Stop fraud with unique device identification
Create powerful device profiles to uncover hidden threats instantly.

Solution
Device Fingerprint Issues We Resolve
Prevent fraud with accurate, real-time device intelligence.
Device Spoofing
Stop impersonated or tampered devices before they cause damage.
Returning Fraudsters
Detect users trying to re-enter after being blocked.
Synthetic Identities
Catch fraud rings operating from the same device.
Bot Attacks
Identify and block automation tools faking real user
Device Evasion
Track threats even after VPNs or cookie clearing.
Multi-Account Abuse
Reveal devices linked to mass fake account creation.
In Action
Try Cross Classify in Action
We support a wide range of device fingerprint recognition methods to quickly detect any threats to your product. Try our quick demo to see how it works — just keep in mind, the production version is even more powerful.
Want to Try Cross Classify in Action?
Our Approach to Device Fingerprint Intelligence
Detect devices, reveal fraud, protect accounts.
Device Attribute Correlation
Our device fingerprinting solution gathers and correlates multiple hardware and software attributes to build a unique device identity, resistant to evasion and spoofing.
Resilient Identity Tracking
We ensure long-term identification by tracking device fingerprints over time, maintaining recognition even after resets, VPN use, or cookie clearing.
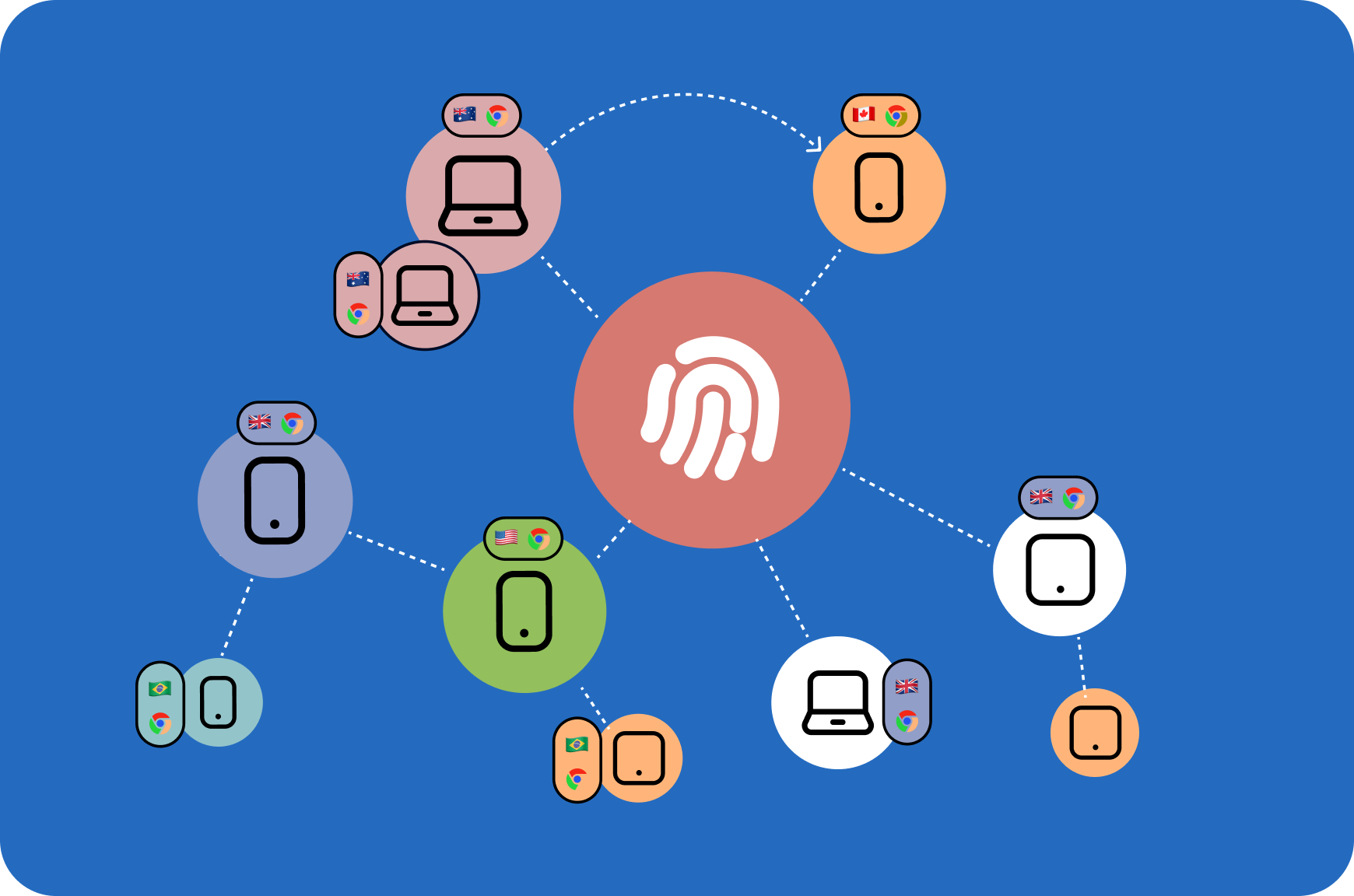
Linkage Intelligence
Linkage Intelligence connects devices through shared attributes, enabling our system to detect coordinated fraud attempts and multi-account abuse via device fingerprint analysis.
Blog
Latest from Cross Classify
Frequently asked questions
Device fingerprinting is a technique used to identify and track a device based on its unique hardware, software, browser, and network attributes—without relying on cookies. It's widely used in cybersecurity for fraud detection and user authentication.
Device fingerprinting works by collecting dozens of parameters—like screen resolution, installed fonts, OS version, browser type, timezone, and more—then combining them into a unique “fingerprint.” Even if a user clears cookies, their fingerprint remains stable.
In cybersecurity, device fingerprinting helps prevent account takeover, fake account creation, bot attacks, and fraud. It enables systems to detect anomalies, such as a login from a device never seen before or a suspicious fingerprint mimicking another user.
Common techniques include:
- Browser fingerprinting (user agent, plugins, canvas fingerprint)
- Network fingerprinting (IP, protocol behavior)
- Hardware fingerprinting (CPU, GPU, battery status),
- Behavioral fingerprinting (typing speed, mouse movement),
Yes. Device fingerprinting is especially effective against:
- Account fraud (e.g., stolen credentials used from a new device)
- Automated bot misuse
- Multi-accounting and bonus abuse By linking actions to unique fingerprints, suspicious behavior patterns become easier to catch
Absolutely. Device fingerprinting strengthens authentication by identifying familiar vs. unfamiliar devices. It’s often combined with other signals in risk-based authentication to avoid user friction while keeping fraudsters out.
A typical fingerprint might include:
- OS: Windows 11
- Browser: Chrome 125
- IP: 203.0.113.5
- Screen: 1920×1080
- Fonts: Arial, Roboto
- Combined, these details form a unique signature for that device.
Browser fingerprinting is a subset of device fingerprinting. While browser fingerprinting focuses on browser-level data (like canvas rendering or plugins), device fingerprinting also includes network, hardware, and behavioral traits for deeper analysis.
Yes, device fingerprinting works on both iOS and Android. Mobile devices expose unique parameters like device model, OS version, and network settings that contribute to a stable fingerprint, even in-app or across browsers.
CrossClassify’s fingerprinting technology, based on our academic work NADER, uses advanced AI and privacy-aware models to create highly accurate, adaptive fingerprints. It supports cross-device tracking, detects spoofed environments, and integrates seamlessly into fraud detection systems.
Let’s Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required


