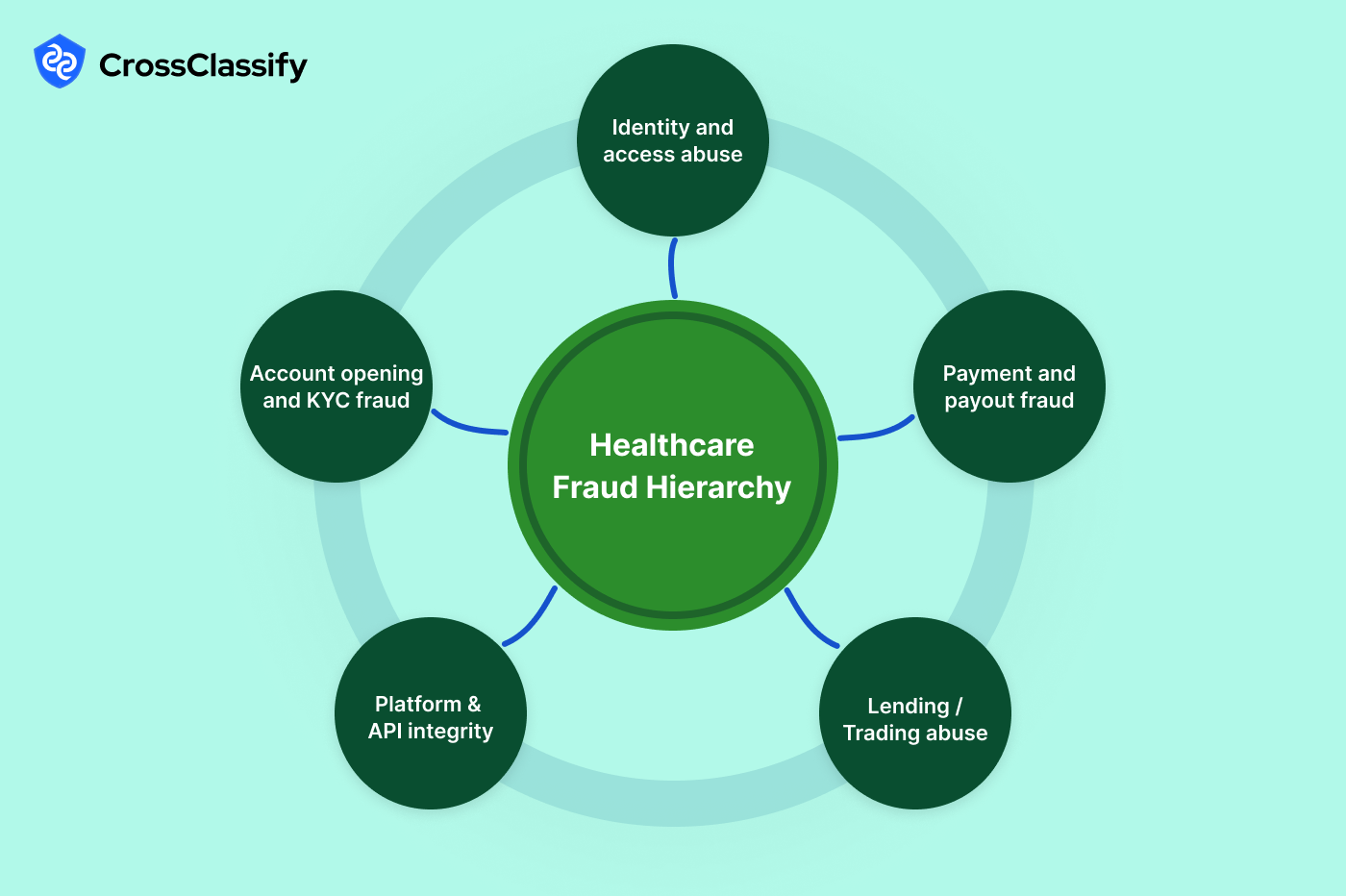
Cybersecurity for Healthcare
Protect patient data from healthcare fraud and access abuse
Detect insider threats and account takeovers across EHR systems instantly

Stats on Healthcare Breaches
82%
Healthcare Cyberattacks
Most healthcare organizations experienced a cyberattack recently, with the most expensive incident costing over $4.7 million
180M
UnitedHealth Breach
Millions were affected in the UnitedHealth-Change Healthcare breach; the incident cost UnitedHealth approximately $3.09 billion in response-related expenses.
$0.0M
Healthcare Data Breach Cost
Average cost of a healthcare data breach; per-record cost averages $408, nearly 3x the global average.
Why Healthcare Data Security Matters
Healthcare data is a top target for cybercriminals
Medical records, patient identities, and insurance data are worth more than financial info on the black market. Without real-time healthcare fraud detection, attackers exploit gaps in session monitoring and identity validation.
Account takeover in EHR systems is rising fast
Threat actors bypass login defenses and access EHR platforms, manipulating patient records and extracting sensitive health data. Traditional login-based security can’t prevent post-login fraud, you need behavioral analysis and session-level visibility.
Healthcare bots and fake accounts inflate billing fraud
Bad actors use automation to open fake patient profiles, schedule appointments, or submit fraudulent claims. A robust bot detection and account opening fraud prevention solution is critical to cut operational waste.
Insider threats drive costly HIPAA violations
Many breaches come from internal misuse of healthcare systems by overprivileged staff or third parties. Only continuous monitoring and risk scoring can detect this abuse before sensitive data is exposed.
Blog
Latest from Cross Classify
Solution
Issues We Resolve
We protect your app from the most prevalent cyber attacks
Secure Against Healthcare Account Takeover
Reduces account takeover fraud by 60% through behavior-based, healthcare-specific login monitoring.
99%
Of U.S. hospitals were targeted by credential phishing or ATO attempts
$9.77M
Is the average cost of a healthcare ATO breach in recent years
How We Prevent Account Takeover
Prevent identity theft and data breaches caused by unauthorized access to user accounts. Account Takeover (ATO) attacks exploit vulnerabilities using tactics like impersonation, keylogging, smishing and phishing, and session hijacking, putting sensitive information and trust at risk.
Learn More ❯Continuous Monitoring for Healthcare Systems
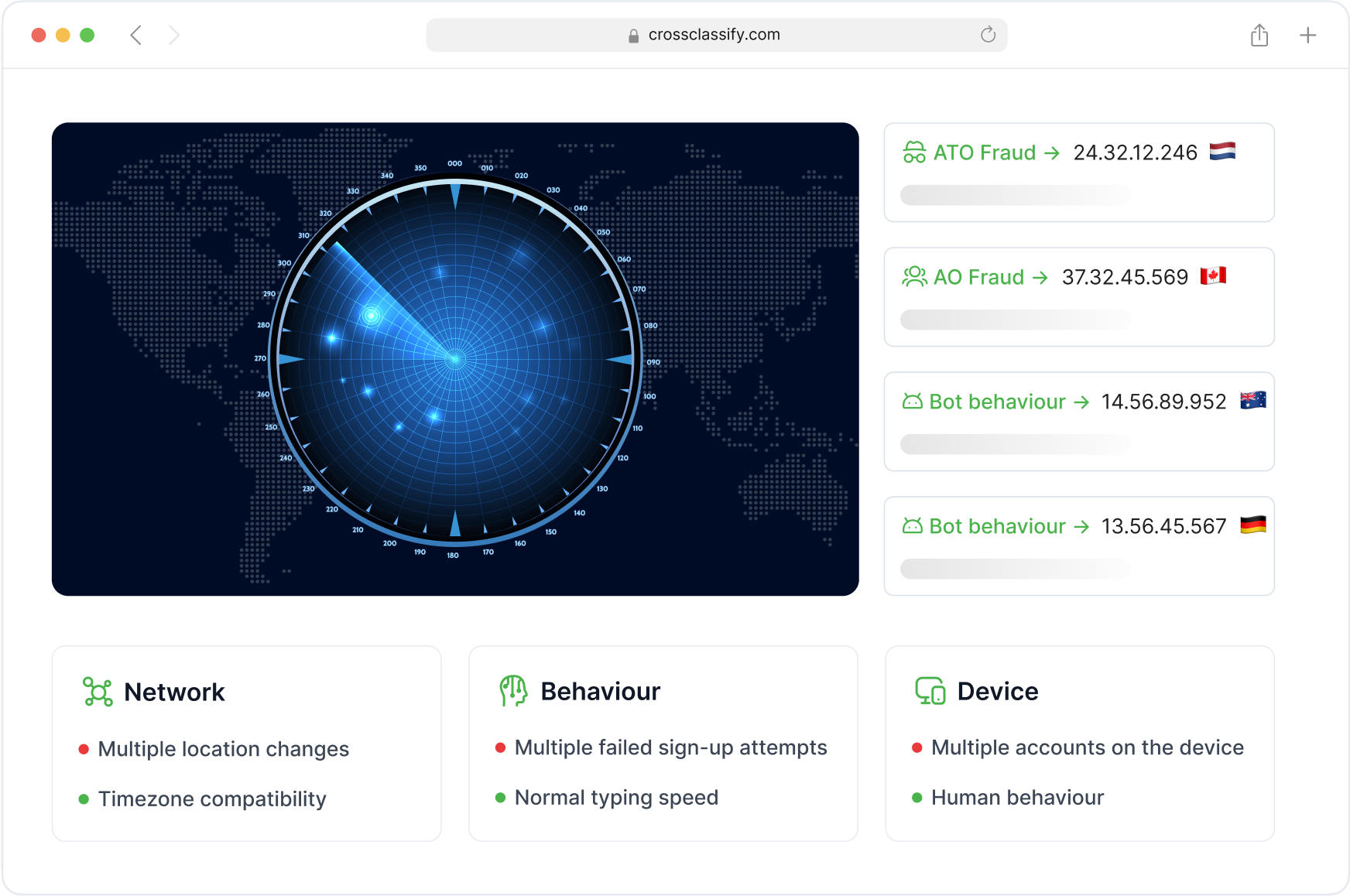
CrossClassify provides continuous monitoring across critical healthcare systems like EHR platforms, patient portals, and insurance apps. It detects anomalies throughout the session,not just at login, making it effective against post-login fraud, record tampering, and insider misuse. This proactive approach protects sensitive patient data and helps maintain compliance with regulations like HIPAA.
Behavior Analysis in Clinical Environments
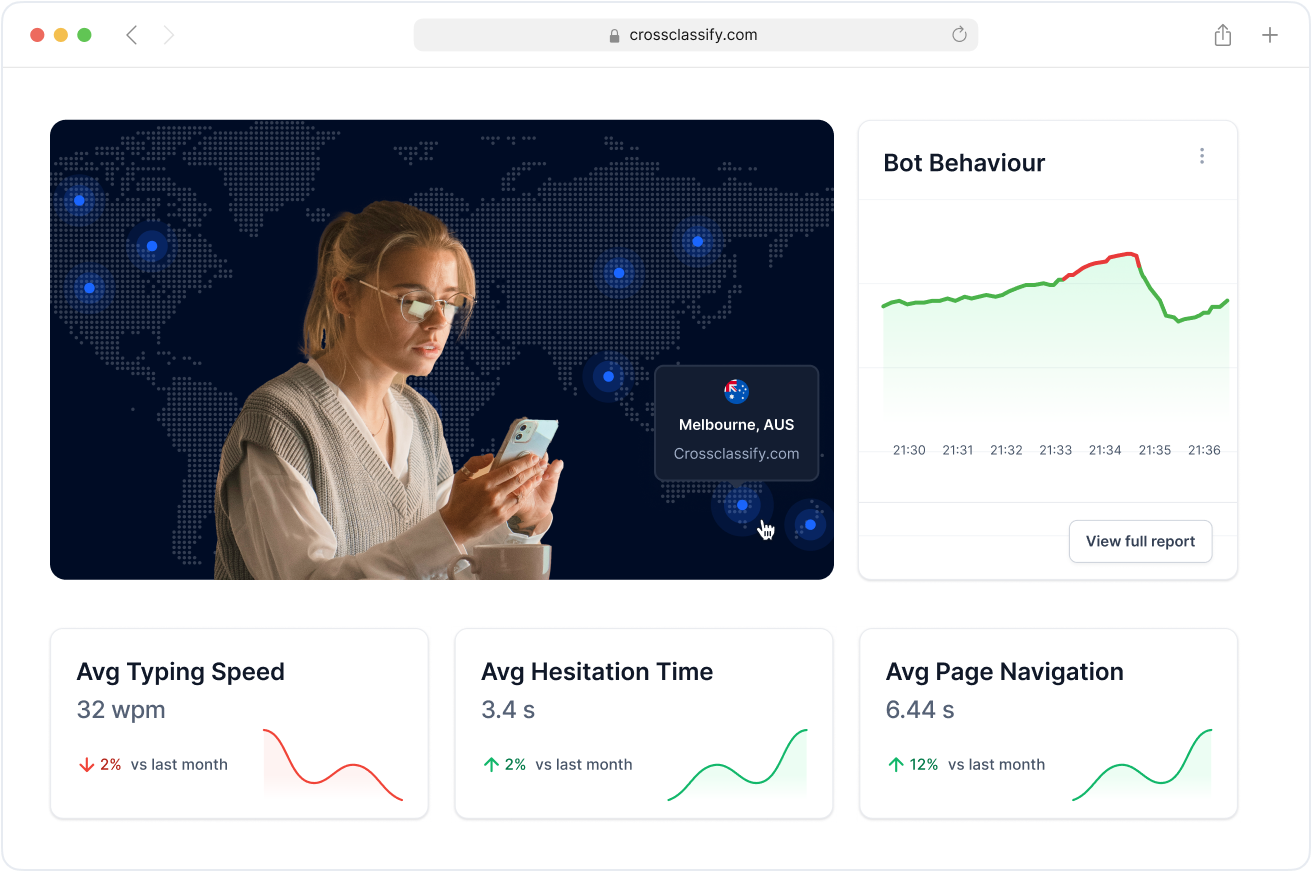
Our platform uses behavior analysis to profile how healthcare staff and patients interact with systems like EHRs, e-prescription tools, andadmin dashboards. By understanding natural patterns, we quickly detect insider threats, fraudulent behavior, and even bot-like access. This enables early intervention without disrupting care workflows.
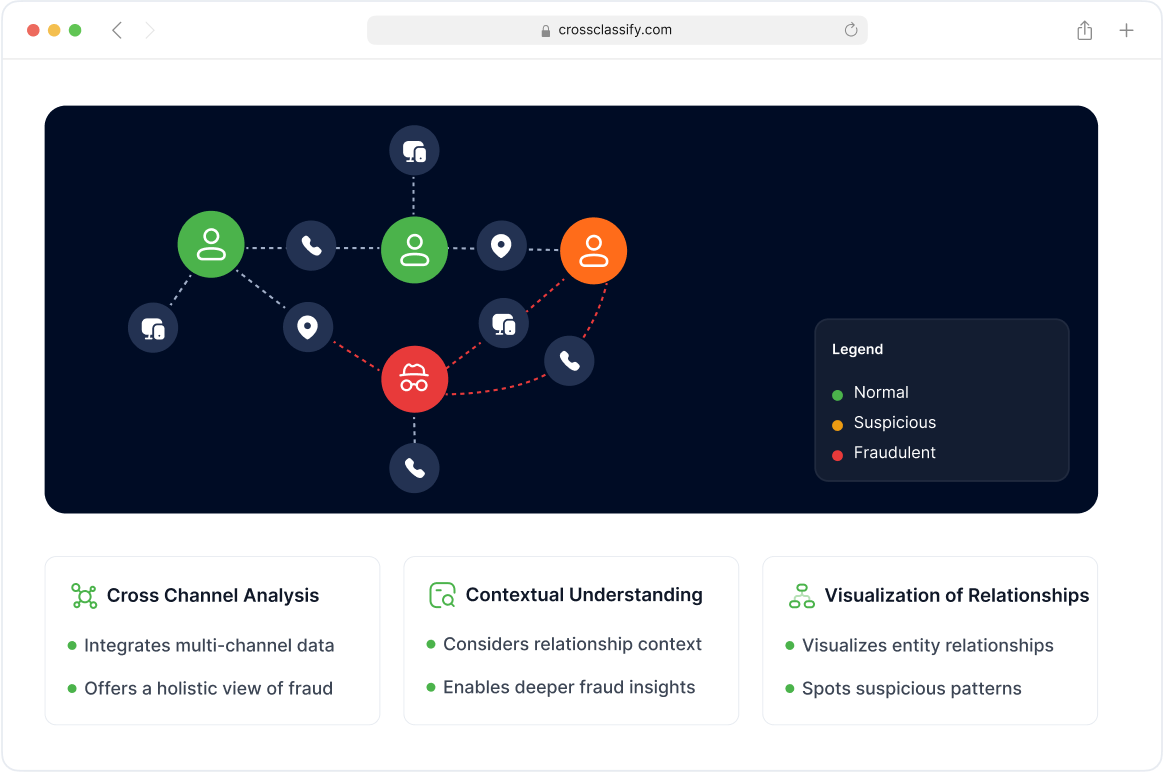
Link Analysis for Medical Fraud Rings
Our link analysis tool maps hidden relationships between fraudulent patient accounts, shared devices, and reused credentials. It detects patterns across login attempts and access behaviors that often indicate fraud networks, billing scams, or account takeover campaigns in large healthcare environments. This helps organizations break the chain of fraud early.
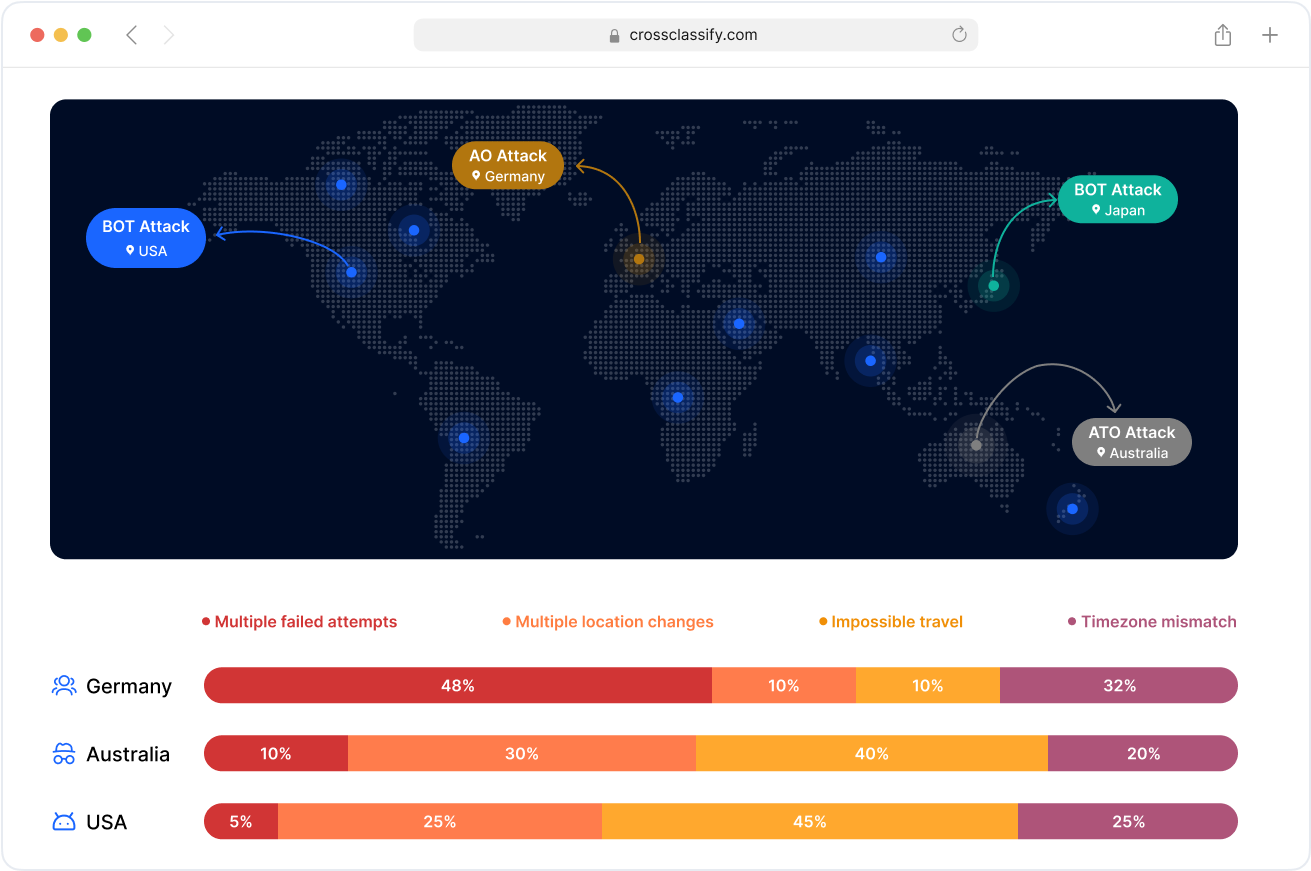
Geo Analysis of Healthcare Access Points
CrossClassify’s geo analysis feature identifies and blocks geolocation anomalies during patient or staff access events. By tracking IPs, devices, and locations, we flag suspicious logins, such as cross-border access, TOR nodes, or shared credential misuse. This helps prevent account takeover and protects systems like telehealth platforms and remote EHRs.
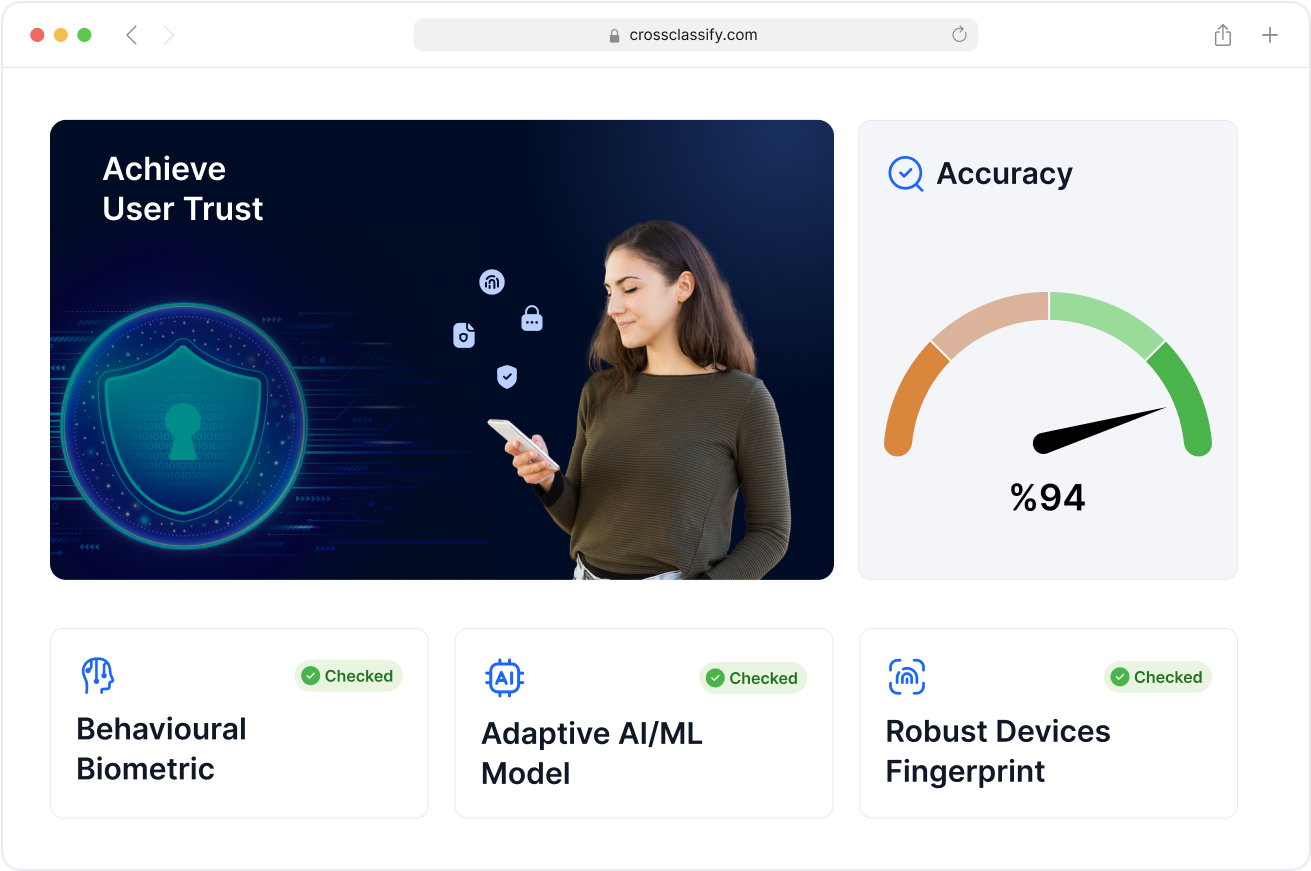
Enhanced Security and Accuracy for Healthcare
Healthcare organizations need fraud prevention tools that balance high security with operational accuracy. CrossClassify uses AI-driven risk scoring, behavioral context, and domain-specific intelligence to reduce false positives in sensitive systems like billing, insurance verification, and EHR access. This ensures patient trust and regulatory compliance remain intact.
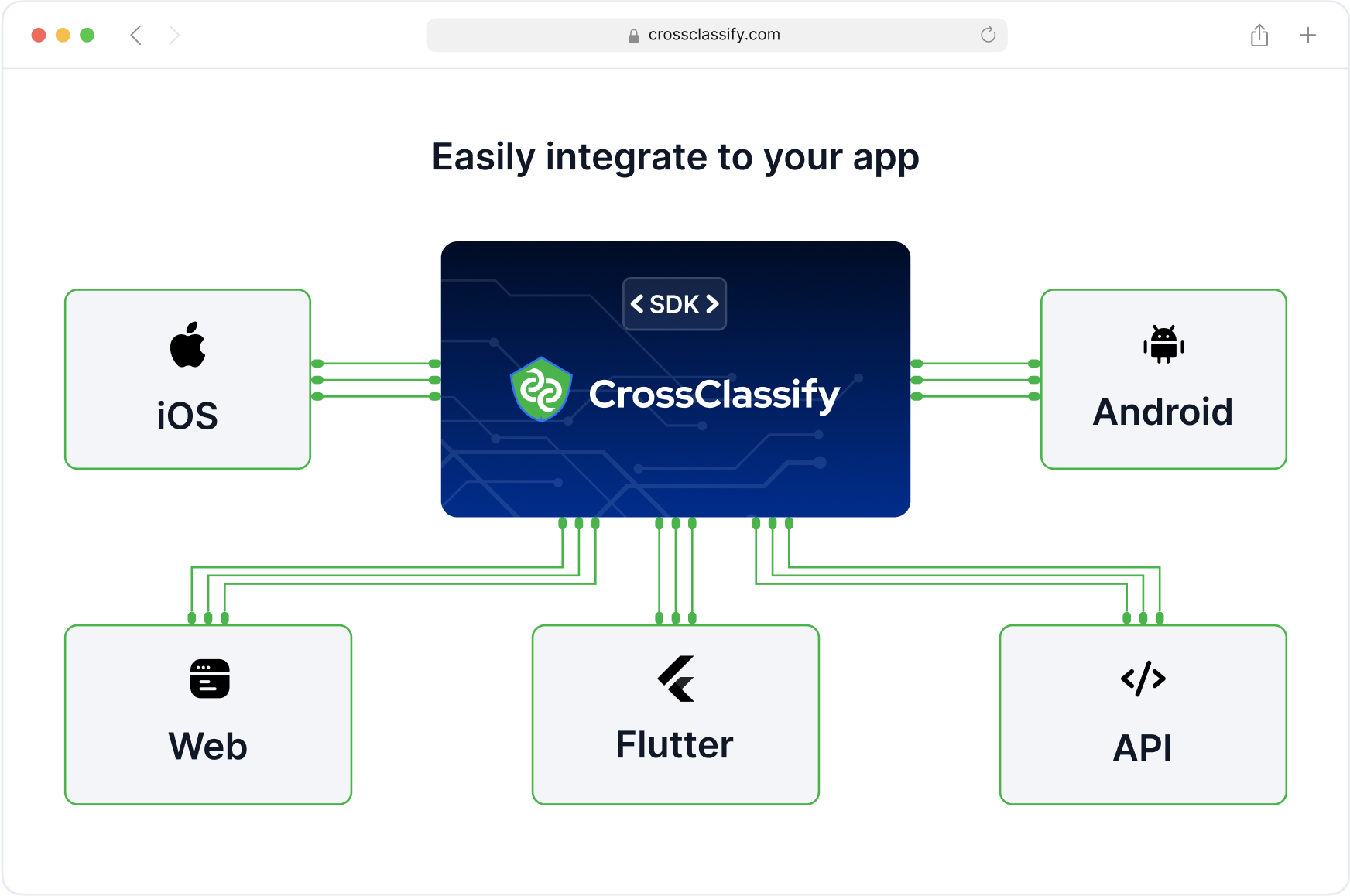
Seamless Integration with Healthcare Platforms
CrossClassify integrates easily with major EHR systems, health insurance APIs, patient portals, and telemedicine applications. Our HIPAA-compliant SDKs and APIs allow you to deploy fraud detection at login, account creation, and transactional checkpoints with minimal code. Integration takes days, not months.
Alerting and Notification for Healthcare Threats
CrossClassify’s intelligent alerting system notifies fraud and compliance teams in real time when risky activity occurs, such as unauthorized record access, abnormal billing patterns, or geolocation mismatches. Alerts can be routed to SIEMs, case management systems, or healthcare-specific dashboards for rapid response.
Compliance
From Compliance to Care
General Data Protection Regulation (GDPR)
Meta Platforms: Fined €91 million for improper storage of user passwords, contributing to a total of €2.5 billion in GDPR-related fines.
Clearview AI: The Dutch data protection authority imposed a €30.5 million fine for creating an unauthorized facial recognition database.
Health Insurance Portability and Accountability Act (HIPAA)
Warby Parker: The eyewear company agreed to a $1.5 million civil monetary penalty for alleged HIPAA violations related to unauthorized disclosures of protected health information.
Providence Medical Institute: Faced a $240,000 fine for potential HIPAA non-compliance concerning patient data security. Amazon Europe
Superior Healthcare Fraud Detection
We use adaptive real-time monitoring, behavioral biometrics, and device intelligence to catch post-login fraud and account takeover in EHR systems, where traditional tools fail to see.
HIPAA-Compliant Risk Scoring
Our risk-based authentication balances security with patient experience, designed for HIPAA-compliant healthcare apps like telehealth, patient portals, and billing systems.
Designed for Healthcare Complexity
Unlike standard fraud tools, we focus on threats like medical identity theft, telehealth abuse, and insurance fraud through behavioral analysis tuned to clinical workflows and billing patterns.
Trusted by the Australian HL7 FHIR Community and Healthcare Companies


Frequently asked questions
Let's Get Started
Elevate your Healthcare app's security with CrossClassify. Schedule a personalized demo to see how we protect customer accounts and ensure compliance with industry standards.