Last Updated on 30 Sept 2025
Data Breach in Healthcare: Buyer's Guide to Reducing PHI Exposure, Breach Costs, and Compliance Risk with AI-Driven Prevention
Share in

Key Notes
•
Healthcare breach costs are still the world's highest. 2025 research shows the global average breach cost fell overall, but U.S. breach costs reached a new record. Healthcare remains the most expensive sector, with multi-million-dollar incidents driven by fines, forensics, and disruption. The HIPAA Journal•
•
Boards want prevention with fast time-to-value. Healthcare leaders now seek commercially proven solutions that combine device fingerprinting, behavioral biometrics, and continuous monitoring—exactly what CrossClassify for Healthcare delivers, with instant visibility via the Healthcare Quick-Access dashboard.
Introduction: Why Healthcare Breaches Keep Dominating Headlines
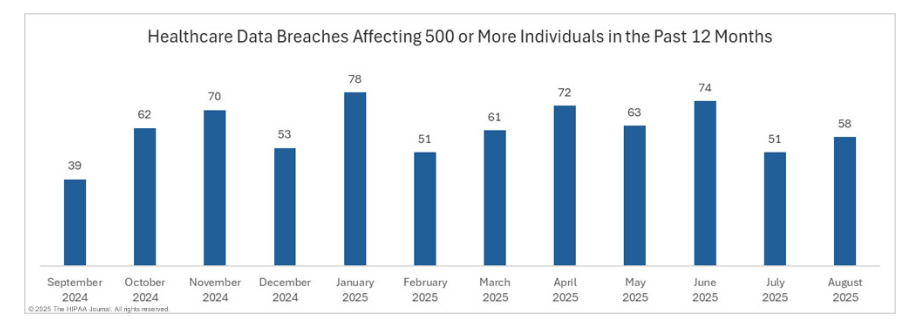
Healthcare has a perfect storm of risk: highly monetizable PHI, sprawling vendor ecosystems, and legacy tech debt. Meanwhile, regulators and plaintiffs move faster than ever. HIPAA Journal's monthly breach reports show elevated activity in 2025, with August recording 58 large breaches (500+ records) and a month-over-month uptick—evidence that volume pressure remains. For buyers, this means your "status quo" controls are no longer enough. The HIPAA Journal
Link this pressure to business outcomes: patient safety, cash-flow (claims), and compliance posture. Then compare solutions—rule-only tools vs. AI-driven fraud and abuse prevention—so you can justify investment and move quickly with a roadmap.
Link this pressure to business outcomes: patient safety, cash-flow (claims), and compliance posture. Then compare solutions—rule-only tools vs. AI-driven fraud and abuse prevention—so you can justify investment and move quickly with a roadmap.

The True Cost of Healthcare Data Breaches
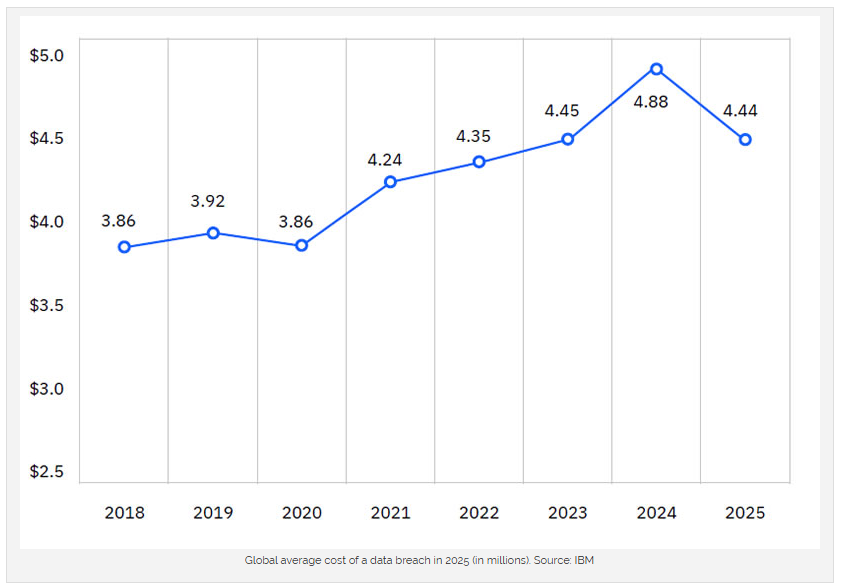
Direct and indirect cost drivers. Beyond ransom and remediation, costs balloon through regulatory fines, notification, litigation, and patient churn. Average breach costs remain highest in healthcare year after year, even as some global averages decline. U.S. figures set new records in 2025 due to higher penalties and escalation costs; healthcare is hit hardest because PHI is durable and cannot be reissued like a card number.
Operational disruption and revenue leakage. Ransomware can stall claims processing, scheduling, and billing. Even brief outages cascade into denied claims, delayed reimbursements, and clinician overtime. Downtime also triggers emergency procedures that are costlier and riskier to patient safety.
Vendor and supply-chain exposure. Business associates and third-party analytics firms present concentrated risk. One vendor breach can spill into multiple covered entities, multiplying notifications and penalties. Strong third-party risk scoring and device intelligence shrink this blast radius.
Why buyers prefer proven platforms. Point tools create siloed alerts and friction for clinicians. Providers increasingly choose integrated prevention platforms that combine device fingerprinting, behavioral biometrics, link analysis, and continuous monitoring to cut MTTD/MTTR and reduce total cost of ownership. See CrossClassify for Healthcare and our Quick-Access dashboard for a fast path to value.
For a structural overview of fraud vectors and where cost accumulates across the journey, see CrossClassify's Healthcare Fraud Hierarchy and Healthcare Cybersecurity & Fraud articles.

Operational disruption and revenue leakage. Ransomware can stall claims processing, scheduling, and billing. Even brief outages cascade into denied claims, delayed reimbursements, and clinician overtime. Downtime also triggers emergency procedures that are costlier and riskier to patient safety.
Vendor and supply-chain exposure. Business associates and third-party analytics firms present concentrated risk. One vendor breach can spill into multiple covered entities, multiplying notifications and penalties. Strong third-party risk scoring and device intelligence shrink this blast radius.
Why buyers prefer proven platforms. Point tools create siloed alerts and friction for clinicians. Providers increasingly choose integrated prevention platforms that combine device fingerprinting, behavioral biometrics, link analysis, and continuous monitoring to cut MTTD/MTTR and reduce total cost of ownership. See CrossClassify for Healthcare and our Quick-Access dashboard for a fast path to value.
For a structural overview of fraud vectors and where cost accumulates across the journey, see CrossClassify's Healthcare Fraud Hierarchy and Healthcare Cybersecurity & Fraud articles.

Real-World Examples That Shocked the Industry
Change Healthcare / UHG: ~190–193M impacted. Widely cited as the largest U.S. healthcare data theft, this attack disrupted claims and billing nationwide. It shows how a single compromise can ripple across providers, payers, and pharmacies—an archetype of systemic risk that boards now model for. Reuters
Episource: ~5.4M records. A healthcare data analytics vendor reported one of 2025's largest PHI exposures, underscoring the business-associate risk that often lies outside a provider's immediate control. Mature buyers now treat vendor telemetry as first-class signal in continuous monitoring. The HIPAA Journal
Monthly breach cadence remains high. HIPAA Journal's 2025 reports show sustained volume in large incidents. This validates a shift from reactive containment to proactive, behavior-centric prevention that detects early signs of compromise before mass exfiltration. The HIPAA Journal
Episource: ~5.4M records. A healthcare data analytics vendor reported one of 2025's largest PHI exposures, underscoring the business-associate risk that often lies outside a provider's immediate control. Mature buyers now treat vendor telemetry as first-class signal in continuous monitoring. The HIPAA Journal
Monthly breach cadence remains high. HIPAA Journal's 2025 reports show sustained volume in large incidents. This validates a shift from reactive containment to proactive, behavior-centric prevention that detects early signs of compromise before mass exfiltration. The HIPAA Journal

Why Healthcare is a Prime Target
PHI is permanently valuable. Medical histories, diagnoses, and insurance IDs enable long-tail fraud and extortion. Attackers can re-monetize PHI repeatedly, which increases expected revenue per breach for adversaries and makes your environment a priority target.
Expanding attack surface from remote and med-tech care. Telehealth, home monitoring, and connected devices improve care but multiply endpoints and identities. Without device intelligence and behavioral baselines, it is hard to tell a patient at home from an adversary on a proxy. For mitigation patterns, see Fortifying Med-Tech.
Legacy platforms and fragmented identity. Decade-old EHR modules, uneven MFA coverage, and parallel IAM systems create exploitable seams. Modern buyers consolidate risk signals—device, behavior, geo, network, and link analysis—to close these gaps.
High regulatory and reputational stakes. Healthcare combines strict laws (HIPAA, state privacy acts, GDPR for global orgs) with the human impact of care disruption. That cocktail makes the sector uniquely punitive when controls fail.

Expanding attack surface from remote and med-tech care. Telehealth, home monitoring, and connected devices improve care but multiply endpoints and identities. Without device intelligence and behavioral baselines, it is hard to tell a patient at home from an adversary on a proxy. For mitigation patterns, see Fortifying Med-Tech.
Legacy platforms and fragmented identity. Decade-old EHR modules, uneven MFA coverage, and parallel IAM systems create exploitable seams. Modern buyers consolidate risk signals—device, behavior, geo, network, and link analysis—to close these gaps.
High regulatory and reputational stakes. Healthcare combines strict laws (HIPAA, state privacy acts, GDPR for global orgs) with the human impact of care disruption. That cocktail makes the sector uniquely punitive when controls fail.

Trends and Statistics to Watch in 2025
Volume pressure persists. In August 2025 alone, 58 large breaches were reported (500+ records), a 13.7% month-over-month increase, signaling continued adversary focus and operational strain. Procurement teams should prioritize controls that reduce both breach frequency and average breach size.
Costs evolve, not vanish. While some global averages fell, U.S. breach costs rose to new highs in 2025. Healthcare remains the costliest industry, affirming that prevention platforms can have outsized ROI compared to reactive spend.
Systemic incidents reshape vendor risk policy. Massive third-party breaches (analytics, clearinghouses) push buyers to demand device fingerprinting and behavior analytics at the edge of every integration, not just core EHR access.
Costs evolve, not vanish. While some global averages fell, U.S. breach costs rose to new highs in 2025. Healthcare remains the costliest industry, affirming that prevention platforms can have outsized ROI compared to reactive spend.
Systemic incidents reshape vendor risk policy. Massive third-party breaches (analytics, clearinghouses) push buyers to demand device fingerprinting and behavior analytics at the edge of every integration, not just core EHR access.
Prevention Strategies That Actually Work
Device Fingerprinting for PHI access control. Identify risky devices by hardware/software signatures, integrity, and historical behavior, then gate sensitive workflows (portals, claims, image archives). This reduces account sharing, stops automated credential stuffing, and flags anomalous device churn early. Explore device intelligence in action with the Healthcare Quick-Access view.
Behavioral Biometrics to catch impostors in session. Keystroke dynamics, pointer paths, scroll cadence, and session rhythms are hard to fake at scale. A behavioral profile can halt fraudulent intake, portal scraping, or privilege escalation without blocking genuine clinicians. Learn more in CrossClassify's Behavioral Biometrics solution.
Continuous Monitoring and Risk Scoring. Stream device, identity, and content signals into a real-time risk score. Trigger step-up verification for medium risk, auto-block for high risk, and silently log for low risk to keep clinician UX smooth while reducing breach likelihood. See the Quick-Access dashboard for triage flows and playbooks.
Link Analysis for supply-chain and account webs. Map relationships among patients, providers, devices, IPs, and vendors to spot coordinated activity (e.g., shared devices across unrelated accounts). This is critical for vendor breaches where signals appear outside your primary domain.
Zero-Trust enforcement with contextual MFA. Move beyond static MFA. Combine device reputation + behavior + geo to step-up only when risk spikes, minimizing clinician friction while tightening control over PHI retrieval and export.
All of the above are native to CrossClassify for Healthcare, and can be operationalized quickly through the Healthcare Quick-Access interface.

Behavioral Biometrics to catch impostors in session. Keystroke dynamics, pointer paths, scroll cadence, and session rhythms are hard to fake at scale. A behavioral profile can halt fraudulent intake, portal scraping, or privilege escalation without blocking genuine clinicians. Learn more in CrossClassify's Behavioral Biometrics solution.
Continuous Monitoring and Risk Scoring. Stream device, identity, and content signals into a real-time risk score. Trigger step-up verification for medium risk, auto-block for high risk, and silently log for low risk to keep clinician UX smooth while reducing breach likelihood. See the Quick-Access dashboard for triage flows and playbooks.
Link Analysis for supply-chain and account webs. Map relationships among patients, providers, devices, IPs, and vendors to spot coordinated activity (e.g., shared devices across unrelated accounts). This is critical for vendor breaches where signals appear outside your primary domain.
Zero-Trust enforcement with contextual MFA. Move beyond static MFA. Combine device reputation + behavior + geo to step-up only when risk spikes, minimizing clinician friction while tightening control over PHI retrieval and export.
All of the above are native to CrossClassify for Healthcare, and can be operationalized quickly through the Healthcare Quick-Access interface.

Building a Future-Proof Security Posture
Unify identity, device, and behavior signals. Consolidate telemetry into one decisioning layer that scores risk in real time. This closes gaps between your EHR, patient portal, and third-party tools so attackers cannot pivot unseen.
Segment vendors and med-tech by blast radius. Not every integration needs the same trust level. Apply least-privilege access, outbound egress controls, and per-vendor device policies to limit data exposure if a partner is compromised.
Codify playbooks and automate enforcement. Pre-approve actions for specific risk scores (e.g., lock PHI export, mask SSNs, throttle API calls) so your response time is measured in seconds. Automation reduces burnout and error in your SOC and compliance teams.
Operationalize continuous assurance. Pair posture checks (patch, EDR, MDM) with behavioral drift detection to surface slow-burn compromises. Quarterly tabletop exercises with claims, billing, and clinical ops tighten your muscle memory for the next incident.
For structural guidance on where to start by risk area, review Healthcare Fraud Hierarchy and the broader Healthcare Cybersecurity & Fraud overview. If you deploy connected devices, fold in the Fortifying Med-Tech safeguards.
Segment vendors and med-tech by blast radius. Not every integration needs the same trust level. Apply least-privilege access, outbound egress controls, and per-vendor device policies to limit data exposure if a partner is compromised.
Codify playbooks and automate enforcement. Pre-approve actions for specific risk scores (e.g., lock PHI export, mask SSNs, throttle API calls) so your response time is measured in seconds. Automation reduces burnout and error in your SOC and compliance teams.
Operationalize continuous assurance. Pair posture checks (patch, EDR, MDM) with behavioral drift detection to surface slow-burn compromises. Quarterly tabletop exercises with claims, billing, and clinical ops tighten your muscle memory for the next incident.
For structural guidance on where to start by risk area, review Healthcare Fraud Hierarchy and the broader Healthcare Cybersecurity & Fraud overview. If you deploy connected devices, fold in the Fortifying Med-Tech safeguards.
Conclusion
The market signal is clear: attackers favor healthcare because PHI yields durable returns, supply chains are complex, and downtime hurts. 2025 data shows large breach volumes and record U.S. costs, with third-party incidents amplifying impact. The winning response is commercially proven prevention: device fingerprinting + behavioral biometrics + continuous monitoring + link analysis, operationalized via a quick-start dashboard and automated playbooks.
If you're ready to reduce breach likelihood and cost per incident—without slowing clinicians—start with CrossClassify for Healthcare and fast-track visibility through the Healthcare Quick-Access dashboard.
If you're ready to reduce breach likelihood and cost per incident—without slowing clinicians—start with CrossClassify for Healthcare and fast-track visibility through the Healthcare Quick-Access dashboard.
Explore CrossClassify today
Detect and prevent fraud in real time
Protect your accounts with AI-driven security
Try CrossClassify for FREE—3 months
Share in
Frequently asked questions
Healthcare mixes strict privacy rules with mission-critical workflows and vast vendor ecosystems. You must protect PHI without slowing clinicians, which is why risk-adaptive controls (device + behavior) are essential.
It recognizes known and risky devices before sensitive actions occur, stopping account sharing, automation, and risky logins. This shrinks the breach blast radius even if credentials are stolen.
MFA is necessary but not sufficient. Behavioral biometrics detects impostors during the session by modeling human interaction patterns, which is far harder for attackers to spoof at scale. See CrossClassify's Behavioral Biometrics.
Most organizations start with read-only telemetry and the Quick-Access dashboard for rapid signal coverage, then enable step-up and blocking policies over 2–4 sprints.
No. Policies are risk-adaptive. Low-risk sessions flow normally; elevated risk triggers targeted step-up. This keeps usability high while tightening PHI controls.
Yes. CrossClassify augments identity with device reputation, behavior baselines, geo/IP and link analysis, enforcing least privilege in practice. Start with CrossClassify for Healthcare.
By attaching risk scoring to devices and sessions—not just accounts—you can contain vendor incidents quickly and prove due diligence with analytics and playbooks.
Track reduced high-risk session rate, blocked PHI exports, mean time to detect/contain, and breach-related costs avoided. Given 2025's cost dynamics, prevention platforms can materially change your loss curve. The HIPAA Journal
Use Quick-Access to triage, then codify automated responses per risk tier. Export reports for HIPAA audit readiness and incident response documentation.
Review CrossClassify's Healthcare Fraud Hierarchy and Healthcare Cybersecurity & Fraud to align controls with your top fraud and breach patterns.
Let's Get Started
Discover how to secure your app against fraud using CrossClassify
No credit card required
