Solution
BOT issues we resolve
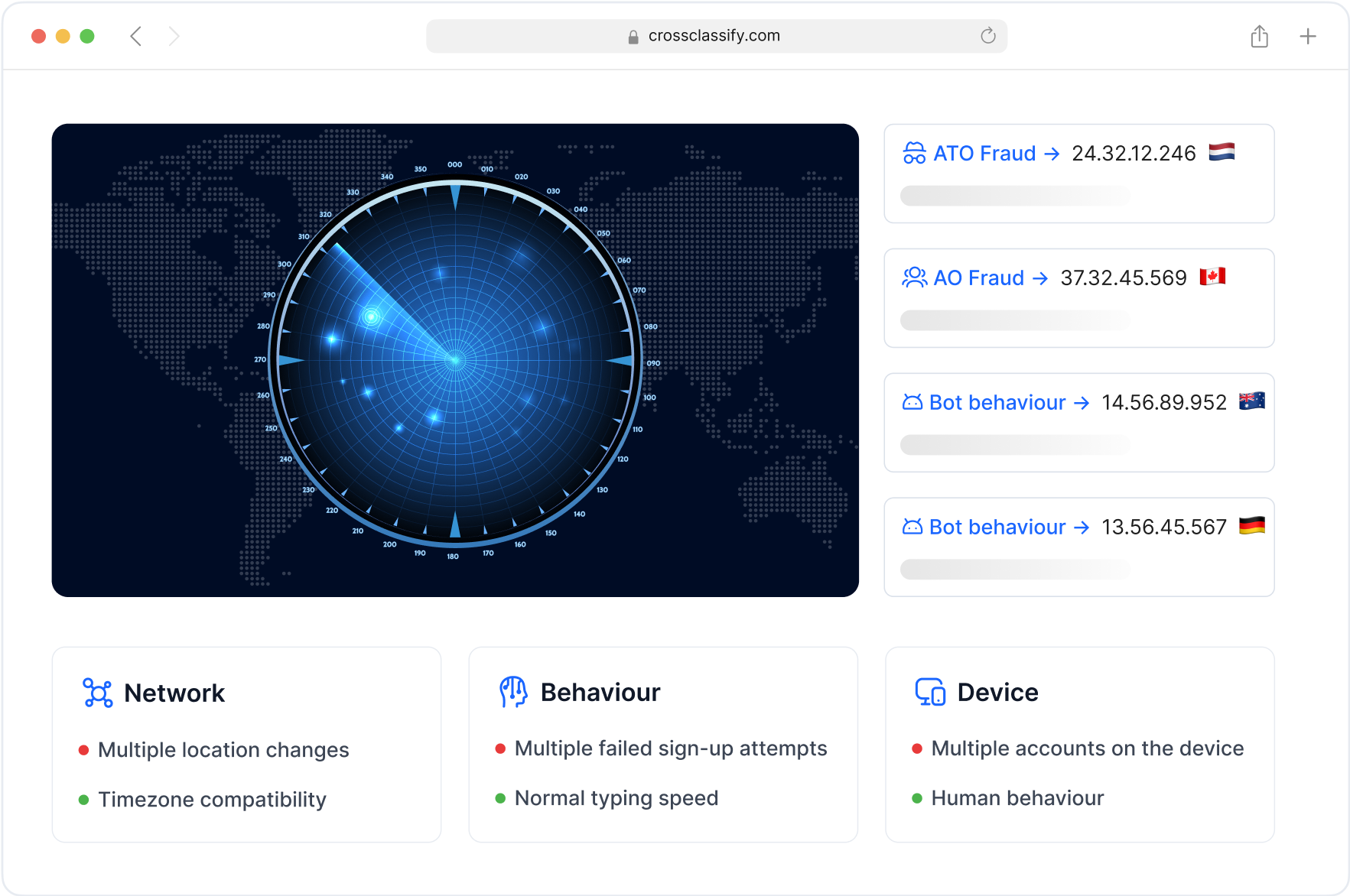
The main bot-related issues that CrossClassify’s Bot Attack Protection resolves,
Carding Attacks
Malicious bots perform automated payment fraud by testing stolen credit card details on checkout pages. These attacks can lead to chargebacks, financial losses, and increased fraud detection costs.
Web Scraping & Data Theft
Bots scrape sensitive business data, such as pricing information, product listings, and proprietary content, which competitors and malicious actors use for unfair advantages.
DDoS (Distributed Denial-of-Service) Attacks
Bot-driven DDoS attacks overwhelm servers with traffic, causing service disruptions, downtime, and financial losses. Attackers use botnets to cripple business operations.
Click Fraud & Ad Fraud
Fraudulent bots click on paid ads to drain marketing budgets and manipulate campaign performance metrics, affecting advertising ROI.
API Abuse & Automated Exploits
Bad actors deploy bots to exploit APIs, abuse promotions, or manipulate pricing systems, leading to unauthorized transactions and security loopholes.
Blog
Latest from Cross Classify
Frequently asked questions
A bot attack is when automated scripts—called bots—are used to perform repetitive tasks like credential stuffing, fake account creation, or promo abuse at scale. These attacks can disrupt services, steal data, or commit fraud.
Common bot-driven fraud types include:
- Credential stuffing (using leaked credentials to hijack accounts)
- Fake account creation (for bonuses, spam, or abuse)
- Card testing (verifying stolen card details)
- Promo and referral abuse
- Denial-of-inventory attacks in e-commerce
Signs of a bot attack include:
- Sudden spikes in traffic or sign-ups
- Repeated login failures from many IPs
- Form submissions with suspicious patterns
- High bounce rates or short session times
- Device or fingerprint anomalies
CrossClassify detects these behaviors in real time with behavioral and device intelligence.
Modern bots mimic real users by simulating mouse movements, using residential IPs, or spoofing device fingerprints. Traditional CAPTCHAs or rate-limiting often fail, especially against advanced botnets or AI-driven attacks.
Online abuse refers to malicious behavior by users—real or automated—such as:
- Spamming content or messages
- Bypassing usage limits
- Multi-accounting for exploitation
- Content scraping or API misuse
Abuse often comes from either bots or fraud farms.
CrossClassify uses:
- Device fingerprinting to detect emulators and spoofing
- Behavioral analysis to spot bot-like interaction patterns
- Velocity checks and IP intelligence
- Risk scoring to act before damage happens
it blocks both known and unknown bot behavior—without disrupting real users.
Bot and abuse fraud can lead to:
- Skewed analytics
- Wasted marketing spend
- Damaged platform reputation
- Financial loss from fake transactions
- Manual review overload
Preventing it early saves revenue and resources.
No. Some bots are legitimate (e.g., search engine crawlers). The problem lies with malicious bots used for fraud, scraping, or abuse. CrossClassify helps distinguish between good and bad bot activity.
Basic systems? Yes. But with AI-driven detection, deep fingerprinting, and behavior tracking, CrossClassify continuously adapts to evolving threats, making it significantly harder for fraudsters to stay undetected.
CrossClassify delivers all of these in a seamless, real-time solution. Best practices include:
- Implementing behavior-based detection
- Using device and browser fingerprinting
- Monitoring traffic patterns and anomalies
- Employing real-time risk scoring
- Avoiding overreliance on CAPTCHAs
CrossClassify delivers all of these in a seamless, real-time solution.
Let’s Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required