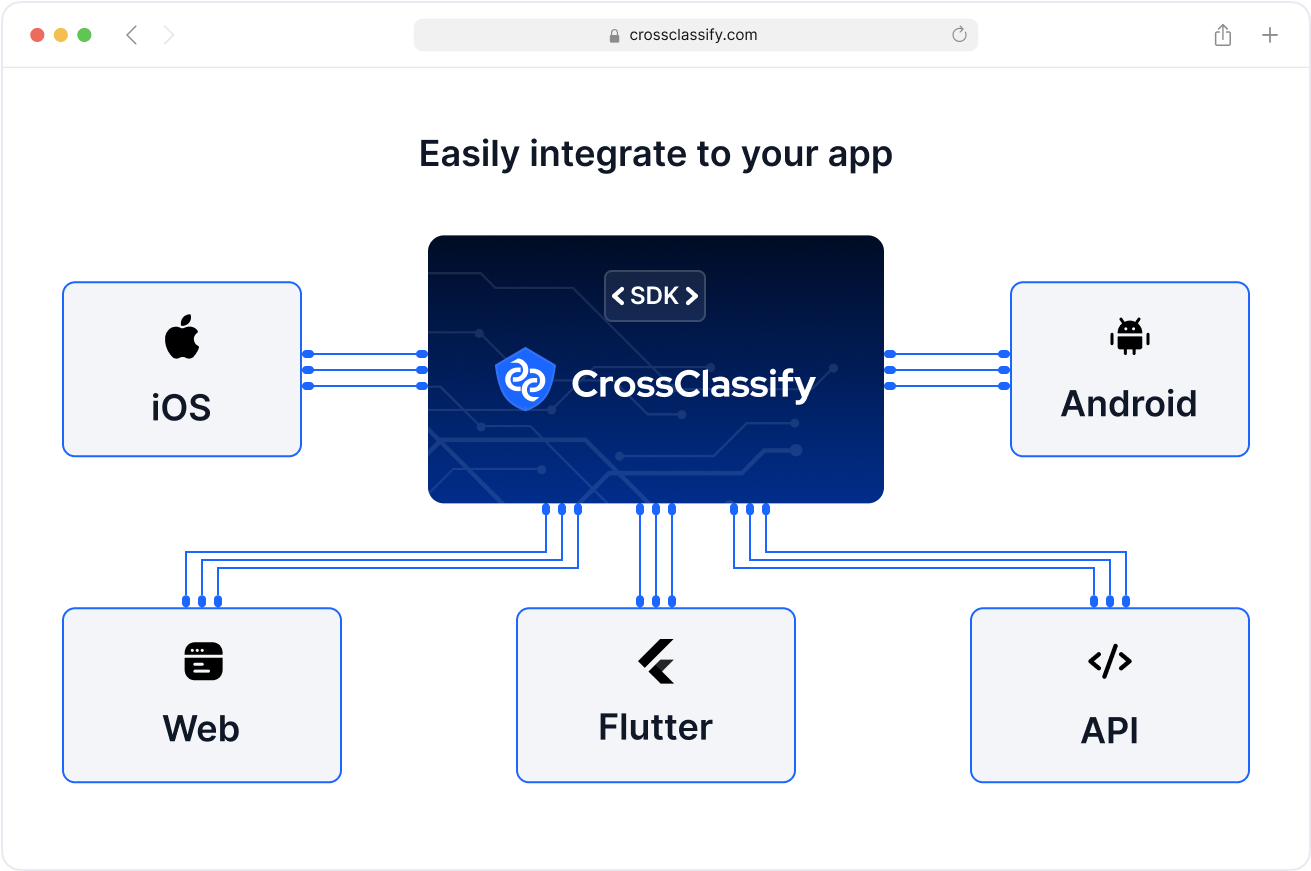
Seamless Integration with Mining IT Systems
CrossClassify integrates effortlessly with your existing mining ERP, fleet management, and access control systems via APIs and SDKs. Whether you’re managing digital twins or automated drilling software, our solution adapts to your existing architecture without disrupting operations.
Alerting and Notification for Mine Security Events
Receive real-time alerts for fraud attempts in mining user portals, including fake identity creation, unusual activity across shifts, or sudden risk score spikes during high-value operations like blasting or ore weighing. Stay informed and act fast before fraud escalates.
Compliance
From Compliance to Credibility
MSHA – Mine Safety and Health Administration
MSHA inspections identified 253 violations across 14 U.S. mines.
Warrior Met Coal fined over $150,000 for repeated ventilation violations in Alabama mines.
Red Dog Mine (Alaska) cited for multiple safety breaches, totaling $130,000 in penalties
EPA – Environmental Protection Agency Mining Regulations
Teck Resources fined $2.2M for polluting the Columbia River.
Cadia Holdings fined $350,000 over illegal dust emissions in New South Wales.
Hecla Mining Company agreed to a $143M settlement for historic water contamination.
Built for Mining Digitization
Mining operations are embracing automation, cloud platforms, and remote systems. We protect every digital touchpoint—logins, SCADA access, contractor portals—with continuous monitoring that evolves alongside your transformation strategy.
Mining-Specific Risk Models
Unlike generic fraud tools, our models are calibrated to mining data flows, access roles, and workflows. We understand the difference between a site engineer and a logistics operator—and treat them differently.
Behavior-First Detection Engine
Instead of relying on rules or blacklists, our platform learns from how miners, engineers, and suppliers behave. It flags bots, impersonators, and insiders based on intent—not IP addresses.
Frequently asked questions
Read more
Read more
Read more
Read more
Read more
Read more
Read more
Read more
Read more
Read more
Let's Get Started
Elevate your mining app's security with CrossClassify. Schedule a personalized demo to see how we protect customer accounts and ensure compliance with industry standards.