13 Feb 2025
Redefine Identity Protection in Cybersecurity
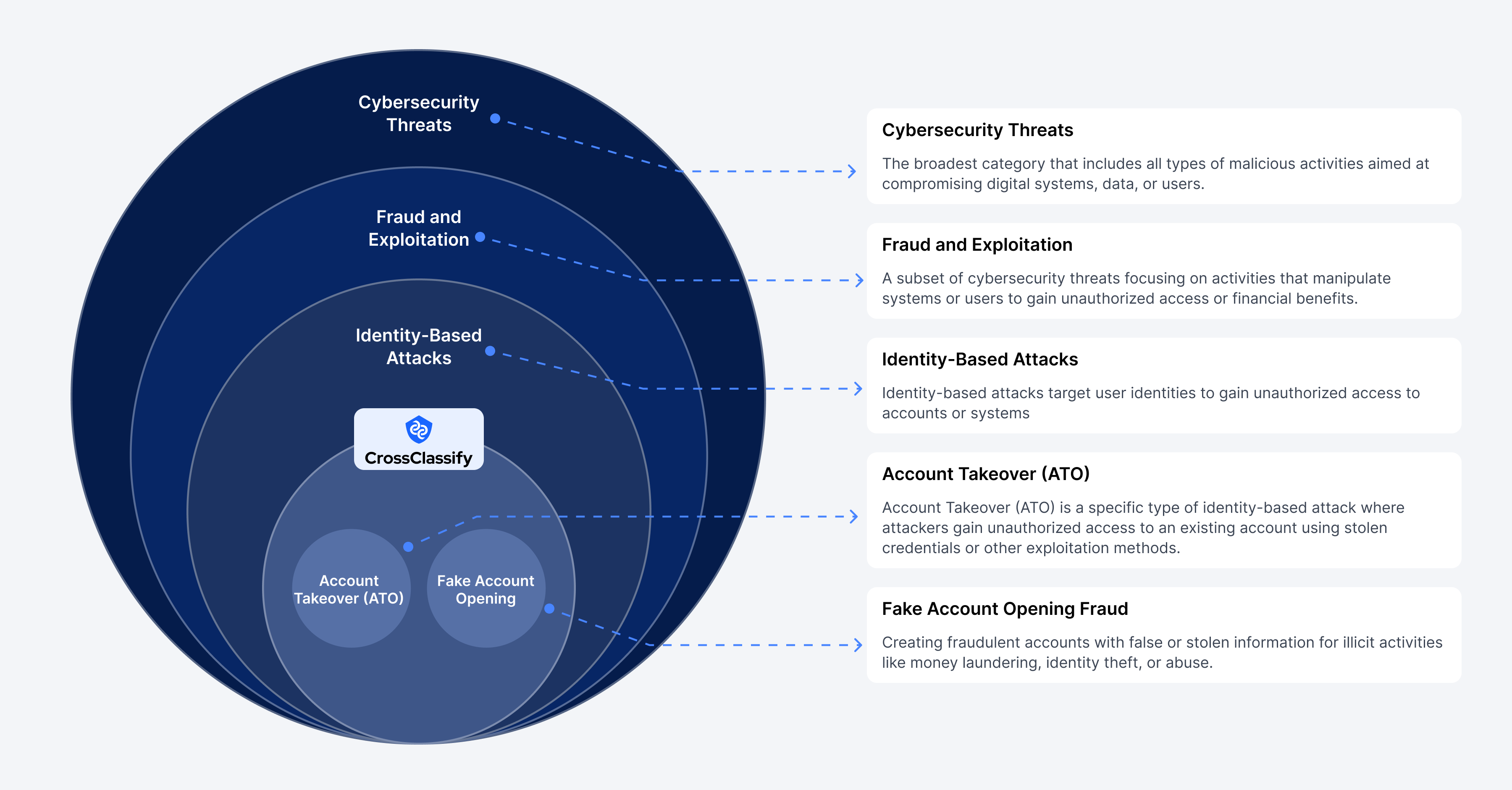
Preventing account takeovers and identity fraud before they happen. Cybersecurity is a multi-layered battlefield, where threats evolve and adapt at an alarming rate. From nation-state attacks to financial fraud, businesses today face an ever-growing range of risks. At the highest level, cybersecurity threats encompass everything from malware and ransomware to phishing and social engineering. As attackers refine their tactics, organizations must implement proactive security measures to mitigate risks before they escalate into breaches. One critical subset of cybersecurity is Fraud and Exploitation, which targets weaknesses in applications, APIs, and authentication systems. Web and mobile applications, often the primary access points for users, are highly vulnerable to exploits such as credential stuffing, session hijacking, and man-in-the-middle attacks. These vulnerabilities allow attackers to manipulate systems, steal data, or gain unauthorized access, leading to financial losses and reputational damage for businesses.
Within fraud and exploitation lies Identity-Based Attacks, a domain where CrossClassify (CC) operates as a leader in protection. Identity threats, such as Account Takeover (ATO) and Fake Account Opening (AO), are two of the most prevalent and damaging forms of fraud today. Attackers compromise legitimate accounts or create synthetic identities to exploit systems, bypassing traditional security measures. CrossClassify leverages AI-powered behavioral analysis and device fingerprinting to detect and block these threats in real-time, ensuring businesses stay ahead of identity fraud. In a world where digital identities are constantly under attack, proactive defense is no longer optional—it's a necessity.
Explore our advanced identity protection solutions: Account Takeover Protection, Account Opening Fraud Prevention, and Behavioral Biometrics. Learn more about identity fraud prevention in our articles: The Anatomy of Account Takeover and Fraud and Identity Theft.
