Last Updated on 07 Jul 2025
Odoo Logging Best Practices: Enhance ERP Security with Smart Monitoring
Share in

Key Notes
•
73% of businesses take an average of 207 days to detect breaches, highlighting the urgent need for proactive logging.
•
Comprehensive logging can reduce detection time from 207 days to just hours, preventing small threats from becoming major incidents.
•
Without proper logging, AI-powered tools like behavior analysis and anomaly detection fail to identify threats effectively.
Did you know that 73% of businesses are missing a critical security layer that could cut breach detection time from 207 days to just hours? This startling fact underscores the vital role of a robust logging system in today's cybersecurity landscape. What separates companies that swiftly detect attackers from those that uncover breaches months later? It’s not always expensive security tools, it’s logging. Let’s explore the cybersecurity battlefield and discover why logging could be your organization’s ultimate defense!
What is Logging?
Logging is the systematic recording of events, actions, and data related to system usage. It serves as the foundation for monitoring, auditing, and bolstering security measures. Without it, organizations lack visibility into user activities and potential threats.
Log Importance
The critical statistics speak for themselves: 73% of businesses take an average of 207 days to detect security breaches. This extended detection time transforms minor incidents into catastrophic losses. Effective logging systems can dramatically reduce this timeframe from months to mere hours, serving as the early warning system that organizations desperately need.
Logs are a fundamental data source that underpins nearly every cybersecurity defense mechanism, helping detect and defend against attacks at their earliest stages. Whether it’s User Behavior Analysis, Anomaly Detection, or Continuous Monitoring, all security algorithms depend on comprehensive log data to identify suspicious patterns and potential threats. Without proper logging, even the most sophisticated AI-driven security tools become ineffective, leaving organizations vulnerable to undetected attacks. In the cybersecurity battlefield, logs provide the intelligence needed to distinguish between normal user behavior and malicious activities, making them indispensable for proactive threat detection and response.
Log Types
Effective security logging requires capturing specific critical fields that enable comprehensive threat detection. Essential log components include timestamps for chronological analysis, user identifiers for accountability, session information for tracking user journeys, device fingerprints for identity verification, IP addresses for location tracking, browser details for environmental context, and action records for behavioral analysis. These elements form the foundation for building accurate user behavior profiles and detecting anomalies.
•
Understanding Log Sources
Logs can be collected from two primary sources: client-side and server-side. Each source provides unique insights and has distinct capabilities and limitations.
Client-side logging refers to data collection that occurs directly on the user's device, typically through JavaScript in web browsers or native applications. This approach captures device-specific information such as screen resolution, timezone, browser capabilities, and user interaction patterns. Client-side logging excels at gathering detailed user experience data and device characteristics that are not readily available to the server.
Server-side logging involves data collection that happens on the hosting infrastructure when processing user requests. This method captures network-related information, request patterns, response times, and system-level events. Server-side logging is particularly effective for tracking user sessions, monitoring system performance, and analyzing traffic patterns.
•
Internet-Dependent Log Enrichment
Certain log enhancements require external internet services and cannot be collected in isolated on-premise environments. These include IP geolocation services that convert IP addresses to geographic locations (country, city, latitude/longitude), VPN and proxy detection services that identify anonymized traffic, threat intelligence feeds that provide real-time security context, and device reputation services that assess the trustworthiness of connecting devices. On-premise installations without internet access miss these enrichments, limiting their ability to perform comprehensive geographic and threat analysis.
Client vs. Server Log Comparison
| Feature | Client | Server | Requires External Services | Collectable Without Internet |
|---|---|---|---|---|
| Device model | Yes | Partially (via user agent) | No | Yes |
| Device type | Yes | Partially (via user agent) | No | Yes |
| Device browser | Yes | Yes (via user agent) | No | Yes |
| Device timezone | Yes | No | No | Yes |
| Datetime (of request) | Yes | Yes | No | Yes |
| Username | Yes | Yes | No | Yes |
| IP Location | No | Yes (via IP geolocation) | Yes | No |
| Country | No | Yes | Yes | No |
| City | No | Yes | Yes | No |
| Lat, Long | No | Yes | Yes | No |
| Is VPN | No | Partially (with tools) | Yes | No |
| Is Proxy | No | Partially (with tools) | Yes | No |
| Page form name | Yes | Yes | No | Yes |
| Device resolution | Yes | No | No | Yes |
| Device cookie | Yes | Yes | No | Yes |
This table summarizes the capabilities of client-side versus server-side logging, highlighting which data sources require external services and which can be collected in offline environments.
Log Monitoring: Suspicious Behavior Detection Solutions
Logging isn't just about data collection, it's about leveraging that data to safeguard your organization. By feeding logs into AI-driven suspicious behavior detection algorithms, businesses can proactively identify threats. These algorithms, such as User Behavior Analysis (UBA), Continuous Monitoring, and Anomaly Detection, all depend on comprehensive logging to function effectively.
Smart leaders use these game-changing approaches:
•
User Behavior Analysis (UBA): Monitors user interactions, learns normal patterns, and flags deviations, like unusual clicks or navigation.•
Continuous Monitoring: Provides 24/7 surveillance, ensuring threats don't slip through during off-hours.•
Anomaly Detection: Uses AI to spot unusual patterns in log data, like a sudden spike in activity.
These methods rely on high-quality log data to operate. Without it, even the most advanced AI tools are powerless.
How AI Algorithms Use Logs
AI analyzes logs through three key detection methods:
•
Pattern-based Detection: Spots anomalies in interactions like page navigation or clicks, all of which are gathered with comprehensive logging.•
Time-based Detection: Identifies impossible travel or odd access times using timestamps, if stored during logging.•
Count-based Detection: Detects spikes in login attempts or session data, which can be found by defining a time-window on the user’s logs.
Logs must include timestamps, device fingerprints, account details, IP addresses, browser info, and session data to build user behavior profiles and detect anomalies.
Odoo Logging Solutions and Third-Party Options
Odoo is a powerful ERP system, offering modules for CRM, e-commerce, accounting, and more. However, a fresh Odoo instance may lack a built-in comprehensive logging module for user behavior and security monitoring. Third-party solutions include:
| Module | Advantages | Limitations |
|---|---|---|
| AuditLog (Free) | Ideal for development and testing | Lacks robust security monitoring |
| Advanced Session Management | Tracks user sessions | Limited behavioral logging; no automatic decision or analysis |
| CS Login Audit Log | Monitors login attempts | Restricted to logins; no automatic decision or behavior analysis |
These enhance logging but may not fully support advanced security or automated responses.
Robust logging is vital across all ERP systems, not just Odoo. Without it, organizations miss fraudulent activities, increasing vulnerability. Many third-party services collect data but lack behavior analysis for proactive threat detection.
CrossClassify: Advanced Behavior Analysis and Fraud Detection Platform
CrossClassify is an online service that gathers client-side data via an SDK, extracting features from behavioral logs and historical data without code changes. It uses AI-driven anomaly detection to distinguish normal from suspicious behaviors. While ideal for online services, many Odoo users rely on on-premise instances without internet access. CrossClassify addresses this challenge with OSTA (Odoo Security Threat Analysis), a comprehensive web security tool designed specifically for on-premise Odoo environments.

OSTA: Odoo Security Threat Analysis
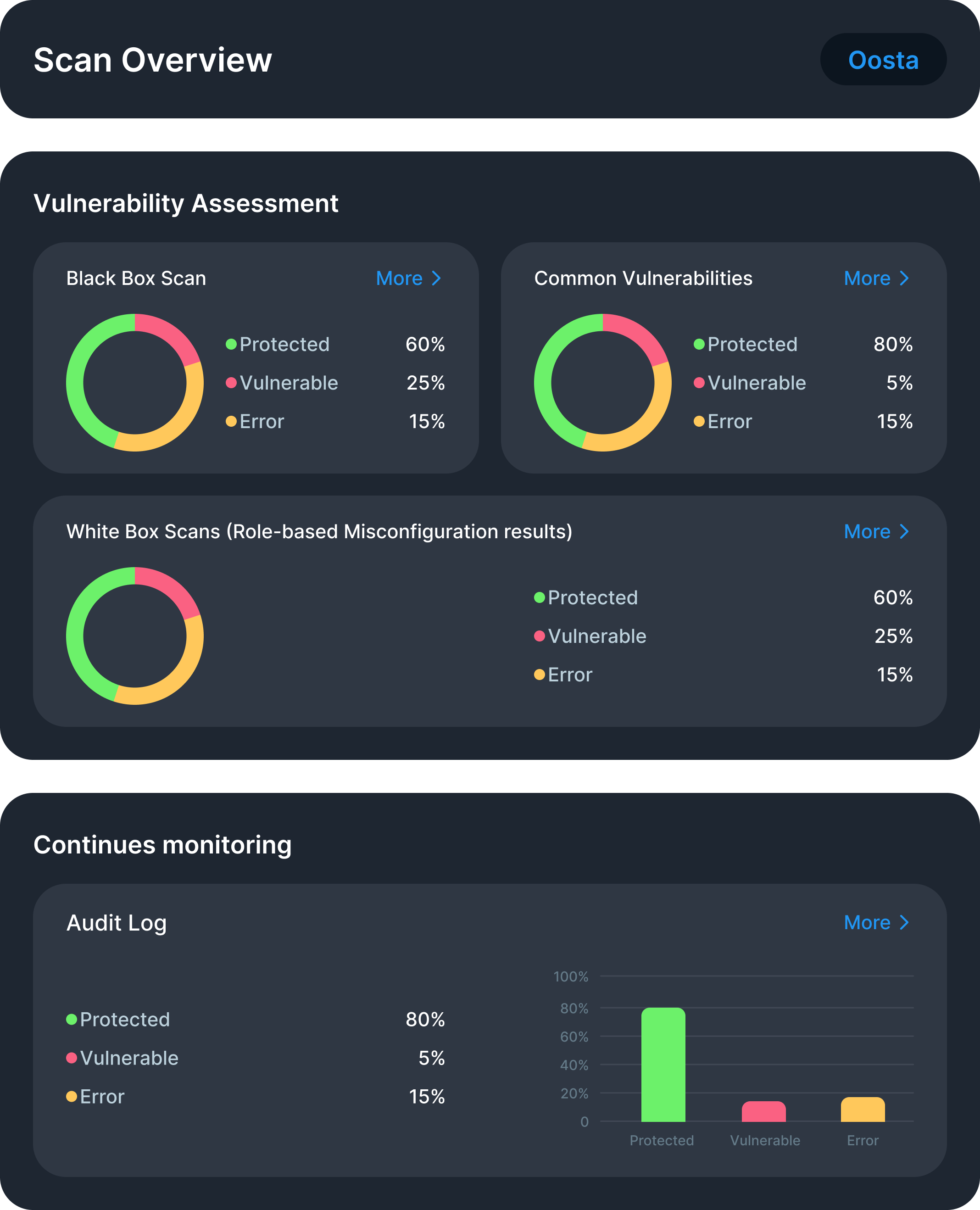
OSTA (Odoo Security Threat Analysis) is a comprehensive web security tool that provides end-to-end security protection for on-premise Odoo instances. It includes two sub‐services: first, identifying vulnerabilities through comprehensive testing; then, providing ongoing protection through automatic logging, continuous monitoring, and behavioral analysis. This integrated approach ensures security gaps are not only discovered but actively defended against in real time.
•
OSTA as Vulnerability Assessment
OSTA begins by conducting thorough vulnerability assessments of your Odoo instance. It actively simulates various attacks and security threats to determine system vulnerabilities through real‐world attack scenarios, including account takeovers, over‐privileged user exploits, endpoint weaknesses, authentication bypass attempts, and data access violations.
The vulnerability assessment process generates detailed reports highlighting specific security gaps such as weak access controls, misconfigurations, inadequate authentication mechanisms, and authorization flaws. Beyond identification, OSTA provides tailored solutions and actionable recommendations to address each discovered vulnerability. This proactive approach allows organizations to strengthen their security posture before malicious actors can exploit these weaknesses.
•
OSTA as Log Monitoring and Suspicious Activity Detector
Once vulnerabilities are identified and addressed, OSTA transforms into a continuous security monitoring system. Building on the insights gained from the vulnerability assessment phase, OSTA implements comprehensive logging mechanisms and real-time behavioral analysis to protect against the specific threats identified during testing.
OSTA integrates seamlessly with your Odoo instance to collect critical security data including usernames, login attempts, session details, timestamps, form interactions, and user behavior patterns. All data is stored securely in Odoo's PostgreSQL database without impacting system performance.
The monitoring system employs AI-driven analysis that triggers on each login attempt and user session. It detects suspicious patterns such as unusual login frequencies, abnormal device access, impossible travel scenarios, and behavioral anomalies that match the vulnerability patterns identified in the assessment phase. The system uses pattern-based, count-based, and time-based detection methods to identify threats like excessive login attempts, impossible travel, and suspicious user behavior.
When suspicious activity is detected, OSTA can automatically block users (if enabled), send immediate notifications to administrators, and provide override capabilities for legitimate users. The intuitive tabular display allows administrators to monitor activities easily while maintaining complete data privacy in isolated environments.
By combining vulnerability assessment with continuous monitoring, OSTA creates a comprehensive security ecosystem that first identifies what needs protection, then actively defends against those specific threats. This makes OSTA an indispensable tool for on-premise Odoo users seeking enterprise-grade security without compromising their isolated environment requirements.
Conclusions
Logging is a cornerstone of cybersecurity, enabling detection tools to detect suspicious behavior and slash breach detection times. CrossClassify offers tailored solutions for both cloud and on-premise Odoo setups with tools like OOSTA, ensuring robust protection regardless of your environment. In the cybersecurity battlefield, logging unlocks the power of knowledge and it is the key to staying secure at all times.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
